Weekly Report: New Hacking Techniques and Critical CVEs 10 Feb – 16 Feb 2026
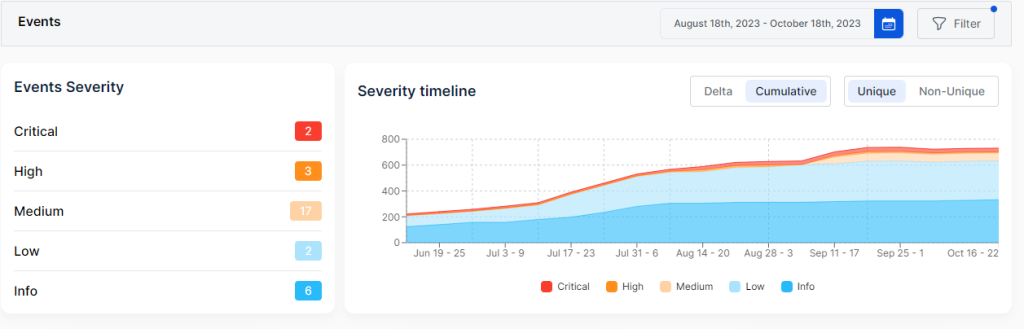
Critical vulnerabilities dominated with Microsoft Patch Tuesday addressing 6 zero-days (CVE-2026-21510, CVE-2026-21513, CVE-2026-21514, CVE-2026-21519, CVE-2026-21533) exploited in Windows Shell and Office. ZLAN ICS devices face complete takeover via CVE-2026-XXXX series. Warlock ransomware exploited CVE-2026-23760 in SmarterMail. TeamPCP worm compromised 60K cloud servers. North Korea’s UNC1069 deployed AI deepfakes against crypto firms. FileZen command injection (CVE-2026-25108)… Read More »Weekly Report: New Hacking Techniques and Critical CVEs 10 Feb – 16 Feb 2026