As technological advances create business opportunities for businesses, they also present huge security risks of information of the same businesses. According to the U.K. government’s Cybersecurity Breaches Survey 2019, 32% of UK businesses reported breaches in their networks in 2019. And Kaspersky predicts new threat angles and attack strategies to come in the years ahead`.
Today, cyber threat actors continue to diversify their attack toolsets, at times resorting to extremely customized and persistent tools, and others successfully employing the well-known and time-tested attack methods. As a result of these sophisticated efforts, businesses must evaluate their capability to resist and respond to cyber-attacks based on an understanding of the key threats they face.
One of the ways through which businesses can assess their preventive capabilities is by the red team and through automated red teaming. Red teaming is a process through which businesses carry out simulated targeted attacks against their own networks to test their defensive protocols. It is designed to measure how well an organization’s personnel, networks, applications, and physical security protocols will respond to an attack from a real-life adversary. A red team is a cyber-security unit responsible for organizations’ continuous red teaming activities.
Red teaming goes beyond identifying gaps and vulnerabilities in an organization’s defensive security protocols; it can also provide insights into your organization’s capability to detect attacks in progress and neutralize them through a range of red teaming tools.
Red Team Landscape: Gartner
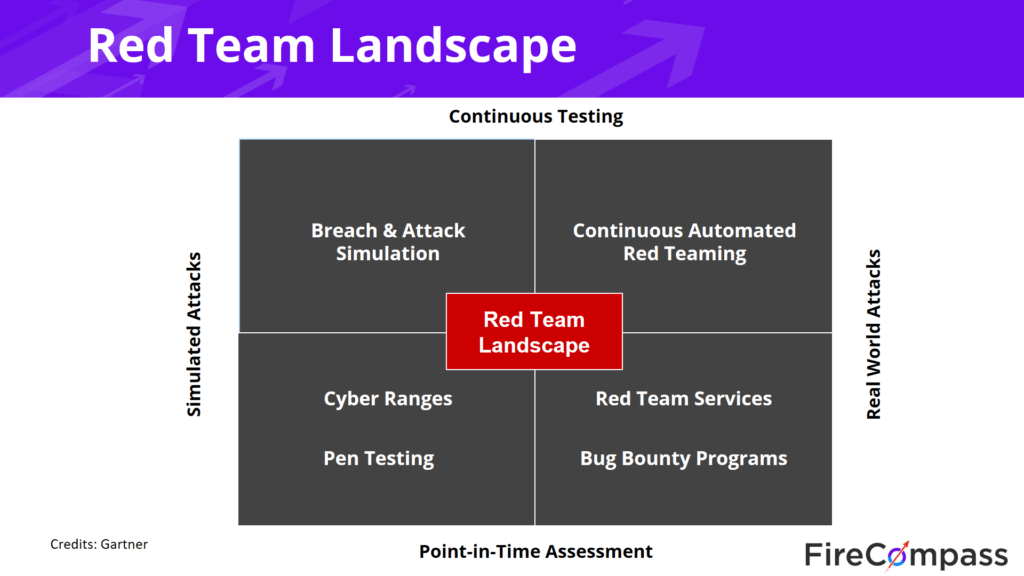
Presently there are two types of security controls; one can either make a point in time assessment or conduct continuous testing. And to protect yourself, you either have the choice of conducting simulated attacks or real-world attacks. Breach & attack simulation, and penetration testing are presently common; however, the range is limited, considering they are a point in time testing and simulated attacks.
Continuous Automated Red Teaming (CART) is an upcoming technology that fills the gap between continuous attacks and real-world attacks.
Firecompass is one of the few organizations that has recently launched a Saas based platform for CART.
Importance Of Red Team Cybersecurity
Identifies Vulnerabilities In A Network
A red team is a group of “good guys” conducting cyber-attacks, or rather ethical hackers. They utilize their cybersecurity and social engineering skills to identify vulnerabilities in applications and networks that they can use to launch real-life and simulated attacks. The success of red teaming activities means that there are vulnerabilities in the network. This presents an opportunity for the organization to patch up their weaknesses in readiness for real-life adversarial attacks.
Discover Weaknesses In Your Development And Testing Processes
For companies developing online-based applications and systems, testing is one of the essential phases. In this phase, the product is evaluated on its performance and ability to withstand internal and external threats. External threats are primarily cyber threats. This is where red teaming is important. The product is exposed to simulated attacks that are meant to test its defensive aspect. This is to ensure the product is safe from cyber threats before being deployed for implementation.
Facilitates Training For Defensive Practitioners, For Example, Blue Team
Apart from a red team that is tasked with launching friendly cyber-attacks on an application or network, the organization also has in place a blue team that is responsible for protecting the organization from real-life cyber-attacks. Therefore, there are two teams with conflicting objectives: the red team that mounts attacking activities, and the blue team that mounts defensive activities. Bringing these two teams to work together strengthens their individual skills and expertise – the red team shall be able to learn defensive techniques a blue team uses, and devise ways to break them; at the same time, a blue team shall be able to learn of attacking techniques used by a red team, and device ways to defend against them.
Assess Security Performance Levels, Including Systems, People And Processes
The levels of success of red teaming activities is important to assess the performance level of people and processes that have been put in place to protect against cyber threats. This helps an organization in knowing its current posture and allows it to plan ahead. If red teaming activities are overly successful, then that means people and processes put in place to protect against such activities are overly weak; and the organization will have to overhaul its defensive structures.
Understand The Impact Of A Security Breach
Organizations that may not have been on the receiving end of damaging cyber-attacks may not quite understand the impact of a security breach, but red teaming simulated attacks may make them realize how destructive these breaches might have. For instance, if a red team conducts a simulated attack that brings the entire network down, the organization will surely be cautious when it comes to security breaches.
Collect Evidence To Justify Security Spending
Red teaming activities expose the vulnerabilities of an organization’s defensive systems. For an IT department seeking more funding, a red teaming report can come in handy in justifying the need to spend more on network security. For instance, if red teaming activities were successful in knocking down the core infrastructure of an organization, there would be a consensus among all the stakeholders in reinforcing the organization’s defensive structures.




