We live in an era of constant cyber threats. According to Verizon report 2020, there were over 157525 cyber breach incidents in 2020, 3950 of which were confirmed data breaches. Cyber breaches are harmful occurrences that result in damages to organizations’ financial, legal, and reputational status. Cybercriminals use unsecured endpoints to breach into networks, and once inside, they move around stealing data and launching further attacks against other nodes in the network.
The sum of all known and unknown entry points that can be exploited by cybercriminals is known as an attack surface. To defend against cyber threats, therefore, organizations must seek to carry out attack surface analysis to identify and secure entry points to their networks. This process of identifying, mapping, and securing vulnerabilities to a network is referred to as attack surface reduction
Types Of Attack Surface
Primarily, three types of attack surface affect a majority of the organizations: digital, physical, and social engineering attack surface.
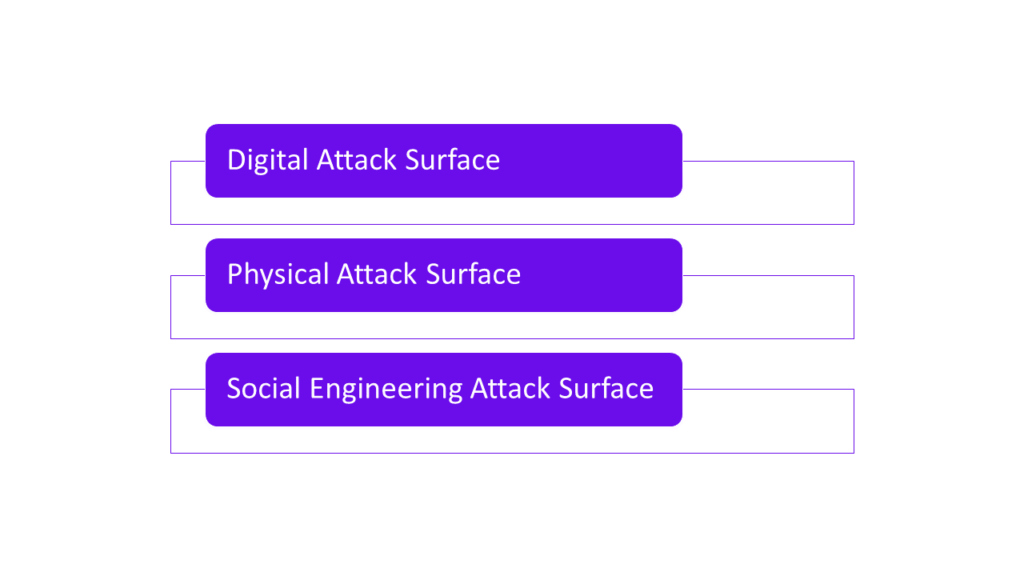
Digital Attack Surface
This comprises all digital assets that reside outside your firewall, and which can be directly accessed from the internet. Every computer and network directly connected to the internet is at risk of being hit by cyber-attacks. Digital attack surface includes domains, subdomains, software applications, networks, and ports. In other words, a digital attack surface refers to everything running on the digital side of an organization.
Digital attack surfaces are the most convenient ways through which cybercriminals gain entry into systems and networks. This convenience stems from the fact that it is easier to hack digitally than to physically break into a data center; and with a digital attack surface, cybercriminals can hit any digital asset around the globe.
Physical Attack Surface
This refers to all vulnerabilities in a system or network that an attacker can physically exploit if they gain entry into the physical location of the system or network components. These include routers and desktop computers. Once an attacker has gained entry into the physical device, he’ll attempt to exploit other devices within the network. Exploitation through the physical attack surface has been rendered complicated with the deployment of protective measures such as biometric access control systems, access control cards and door locking.
Social Engineering Attack Surface
Due to protective measures such as biometrics, cybercriminals have opted for social engineering attack surfaces. Social engineering exploits human susceptibility to manipulate people into disclosing classified information or executing actions that go against their organization’s security measures. The social attack surface is the attack surface consisting of people who can be easily manipulated through the means of social engineering.
Role Of Attack Surface In Cyber Threats
Cybercriminals exploit vulnerabilities they can identify on a network. It is therefore upon organizations to scan and analyze their systems in an attempt to identify possible vulnerable IT assets that can be exploited by cyber attackers. And due to the dynamism of attack surface, regular assessments ought to be carried out to avoid the risks associated with cyber threats.
3 Ways To Minimize Cyber Threats By Reducing Attack Surface
While securing your physical attack surface is achievable with the best security measures such as biometric, protecting your digital and social engineering attack surface may not be an easy task. These two attack surfaces require the deployment of attack surface management tools to give you an all-round view of your digital footprint.
The following are some of the ways to help reduce an organization’s attack surface.
Downgrade Exposure
Cybercriminals utilize attack surfaces to gain entry to a system or network, and the more expansive an attack surface, the more possible number of vulnerabilities, and the higher the probability a cybercriminal will be successful in their cyber-attacks. A desirable solution, therefore, is to reduce the area of exposure. This means restricting functionalities (such as ports, protocols, functions, and service), deploying multilayered defense mechanisms, and eliminating APIs that are susceptible to cyber-attacks.
Reduce Avoidable Complexity
Poor policy management or lack of data during the design stage of a system can lead to complexities that might turn into vulnerabilities in the future. A great way to reduce the attack surface of your system or network is by, therefore, removing preventable complexity.
Identify Your Vulnerabilities
One of the primary ways of reducing your attack surface is attack surface analysis. This is a process through which systems and networks are scanned for possible vulnerabilities that can be exploited by cybercriminals; after which the identified vulnerabilities are secured. Regularly carrying out this process leads to a reduced attack surface.
How To Leverage FireCompass For Attack Surface Management
Cyber-attack surface management is the best approach to identify vulnerabilities in a system or network and reduce the attack surface. By carrying out regular attack surface management, an organization can reduce the risks posed by cyber threats.
FireCompass is the only attack surface management tool that gives Information Security teams and decision-makers a comprehensive solution for detecting possible vulnerabilities in risky assets and reducing the digital attack surface in their organizations.
FireCompass continuously analyzes the internet and provides alerts on any changes or risks associated with your digital footprint. This includes new ports, risky assets, misconfigured databases, or any internet-facing infrastructure.
FireCompass helps organizations to reduce their Digital Attack Surface by:
- Identifying exposed documents & files, IoT infrastructure
- Identifying compromised / malicious infrastructure
- Identifying exposed services like APIs and RDP
- Identifying exposed personnel information including email addresses, phone numbers, etc.
Conclusion
A significant number of cyber breaches occur due to known and unknown entry points to a system or network. Not having a real-time view of your dynamic attack surface leaves an organization in the dark and increases the risk of cyber threats. This is where a complete attack surface mapping solution like Firecompass, be it known or unknown attack surface along with attack surface analysis, attack surface reduction, and management can help reduce your unknown risks significantly.
Gartner recommends security leaders start reducing, monitoring, and managing their attack surface as part of their holistic cybersecurity risk program.
If you would like to reduce your organization’s digital attack surface, simply opt for a comprehensive attack surface management solution like Firecompass.