Key Findings, Insights & Recommendations From Gartner Attack Surface Management – Innovation Insight
According to Gartner Attack Surface Management, Innovation Insights, “Security and risk management leaders aware of their attack surface can improve their risk posture by prioritizing security hygiene and increasing its visibility.”
“By 2026, 20% of companies will have more than 95% visibility of all their assets, which will be prioritized by risk and control coverage by implementing cyber asset attack surface management functionality, up from less than 1% in 2022.” – the report estimates.
Download The Report
Thank you!
You have successfully joined our subscriber list.
Top 3 Benefits & Uses of Attack Surface Management Solutions According to Gartner:
- “Improving asset visibility enables organizations to avoid blind spots and unmanaged technology (such as “shadow IT”), thus improving their security posture and enabling more comprehensive risk management.”
- “Understanding potential attack paths toward assets helps organizations prioritize security control deployment and configuration. This, in turn, helps reduce unnecessary exposure to the internet and the public domain, which could be exploited.”
- “Quicker audit compliance reporting is enabled by more accurate, current, and comprehensive asset and security control reports.”
Key Recommendations from Gartner Innovation Insights for Attack Surface Management include:
“Perform an enterprise attack surface gap analysis to detect potential blind spots in IT and security practices and technology. This is a foundation for improving any security program, but especially when security and risk management leaders have to protect environments of growing complexity.”
"The tool has exceeded our expectations"
- Risk Manager, Sprint USA (now part of T-Mobile)

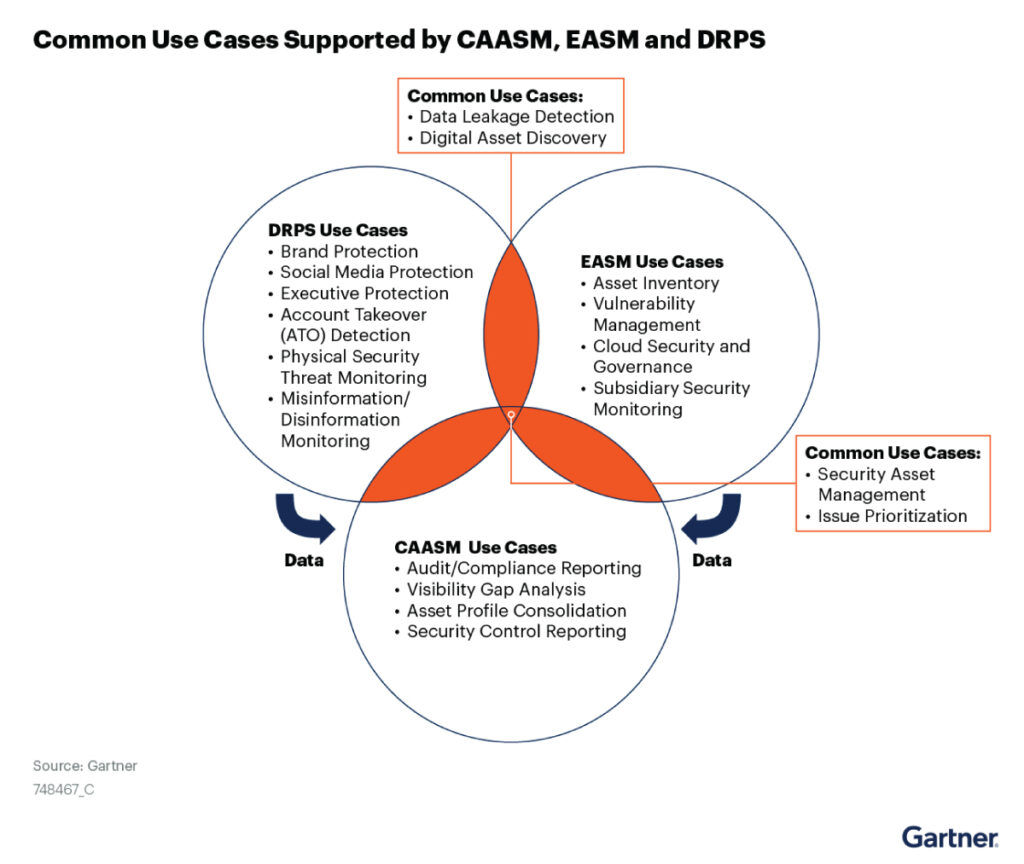
FireCompass Use Cases
Single Platform For Continuous Discovery & Testing Of Your External Attack Surface
Ransomware Attack Surface Testing (RAST)
Discover ransomware attack surface and it’s risk by scanning entire internet for risky assets potentially belonging to the organization
External Attack Surface Management (EASM)
Identify all IPs, Applications, exposed database/cloud buckets, code leaks, leaked credentials, vulnerabilities, exposed test/pre-production systems, etc.
Continuous Automated Red Teaming (CART)
Launches multi-stage attacks on your attack surface and identifies the breach and attack paths.
Get A Hacker's View Of Your Attack Surface
Disclaimer:
Gartner, Innovation Insight for Attack Surface Management, Published 24 March 2022, By Mitchell Schneider, John Watts, Pete Shoard
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose. GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally, and is used herein with permission. All rights reserved.



