SSL (Secure Sockets Layer) and its successor TLS (Transport Layer Security) are cryptographic protocols that ensure secure communication over the internet. They provide data encryption, authentication, and integrity verification to protect sensitive information transmitted between a user’s web browser and a website, or between servers. This security is crucial for online transactions, sensitive data exchange, and maintaining privacy online. Let us explore how Red Teamers can exploit SSL/TLS (Secure Sockets Layer/Transport Layer Security) vulnerabilities using tools like SSLScan and TestSSL. These tools are valuable for identifying weaknesses in SSL/TLS configurations and gaining an upper hand in Red Teaming activities.
>> Discover & Test your Ransomware Attack Surface
SSL/TLS: The Cryptographic Backbone
SSL/TLS is the cryptographic protocol that secures data transmission over the internet. It encrypts the data between the client and the server, ensuring Confidentiality, Integrity, and Authenticity. While SSL/TLS is a fundamental security technology, it’s not immune to vulnerabilities and misconfigurations. Red Teamers often capitalize on these weaknesses to infiltrate systems.
Tracing Back To Beginning
The development of secure communication protocols can be traced back to the need for secure data transmission over the internet.
SSL (Secure Sockets Layer):
SSL 1.0 was never released due to security flaws.
SSL 2.0 released in 1995, had vulnerabilities such as weak encryption and susceptibility to man-in-the-middle attacks.
SSL 3.0 released in 1996, SSL 3.0 addressed the vulnerabilities of SSL 2.0, including the POODLE vulnerability, which exploited weaknesses in the protocol’s design.
TLS (Transport Layer Security):
TLS 1.0, developed in 1999, aimed to address vulnerabilities in SSL 3.0, including the BEAST (Browser Exploit Against SSL/TLS) attack.
TLS 1.0 still had few vulnerabilities, and its use has been discouraged in favor of newer versions.
Subsequent Versions of TLS:
TLS 1.1 (2006) and TLS 1.2 (2008) addressed vulnerabilities present in TLS 1.0, providing stronger cryptographic algorithms and improved security.
TLS 1.3 (2018) further enhanced security, eliminated obsolete and insecure cryptographic algorithms, and improved the efficiency of the handshake process.
The Three – Way Handshake In SSL/TLS
Let’s first understand how does this secure connection begin? It starts with the three-way handshake:
Client Hello: The client initiates the connection by sending a “Client Hello” message to the server. This message contains information about the client’s SSL/TLS capabilities and preferences.
Server Hello: The server responds with a “Server Hello” message, selecting the most secure SSL/TLS version and cipher suite that both the client and server support. The server also sends its digital certificate, which contains its public key.
Client Key Exchange: The client acknowledges the server’s choices and generates a pre-master secret, encrypts it with the server’s public key, and sends it to the server.
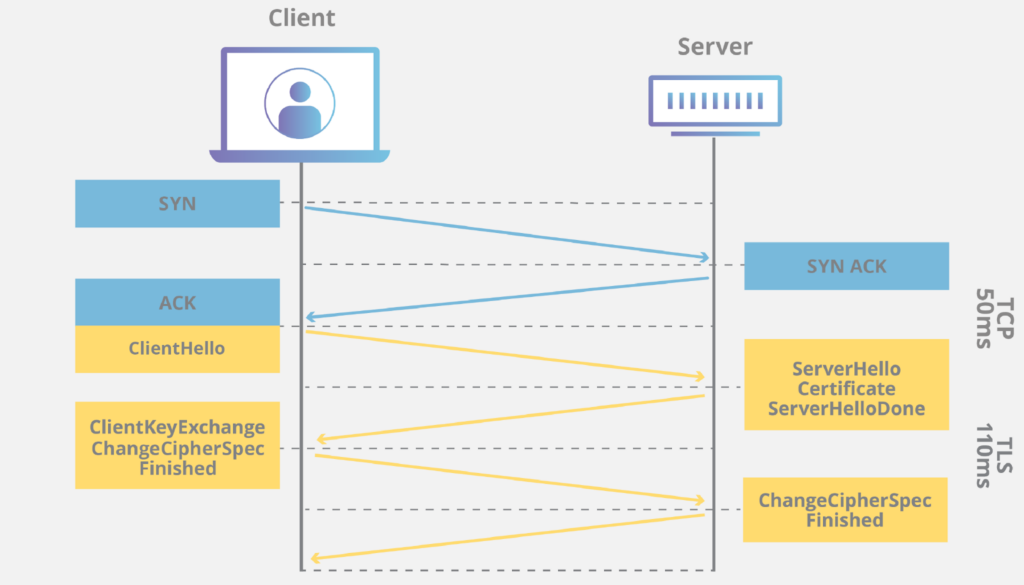
In simple way, It Is like:
x=0 —> x=0 (SYN)
x=1,y=0 <— x=0+1,y=0 (SYN,ACK)
x=1,y=0+1 —> x=1,y=1 (ACK)
With the pre-master secret, both the client and server can derive the symmetric encryption keys used for secure communication. This process ensures that the connection is not only encrypted but also authenticated. While the three-way handshake establishes a secure connection, it’s essential to recognize that SSL/TLS, like any technology, is not immune to vulnerabilities and misconfigurations.
>> [Request RECON Demo] - Reconnaissance Techniques As Threat Actors
About Encryption In Online Protection
Symmetric Encryption:
Tailored for the bulk encryption of data, this method, embodied by the Advanced Encryption Standard (AES), secures the transfer of substantial volumes of information with efficiency and speed. Following an elegant handshake, our digital protection seamlessly transitions into the realm of symmetric encryption, forming an impenetrable shield around our data.
Concept Of Key Exchange:
Here, the beauty of asymmetric encryption reveals itself. Public key cryptography, represented by cryptographic luminaries like RSA (Rivest-Shamir-Adleman) and ECC(Elliptic Curve Cryptography), orchestrates a secure exchange of keys. This intricate method ensures that the keys to our digital sanctuaries are exchanged safely, away from attackers maintaining the Integrity.
Digital Signatures:
Asymmetric encryption takes the lead, creating and verifying digital imprints that guarantee the integrity and authenticity of our data. Each digital signature acts as an secure seal, assuring users of the legitimacy of their online interactions.
Securing Communication:
Symmetric encryption protocol creates an encrypted tunnel that envelopes our data, providing a private and secure channel for information exchange. This ensures that sensitive information remains shielded throughout the Data transfer.
-> (Request Demo) 10 X Pen Testing Frequency & 100% Asset Coverage
Common Vulnerabilities Associated With SSL/TLS
A Terminology We Need To Look Into Is Padding: Padding is like preparing a message before we lock it up with a secret code. Now, this message might not fit perfectly in the box, so you add some extra stuff (the padding) to make it fit just right. Padding ensures that the message is in consistent size and shape, making it harder for someone to figure out what’s inside. Think of it as an extra layer of protection to keep your message safe and secure.
Lucky 13 Vulnerability: “Lucky 13” is a significant vulnerability in SSL/TLS that focuses on the implementation of block ciphers such as AES. This attack relies on timing variations during the encryption process to uncover the original, unencrypted data. It’s crucial for Red Teamers to understand the implications of Lucky 13 since it can result in data exposure, particularly in systems employing outdated cipher suites and padding methods. To counter the Lucky 13 threat, organizations should prioritize the adoption of up-to-date encryption standards and configurations.
Heartbleed Vulnerability: Heartbleed remains one of the most infamous SSL/TLS vulnerabilities. It affected the widely used OpenSSL library and allowed attackers to read sensitive information from the memory of a vulnerable server. Red Teamers often look for servers that are still susceptible to Heartbleed, as it provides an avenue for unauthorized access and data theft. Organizations must patch their systems promptly and replace vulnerable SSL/TLS implementations to prevent this critical vulnerability.
POODLE (Padding Oracle On Downgraded Legacy Encryption): POODLE is a security vulnerability that targets the SSLv3 protocol. It allows attackers to exploit the padding scheme in SSLv3 to decrypt and extract information from encrypted connections. While SSLv3 is considered deprecated and obsolete, it’s still supported by some servers, making them vulnerable to POODLE attacks.
BEAST (Browser Exploit Against SSL/TLS): BEAST is another SSL/TLS vulnerability that affects the security of cipher block chaining (CBC) mode ciphers in SSL/TLS. This attack allows an attacker to recover plaintext data by observing the ciphertext of an HTTPS connection. This attack is challenging to execute.
Identifying Vulnerabilities
As Red Teamers, it’s crucial to understand how to interpret SSLScan and TestSSL results effectively. Here are some key vulnerabilities we might encounter:
Weak Cipher Suites: Look for servers that support outdated, weak cipher suites like RC4 or 3DES. These can be exploited using various attacks.
SSL/TLS Protocol Version: Determine if the server supports older, less secure versions of SSL/TLS, such as SSLv2 or SSLv3. These versions are susceptible to vulnerabilities like POODLE and BEAST.
Certificate Issues: Check for expired, self-signed, or misconfigured certificates. Expired certificates can lead to insecure connections, while self-signed certificates may indicate a lack of proper authentication.
Heartbleed Vulnerability: SSLScan and TestSSL will flag servers susceptible to the Heartbleed bug, a severe vulnerability in OpenSSL.
Misconfigurations: Pay attention to configuration issues like insecure renegotiation, weak key lengths, and insecure hashing algorithms.
Conclusion
SSTI vulnerabilities are a serious concern for web application security. They can provide a foothold for attackers to manipulate your server and potentially achieve RCE. By understanding the mechanics of SSTI, and following best practices for prevention and mitigation, you can significantly reduce the risk of falling victim to this dangerous vulnerability chain.
SSTI can be identified wiith various commercial and open source tools such as Burp Suite, Owasp Zap, Netsparker etc. FireCompass integrates the best of open source and commercial tools to discover SSTI in your attack surface by integrating its Web App Vulnerability Discovery Playbooks with EASM.
>> (Learn More) "Automated Pen Testing Significantly Improved The Depth & Breadth Of Testing" - Ed Adams, Security Innovation
By: FireCompass Delivery Team – Arnab Chattopadhyay, Amit Da, Joy Sen, K Surya Sai Harsha
About FireCompass:
FireCompass is a SaaS platform for Continuous Automated Pen Testing, Red Teaming and External Attack Surface Management (EASM). FireCompass continuously indexes and monitors the deep, dark and surface webs using nation-state grade reconnaissance techniques. The platform automatically discovers an organization’s digital attack surface and launches multi-stage safe attacks, mimicking a real attacker, to help identify breach and attack paths that are otherwise missed out by conventional tools.
Feel free to get in touch with us to get a better view of your attack surface.










