The cybersecurity landscape during August 4-11, 2025, witnessed a surge in critical zero-day exploitations, sophisticated ransomware campaigns, and nation-state attacks targeting critical infrastructure. Four major zero-day vulnerabilities were actively exploited in the wild, with threat actors demonstrating unprecedented speed in weaponizing newly disclosed flaws. The week’s most significant incidents included active exploitation of Citrix NetScaler (CVE-2025-6543) in the Netherlands, widespread WinRAR zero-day abuse (CVE-2025-8088) by RomCom threat actors, and continued SharePoint server compromises through ToolShell bypasses. CISA issued an emergency directive for Microsoft Exchange hybrid vulnerabilities, highlighting the escalating risk to federal infrastructure.
>>Outpace Attackers With AI-Based Automated Penetration Testing
New Hacking Techniques Emerged This Week
AI-Generated Polyglot Malware “Koske”
Overview:
Discovered on July 29, 2025, but actively deployed during the reporting period. Linux cryptomining malware utilizing polyglot JPEG images that embed C rootkit code and shell-script payloads.
Technical Explanation:
Attackers upload two JPEG polyglots via misconfigured servers. One executes as a compiled .so rootkit directly in memory, while the other drops a stealthy shell script for persistent cron-job installation. The polyglot nature allows the malware to appear as legitimate image files while containing executable code.
Impact/Risk:
Complete evasion of traditional AV and EDR solutions through fileless persistence mechanisms. The technique represents a significant evolution in steganographic malware deployment.
Takeaway for CISO:
Implement strict monitoring of JupyterLab and web-upload endpoints; enforce restrictive mime type policies for image file uploads.
QR-Abuse for FIDO Bypass (“PoisonSeed”)
Overview:
Reported July 31, 2025, with active deployment observed during the week. QR-based FIDO authentication bypass technique that lures victims into scanning attacker-controlled QR codes which silently complete genuine FIDO challenges.
Technical Explanation:
Adversaries craft malicious login session QR codes. When victims’ authenticators sign these challenges, attackers hijack the authenticated session without requiring key theft or traditional credential compromise.
Impact/Risk:
Defeats hardware-based MFA implementations and enables stealth capture of authenticated sessions, undermining zero-trust architectures.
Takeaway for CISO:
Enforce explicit user consent flows for all FIDO operations; monitor anomalous FIDO challenge origins through behavioral analytics.
Critical Attack Techniques and CVEs This Week
CVE-2025-6543: Citrix NetScaler Critical Exploitation
Date of Incident:
Exploitation discovered July 16, 2025; widespread deployment observed August 2025.
Technical Details:
Critical control flow vulnerability (CVSS 9.2) affecting NetScaler ADC configured as Gateway or AAA virtual servers. The vulnerability enables unintended control flow and denial-of-service conditions.
Attack Methodology:
- Sophisticated threat actors exploited the flaw as a zero-day since early May 2025
- Attackers deployed malicious web shells on compromised Citrix devices
- Evidence suggests attackers took deliberate steps to erase forensic traces
Impact:
Multiple critical organizations in the Netherlands compromised. NCSC-NL described this as likely work of a sophisticated state-sponsored threat actor.
Takeaway for CISO:
Immediately apply patches and run session termination commands. Deploy NCSC-NL provided IOC hunting scripts. Check for newly created privileged accounts and PHP files in system directories.
CVE-2025-8088: WinRAR Zero-Day Mass Exploitation
Date of Incident:
First observed July 18-21, 2025; continued exploitation through August 2025.
Technical Details:
Path traversal vulnerability (CVSS 8.8) in Windows WinRAR allowing arbitrary code execution through malicious archive files. Attackers craft archives with alternate data streams containing relative paths to write files outside intended directories.
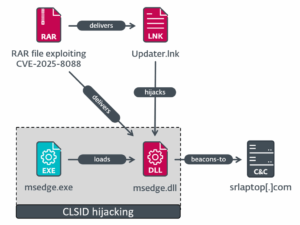
Flowchart of WinRAR CVE-2025-8088 exploitation via CLSID hijacking involving malicious RAR delivery, shortcut hijacking, DLL hijack, and C&C communication
Attack Methodology:
- RomCom threat actors used spear-phishing with job application lures
- Malicious RAR files extract DLLs to system startup directories
- Creates persistent backdoor through Windows startup folder exploitation
- Delivers multiple payloads: Mythic agent, SnipBot variant, and RustyClaw downloader
Impact:
Targeted financial, manufacturing, defense, and logistics firms across Europe and Canada. Paper Werewolf group also leveraged this vulnerability in attacks against Russian organizations.
Takeaway for CISO:
Mandatory immediate update to WinRAR 7.13. Implement email security filtering for RAR attachments. Deploy behavioral monitoring for startup folder modifications.
CVE-2025-53770 & CVE-2025-53771: SharePoint ToolShell Bypasses
Date of Incident:
Active exploitation since July 17, 2025; emergency patches released July 19, 2025.
Technical Details:
- CVE-2025-53770 (CVSS 9.8): Critical RCE through unsafe deserialization
- CVE-2025-53771 (CVSS 6.3): Spoofing vulnerability enabling authentication bypass
- These represent bypasses of previously patched CVE-2025-49704 and CVE-2025-49706
Attack Flow:
- Initial Access: Attacker posts to /_layouts/15/ToolPane.aspx?DisplayMode=Edit with forged Referer header
- Web Shell Deployment: Malicious deserialization payload plants persistent ASPX web shell
- Key Extraction: Web shell dumps ValidationKey and DecryptionKey from machineKey
- Persistent Access: Forged ViewState payloads enable stateless, unauthenticated RCE
Impact:
U.S. federal and state agencies, universities, and energy companies compromised. Storm-2603 deployed Warlock ransomware in some incidents.
Takeaway for CISO:
Apply emergency patches immediately. Rotate ASP.NET machine keys twice (before and after patching). Implement comprehensive hunting for ASPX web shells and DLL payloads.
CVE-2025-53786: Microsoft Exchange Hybrid Privilege Escalation
Date of Incident:
Disclosed August 6, 2025; CISA emergency directive issued August 7, 2025.
Technical Details:
High-severity post-authentication vulnerability (CVSS 8.0) in Exchange hybrid deployments. Allows escalation from on-premises admin to cloud environment privileges through service principal manipulation.
Attack Methodology:
- Exploits shared service principals between on-premises Exchange and Exchange Online
- Attackers forge or manipulate trusted tokens and API calls
- Privilege escalation occurs without easily detectable audit traces
Impact:
Potential for complete hybrid cloud and on-premises domain compromise. Over 28,000 internet-facing Exchange servers remain vulnerable.
Takeaway for CISO:
Apply April 2025 hotfixes immediately. Deploy dedicated Exchange hybrid app configuration. Run Microsoft Exchange Health Checker for validation. Federal agencies had until August 11, 2025, deadline.
Underground Cyber Threat Intelligence
BlackSuit Ransomware Disruption Fallout
Following U.S. HSI seizure of BlackSuit forums on July 24, 2025, affiliates migrated operations to “Chaos”-branded Tor nodes. Intelligence indicates active trading of victim datasets and custom encryption tools, with screenshots showing RSA-4096 double-encrypt negotiation panels circulating on underground forums.
Technical Developments: The disruption led to the emergence of Chaos ransomware, which appears to be a direct rebranding of BlackSuit operations. Affiliates are leveraging previously compromised infrastructure while establishing new command-and-control networks.
Medusa Ransomware Data Exchange Operations
Intelligence from August 1, 2025, revealed NASCAR staff PII and internal mapping data being traded on “BreachForums” re-emergence platforms. Affiliates offered “buy-back” decryption keys at 50% discounts, with payload breakdown diagrams showing multi-stage loader architectures communicating via Telegram bots.
Scattered Spider ESXi Campaign
Between July 27 and August 2, 2025, VMware ESXi environments faced targeted attacks using phone-based help-desk social engineering. Over 30 hypervisor encryptions were documented, with Mandiant flow diagrams depicting lateral movement from management consoles to datastore encryption.
Dark Web Credential Marketplace Surge
Check Point research revealed a 160% increase in compromised credentials available on underground forums during 2025. Threat actors are compiling credentials into “combo-lists” for account takeover attacks, with particular focus on enterprise and financial services credentials.
Ransomware-as-a-Service Evolution
Qilin Leadership: Maintained position as the most active ransomware group in July 2025 with 73 claimed victims, representing 17% of the month’s 423 total ransomware incidents.
Emerging Groups: New RaaS operations including D4RK4RMY launched dark web leak sites with innovative commission structures (50% ransom share plus base salary) and invite-only collaboration models.
Geographic Distribution: U.S. organizations remained the primary target with 223 victims in July 2025, eight times more than second-place Canada.
Technical Underground Developments
AI-Enhanced Attack Tools: Underground forums showcasing AI-generated malware development kits, with particular emphasis on polymorphic code generation and behavioral evasion techniques.
Zero-Day Marketplace Activity: The “zeroplayer” actor advertised WinRAR zero-day exploits on Exploit.in forum for $80,000 on July 7, 2025, prior to the CVE-2025-8088 disclosure.
Deepfake Service Expansion: Accenture research noted a 223% increase in deepfake-related tool trading on dark web forums between Q1 2023 and Q1 2024, with services now offering executive impersonation packages for BEC attacks.
Call to Action: FireCompass Free Demo
In this rapidly evolving threat landscape, organizations need proactive, AI-powered security assessment capabilities to stay ahead of sophisticated adversaries. The incidents documented in this report demonstrate that traditional reactive security models are insufficient against modern multi-vector attacks.
FireCompass offers cutting-edge Continuous Automated Red Teaming (CART) and AI-powered attack surface management to help organizations:
- Simulate real-world attack scenarios like the ToolShell and NetScaler exploits covered in this report
- Identify critical vulnerabilities before threat actors weaponize them
- Automate comprehensive security assessments across hybrid cloud environments
- Provide actionable intelligence on emerging attack vectors and techniques
Request your free demo today to experience how FireCompass can enhance your organization’s security posture against the advanced persistent threats documented in this intelligence briefing. Our platform’s AI-driven approach mirrors the sophistication of modern threat actors, ensuring your defenses are tested against real-world attack methodologies.
Outpace Attackers With AI-Based Automate Penetration Testing With FireCompass:
FireCompass is a single platform for AI-Powered Continuous Automated Red Teaming (CART), Pen Testing & NextGen Attack Surface Management











