Continuous Pentest add 5x more value to the Organization, a best of both Vulnerability Assessment and Traditional Pentest
Organizations employ pentesting to validate critical risks and assess the potential impact of a critical CVE. Traditional pentesting, guided by human experts and following a step-by-step waterfall model, typically covers only 10 to 20% of assets in each assessment.
In contrast, continuous pentesting offers an agile and automated approach that can cover 100% of assets in a single round and responds rapidly to newly added assets or published CVEs.
Our Automated Pentest platform gives you multi-stage attack playbooks to mimic a real attacker and accurately pinpoint prioritized vulnerabilities that would be targeted first. Automated Pentest delivers shorter mean time to remediation and increased depth and breadth of coverage so you can focus on your mission of keeping attackers out and keeping IT/OT services running smoothly and securely.
Gartner says “Nation-state actors and criminal organizations operate with a level of sophistication that surpasses the preventative and detection capabilities of most security and risk management teams.”

How FireCompass Helps
All in a Single Platform – Continuous & Automated
External Attack Surface Management (EASM)
FireCompass runs continuously and indexes the deep, dark, and surface web using the same reconnaissance techniques as threat actors do & automatically discovers an organization's dynamic digital attack surface. Followed by active validation to eliminate false positives.
Continuous Risks Discovery
Identify Critical Risks within 24 to 72 Hours. FireCompass Multi Stage Hunting Playbooks orchestrate 30K attacks and checks on Network, Web, Cloud and other assets from its geographically distributed sensor network. Hunting Playbooks include ransomware susceptibility assessments, web applications testing, credential stuffing, and objective-based campaigns would be run by attackers. 100% of your assets are continuously tested to uncover all possible security risks possible.
Automated Pentesting
FireCompass Platform performs Recon, Hunting, Attack & Safe Exploitation on the attack surface. Attack & Safe Exploitation provide initial access point, exploitation proof of concepts (PoCs), Sample Data Exfiltration, C2 Agent Installation as some of the ways to validate the risk exploitability,
Alerts Reduction
Failure to conduct frequent & extensive attacker-like reconnaissance leaves low-hanging fruits easily exploited by adversaries. The FireCompass platform works by doing:
- Zero-Knowledge fast internet-based recon on 3 Billion+ IPs using deep, dark and surface web OSINT data collections
- Uses attacker-like MITRE ATT&CK Reconnaissance techniques as threat actors would to collect data from threat intel feeds and correlate them with active scans
- AI/ML driven automated asset attribution to organizational business context
- Active validation eliminates false positives and accurately attributes business context
- Delta Reporting delivers situational awareness to stakeholders about the attack surface
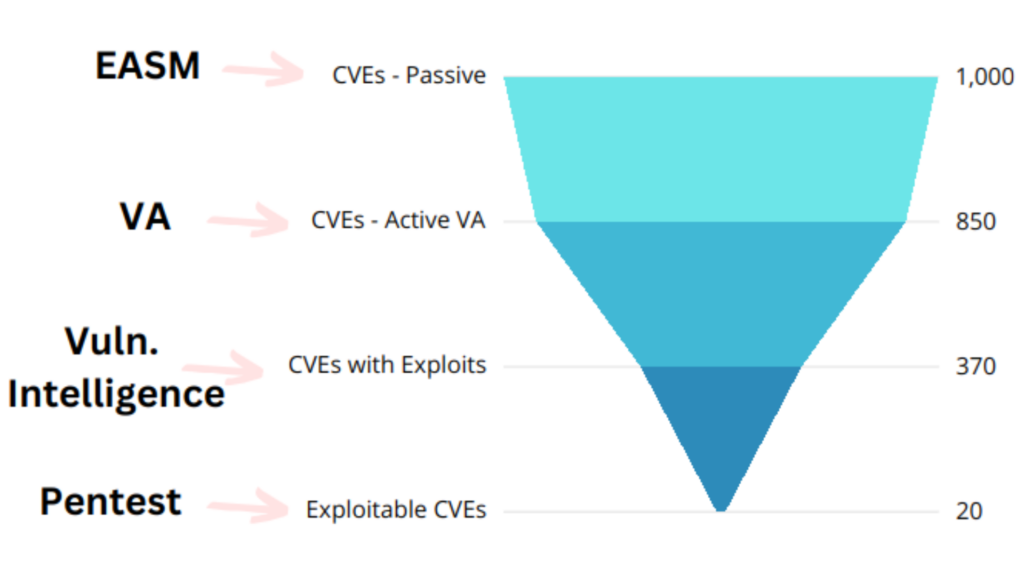
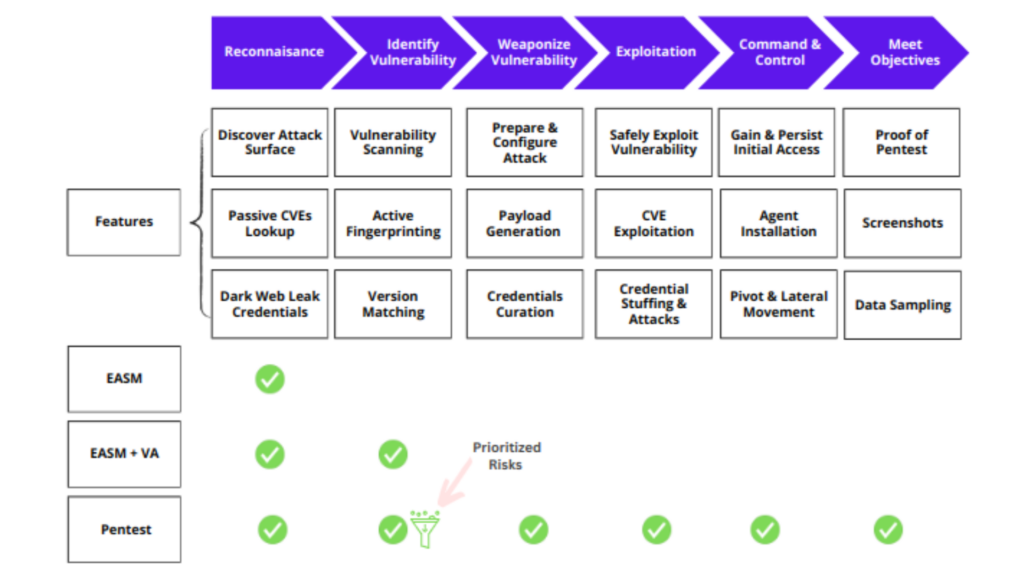
Comprehensive Mitre Coverage
Conventional ASM and VA covers partial MITRE stages upto Reconnaissance and Vulnerability Identification. As a result, EASM with VA is not able to validate risk and security controls effectiveness. Continuous Pentest coves wide spectrum of MITRE framework, use safe and lite exploits to validate risks and security controls.
- Increase Automation & Faster Analysis to free your penetration testers to focus on more challenging work
- Emulate latest threat actors such as Chinese State-Sponsored actors, Russian Threat Actors & more
- Evaluate susceptibility to multiple ransomware flavours
- Conduct DAST and OWASP Top 10 attacks on web based applications
- Perform active social engineering attacks with phishing playbooks
Automated Pentesting
FireCompass Platform performs Recon, Hunting, Attack & Safe Exploitation on the attack surface. Attack & Safe Exploitation uses initial access point, exploitation proof of concepts (PoCs), as some of the ways to validate the risk exploitability.
- Eliminate alert fatigue by only responding to validated attacks
- Adversary-based prioritization that validates attack methods nation-state actors or cybercriminal groups are known to use
- Prioritize high-risk vulnerabilities that are most likely to be exploited
- Attack validation also filters out false positives, if the attack fails, so will attackers
- Access & improve the effectiveness of your security tools, SOC, and managed security partners
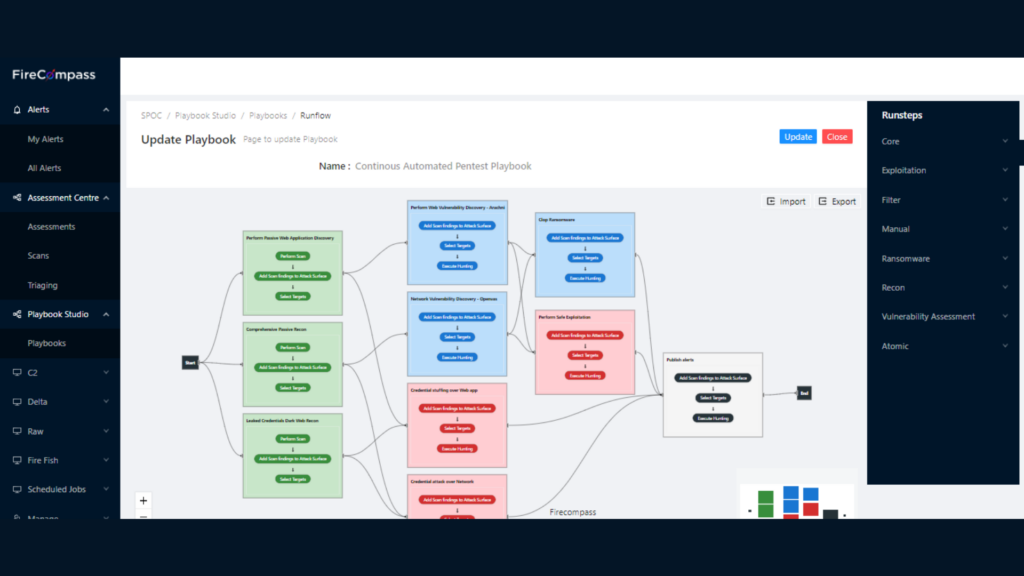
Benefits of Using FireCompass
5X
Assets Coverage
Conduct Pentest on 100% of Assets as compared to 20% of assets in traditional Pentest
10x Pen Testing Frequency
Scale your pentesting to monthly frequency as compared to yearly traditional pentest
50x Reduction of Risk Window
Identify most critical risks within 72 hours, and validate Security Controls at least monthly
80%
Cost Saving
Save upto 80% of your SecOps Bandwidth by Focusing on Prioritized Risks
Frequently Asked Questions
How does Automated Red Teaming differ from Manual Red Teaming and Penetration Testing?
What are the benefits of Automated Red Teaming with FireCompass?
- • Increased Efficiency: FireCompass’ automated processes can help streamline your red teaming efforts and maximize your team’s efficiency. FireCompass can automate tasks such as assessment scoping, data collection, data analysis, prioritization, and reporting, allowing your team to focus on the more important aspects of red teaming and blue teaming.
- • Improved Coverage: FireCompass’ automated red teaming tools can provide comprehensive coverage of your IT environment. By automating the data collection and analysis process, FireCompass can help you identify threats and vulnerabilities more quickly across your entire IT infrastructure.
- • Enhanced Visibility: FireCompass’ automated tools can provide detailed visibility into your IT environment. Automated data collection and analysis can give you a more comprehensive view of your IT infrastructure, allowing you to identify potential threats and vulnerabilities more quickly.
- • Reduced Costs: Automated red teaming with FireCompass can help reduce costs by eliminating the need to hire and train additional personnel. Automation can also help reduce the time and effort required for manual tasks, resulting in significant cost savings.
How does FireCompass automate Red Teaming?
Where does Automated Red Teaming improve compliance?
How does Automated Red Teaming improve Blue Teaming?
What are the common tools and techniques used in Red Teaming?
- • Vulnerability Scanning: Using automated tools to identify and report on potential security weaknesses in your network and systems.
- • Social Engineering: Manipulating people into giving up confidential information or performing unauthorized actions.
- • Network Mapping: Utilizing tools to map out a network’s topology and identify potential entry points.
- • Penetration Testing: Using automated tools and manual methods to identify and exploit weaknesses in your networks and systems.
- • Physical Security Testing: Utilizing physical reconnaissance and covert methods to assess the physical security of your organization.
- • Malware Analysis: Examining malicious code to better understand the nature and purpose of the attack.
- • Database Enumeration: Utilizing tools to identify and retrieve information from databases.
- • Application Security Testing: Utilizing tools to evaluate the security of web and mobile applications.
- • Wireless Network Testing: Utilizing tools to assess the security of wireless networks.
- • Phishing Campaigns: Utilize emails to employees or partners to gain initial access or information about systems including credentials.
How does FireCompass eliminate false positives?
Important Resources

We’ve put together some top talks from global security conferences that could help you get a hang on the debatable topic

We have listed a few breach response tactics that organizations need to keep handy for rainy days. Read to know more about how you can keep your organization safe.
Read More

Here we list 10 tools which can be used for Reconnaissance by Security teams in order to assess their own security posture against hackers.
About FireCompass
- Single Platform for Attack Surface Management and Automated Penetration Testing & Red Team
- Daily Risk Port Scanning & Adversary Emulation through multiple Attack Playbooks
- Prioritized Risks with real-time alerts for faster detection and remediation
Request Demo
Thank you!
You have successfully joined our subscriber list.
