The acceleration in digital transformation has brought about a major shift in the types of threats that organizations are subject to and there is an emerging need for increased visibility.
“We are very excited about FireCompass’ inclusion in the Gartner report. This is testament to the emerging need for continuous attack surface discovery and continuous red teaming/penetration testing as a critical security control for the industry.”
Bikash Barai, Co-Founder, FireCompassIn the Hype Cycle for Security Operations 2021, Gartner points out, organizations that can easily identify the event types that will impact their business in terms of brand damage or reduced operational capacity, stand a much greater chance of having an effective and measurable security operations capability.
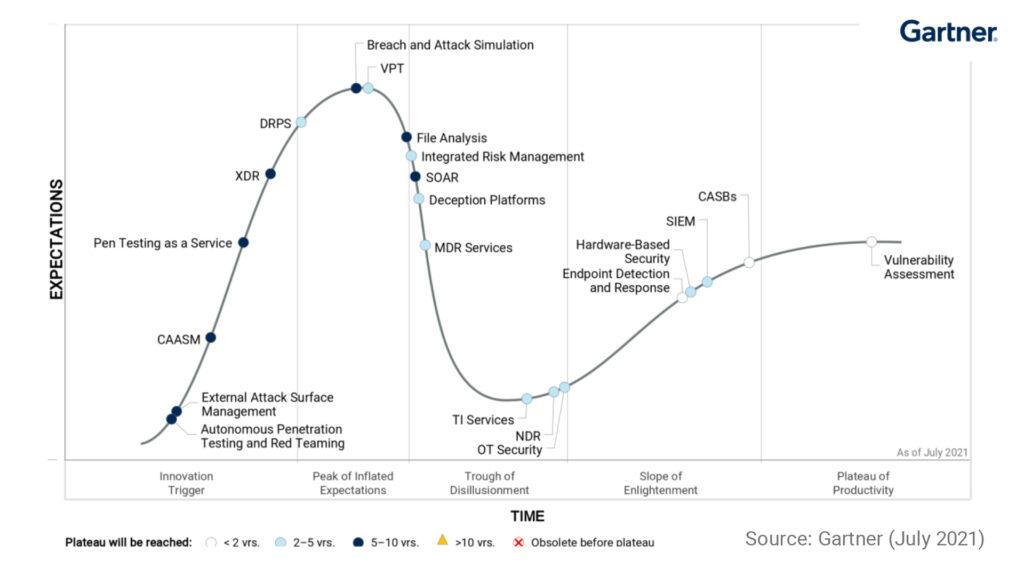
In the 2021 Hype Cycle for Security Operations, Gartner analyzes 21 profiles including Autonomous Penetration Testing and Red Teaming, External Attack Surface Management, CAASM, Pen Testing as a Service, XDR, DRPS, Breach and Attack Simulation, VPT, File Analysis, Integrated Risk Management, SOAR, Deception Platforms, MDR Services, TI Services, NDR, OT Security, Endpoint Detection and Response, Hardware-Based Security, SIEM, CASBs and Vulnerability Assessment.
Read the report to find out how you can cut through the noise in security and capture transformational benefits.
Download Gartner Hype Cycle For Security Operations, 2021
Thank you!
You have successfully joined our subscriber list.
New Entrants to the Gartner Hype Cycle Security Operations 2021:
FireCompass Use Cases
Single Platform For Continuous Discovery & Testing Of Your External Attack Surface
External Attack Surface Management (EASM)
Identify all IPs, Applications, exposed database/cloud buckets, code leaks, leaked credentials, vulnerabilities, exposed test/pre-production systems, etc.
Continuous Automated Red Teaming (CART)
Launches multi-stage attacks on your attack surface and identifies the breach and attack paths.
Ransomware Risk Assessment (RAST)
Discover Risky Ports which are most likely to be attacked and mitigate ransomware risks
Get A Hacker's View Of Your Attack Surface
See your organization’s attack surface from a hacker’s viewpoint (Unsanctioned Cloud Assets, Digital Footprint, Phishing Risks, Misconfigured Infrastructure & more.)
Disclaimer:
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose. GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally, and is used herein with permission. All rights reserved.

