In the ever-evolving landscape of cybersecurity, vulnerabilities continue to emerge, putting critical systems and sensitive data at risk. One such threat that has gained notoriety in recent years is the Server-Side Template Injection (SSTI) vulnerability. While SSTI on its own is a concerning issue, what makes it even more perilous is its potential to escalate into Remote Code Execution (RCE). In this blog, we will explore the mechanics of SSTI vulnerabilities, how they can lead to RCE, and best practices for mitigation.
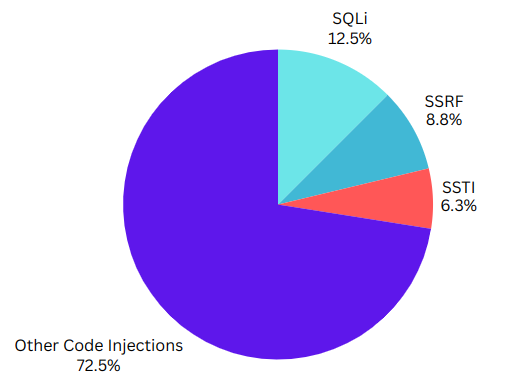
As per GitHub Advisory of vulnerabilities in commercial and Open Source products, out of all the Remote Code Execution Vulnerabilities, around 6.3% of them are Template Injection Vulnerabilities as compared to very popular 12.5% SQLi.
>> Discover & Test your Ransomware Attack Surface
What is SSTI ?
Server-side template Injection (SSTI) is a type of vulnerability that occurs when an attacker can inject malicious template code into a web application, which is subsequently executed on the server. This vulnerability arises when an application does not properly sanitize and validate user input within its templates. A template is a feature by many frameworks to create dynamic content based on provided inputs. Templates are generally processed by Template Engines. Popular template engines like Jinja2, Twig, and FreeMarker are often targeted by attackers when looking for SSTI vulnerabilities.
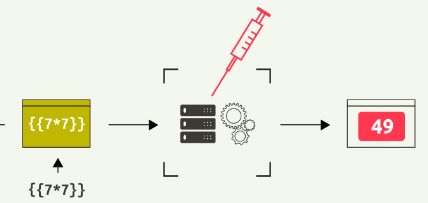
The main danger of SSTI lies in its ability to manipulate the application’s rendering and logic. By injecting arbitrary code into templates, an attacker can exploit the server’s capabilities, potentially leading to information disclosure, data manipulation, and in the worst case, remote code execution.
SSTIs can occur on both server and client sides, affecting diverse technologies. For instance, a flaw in Things Board before version 3.5 allowed attackers to exploit Apache FreeMarker, enabling Server-Side Template Injections when modifying email templates. Similarly, a critical vulnerability was discovered in OpenRapid RapidCMS 1.3.1, where manipulation of a specific argument led to SQL injection through a template file.
The Path to RCE
SSTI is an entry point for attackers, but it doesn’t always directly result in RCE. However, it can be a stepping stone towards achieving full control over the server. The path to RCE typically involves the following steps:
- Identifying SSTI: The attacker finds a vulnerable point in the application where SSTI is possible. This often requires a keen understanding of the application’s technology stack and the specific template engine in use.
- Exploiting SSTI: Once the vulnerability is identified, the attacker crafts malicious payloads and input to inject into the application. This payload is designed to manipulate the template rendering process.
- Leveraging RCE: In some cases, the attacker can escalate the SSTI vulnerability to achieve RCE. This occurs when the attacker can inject code that is executed on the server, effectively taking control of the application’s environment.
- Execution: With RCE achieved, the attacker can run arbitrary code, potentially leading to the complete compromise of the server, unauthorized access to data, and even lateral movement within the network.
>> [Request RECON Demo] - Reconnaissance Techniques As Threat Actors
Mitigation and Prevention
Preventing SSTI vulnerabilities and their potential escalation to RCE is crucial for maintaining the security of web applications. Here are some best practices to mitigate these risks:
- Input Validation: Implement strict input validation and sanitation for user-provided data. Don’t trust user input and always filter and escape data that is used in templates.
- Security Headers: Utilize security headers, such as Content Security Policy (CSP), to prevent the execution of malicious scripts injected through SSTI.
- Template Engine Best Practices: If you’re using a template engine, follow best practices for that specific engine. Ensure that your templates are safely rendered without relying on untrusted data.
- Regular Auditing: Conduct regular security audits and vulnerability assessments to identify and patch SSTI vulnerabilities before attackers do.
- Content-Security Policies: Implement content-security policies to restrict the sources of content and scripts that can be executed in your application.
- Rate Limiting: Employ rate limiting to deter attackers from exploiting SSTI vulnerabilities repeatedly.
- Use of Logic Less Template : One of the simplest ways to avoid introducing server-side template injection vulnerabilities is to always use a “logic-less” template engine, such as Mustache.
- Sandboxed Environment : Executing user code exclusively in a sandboxed environment—where potentially hazardous modules and functions have been completely eliminated—is an additional precaution. Sadly, sandboxing untrusted code is hard by nature and easily circumvented.
-> (Request Demo) 10 X Pen Testing Frequency & 100% Asset Coverage
Conclusion
SSTI vulnerabilities are a serious concern for web application security. They can provide a foothold for attackers to manipulate your server and potentially achieve RCE. By understanding the mechanics of SSTI, and following best practices for prevention and mitigation, you can significantly reduce the risk of falling victim to this dangerous vulnerability chain.
SSTI can be identified wiith various commercial and open source tools such as Burp Suite, Owasp Zap, Netsparker etc. FireCompass integrates the best of open source and commercial tools to discover SSTI in your attack surface by integrating its Web App Vulnerability Discovery Playbooks with EASM.
>> (Learn More) "Automated Pen Testing Significantly Improved The Depth & Breadth Of Testing" - Ed Adams, Security Innovation
By: FireCompass Delivery Team – Keyur Talati
About FireCompass:
FireCompass is a SaaS platform for Continuous Automated Pen Testing, Red Teaming and External Attack Surface Management (EASM). FireCompass continuously indexes and monitors the deep, dark and surface webs using nation-state grade reconnaissance techniques. The platform automatically discovers an organization’s digital attack surface and launches multi-stage safe attacks, mimicking a real attacker, to help identify breach and attack paths that are otherwise missed out by conventional tools.
Feel free to get in touch with us to get a better view of your attack surface.