In today’s world, it’s hard to envision life without telecommunication services. Individuals engaging in activities like online payments, online shopping, and social media are familiar with using one-time passwords for transaction verification and 2F authentication. The security of this authentication method relies primarily on restricting access to telecommunication networks.
Introduction to SS7
Signaling System 7 (SS7) is a set of telephonic protocols that control and exchange information between a network in a public switched telephone network (PSTN), which is a global network of interconnected telephone systems that allows users to communicate by voice. It enables the setup and termination of telephone calls, call routing, as well as various other services such as SMS, mobile roaming, and number portability. It plays a critical role in both traditional landline and mobile (including 2G, 3G, and even 5G) networks.
Key Features of SS7 Protocol
- Service management: SS7 enables services like displaying the caller ID i.e. phone number to the recipient, call forwarding, roaming, and number portability.
- SMS and Data Services: It facilitates the transmission of SMS messages, and ensures reliable communication with mobile data.
- Billing and planning: The SS7 protocol assists in gathering and transferring billing-related information so that users can be charged correctly for the services they use.
SS7 Architecture
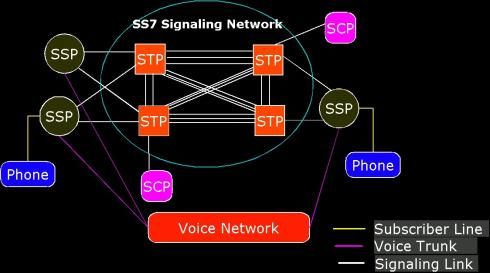
All nodes within the SS7 network are referred to as Signaling Points (SPs). Each SP is assigned a unique identifier known as a Point Code (PC). SPs can read a Point Code to ascertain whether a message is intended for that specific node, and they also have the capability to route SS7 messages to other SPs. There are three types of signaling points in the SS7 network:
- SSP (Signal Switching Point): SPs are primarily responsible for initiating and terminating calls. They connect to end-users with one another by checking the routing table. This includes Mobile Switching Centers (MSCs) nodes. It works closely with the VLR (Visitor Location Register) to retrieve its subscriber information.
- SCP (Service Control Point): SCPs provide advanced services such as database lookups. They interact with SSPs to process requests for services like number translation and call forwarding.
- HLR (Home Location Register): These nodes store subscriber information and location data.
The SCP accesses databases like the HLR and provides information required to process requests from the SSP.
STP (Signaling Transfer Point) → An STP acts as a router between different SPs in the SS7 network.
SS7 Protocol Stack vs OSI Model
As already said, SS7 is not a single protocol but a set of protocols that maps with the 7 layers of OSI model.
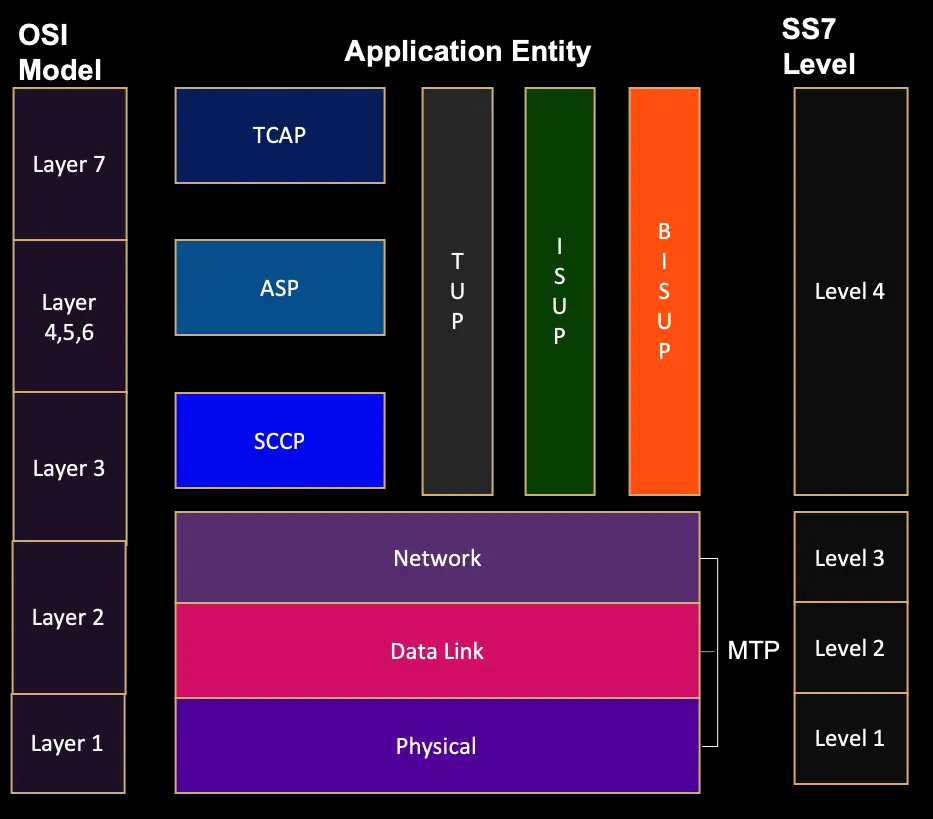
MTP Level 1: This layer corresponds to the Physical Layer of the OSI model. It deals with the physical transmission of data bits, converting them into electric signals. Transferring over various media, such as cables and fiber optical medium.
MTP Level 2: This layer aligns with the Data Link Layer of the OSI model. MTP Level 2 provides reliable data transfer by implementing error detection and correction, ensuring that messages are transmitted without errors. It establishes links between signaling points and handles flow control.
MTP Level 3: This layer corresponds to the Network Layer of the OSI model. MTP Level 3 is responsible for routing signaling messages to their destination. It manages addressing, and message routing, and provides mechanisms for network management. MTP Level 3 ensures that messages are delivered to the correct signaling points within the network.
SCCP (Signaling Connection Control Part): SCCP can be mapped to the Transport Layer of the OSI model. It enhances the capabilities of MTP by providing connection-oriented and connectionless communication services. SCCP manages transport functions such as segmentation, flow control, and error handling for signaling messages, ensuring that data is delivered reliably between applications.
ISUP (ISDN User Part): ISUP corresponds to the Session Layer of the OSI model. It is responsible for establishing, maintaining, and terminating communication sessions between users. ISUP also manages the billing rate.
TCAP (Transaction Capabilities Application Part): TCAP can be mapped to the Application Layer of the OSI model. It enables applications to exchange transaction-oriented messages and facilitates communication between various databases and services from one switch location to another in different networks.
Vulnerabilities Present in SS7 Network
The vulnerabilities in the SS7 (Signaling System 7) protocol that allow hackers to exploit it and perform attacks stem from several design flaws and the lack of robust security measures. Here are the key vulnerabilities:
1. Lack of Authentication Mechanisms
SS7 does not require strong authentication for signaling messages. This means that any node can send messages that appear to be from legitimate sources. Attackers can easily spoof Point Codes (PCs) to impersonate legitimate nodes like Mobile Switching Centers (MSCs) or Visitor Location Registers (VLRs).
2. Open Network Architecture
The SS7 protocol was designed for a more trusted environment when it was developed, assuming that all entities within the network could be trusted. This openness means that once an attacker gains access to the SS7 network, they can exploit the system without significant barriers.
3. Unencrypted Traffic
The signaling messages transmitted over SS7 networks are typically unencrypted. This lack of encryption makes it easier for attackers to intercept and analyze messages. They can extract sensitive information or manipulate messages for malicious purposes.
4. Insufficient Access Controls
Telecom companies often allow various entities (e.g., partners, and third-party service providers) to connect to their SS7 networks without stringent security checks.
Real-Life Incidents of SS7 Attacks
There have been several documented incidents where vulnerabilities in the Signaling System 7 (SS7) protocol were exploited:
- Bank Account Thefts in Germany (2017): Attackers exploited SS7 flaws to intercept two-factor authentication (2FA) codes sent via SMS, enabling unauthorized withdrawals from bank accounts. They first infected victims’ computers with malware to obtain banking credentials and phone numbers, then used SS7 vulnerabilities to reroute SMS messages containing 2FA codes to devices they controlled, facilitating fraudulent transactions. (ref: https://www.makeuseof.com/why-is-ss7-messaging-security-risk/)
- Global Surveillance Activities: Security researchers have demonstrated that SS7 vulnerabilities allow for real-time tracking of mobile users’ locations and interception of calls and text messages. Reports indicate that surveillance companies have marketed systems leveraging SS7 flaws to track individuals worldwide. (ref: https://spectrum.ieee.org/alarming-security-defects-in-ss7-the-global-cellular-networkand-how-to-fix-them)
- AT&T Data Breach (2024): In April 2024, AT&T experienced a significant data breach affecting approximately 110 million customers. Attackers accessed call and text message records, including phone numbers, call durations, and cell site identification numbers, by exploiting vulnerabilities in protocols like SS7. This incident underscored the ongoing risks associated with SS7 security weaknesses. (ref: https://www.wired.com/story/att-phone-records-breach-110-million/)
SS7 Attacks and How They Are Performed
SS7 attacks are mobile cyber threats that take advantage of security weaknesses in the SS7 protocol to intercept and compromise voice and SMS communications within cellular networks.
SS7 attacks exploit the functionalities of communication systems that operate on the SS7 protocol to authenticate themselves and intercept text and voice communications. Attackers can impersonate legitimate network nodes, such as Mobile Switching Centers (MSCs) or Visitor Location Registers (VLRs), by spoofing their Point Codes (PCs), allowing them to redirect calls and messages. This capability enables them to access sensitive information undetected.
Exploiting the SS7 Network Using SigPloit
SigPloit is an open-source penetration testing framework designed to exploit vulnerabilities in telecommunication protocols, particularly SS7 (Signaling System 7), Diameter, GTP (GPRS Tunneling Protocol), and SIP (Session Initiation Protocol). Internally, SigPloit uses several techniques and components to exploit SS7 vulnerabilities which include:
- Mobile Application Part (MAP): This is the most targeted protocol in SigPloit for attacks like location tracking and SMS interception. The tool sends MAP messages (e.g., UpdateLocation, AnyTimeInterrogation) to interact with HLRs, VLRs, and MSCs and get the current location of the victim or send the message to the attacker instead of the actual recipient.
- Spoofing Point Code(PCs): By impersonating a legitimate signaling point like an MSC or HLR, attackers can send fake messages that appear to come from trusted network elements and masquerade as MSCs or VLRs to manipulate call routing, and intercept communications.
- MitM Attacks: SigPloit can simulate Man-in-the-Middle (MitM) attacks by manipulating call or SMS routing messages sent by MSCs or STPs. By altering routing messages, an attacker can place themselves between the communication paths of two parties.
Accessing the SS7 Network with SigTran
Before attacking the SS7 protocol, we need to get into that network. This is highly restricted as it can lead to the interception of calls and messages and many such activities.
One of the ways to get access to the SS7 network is by using SigTran (Signal Transport) to convert the SS7 protocol into a TCP/IP suite.
You will need a SIGTRAN gateway to interface with a traditional SS7 network or use SIGTRAN protocols in an IP environment. Telecom equipment manufacturers or vendors provide such gateways. There we need to configure the different layers of SigTran protocol i.e. SCTP, M3UA, SUA, and Layers.
- M2UA ( MTP2 User Adaptation Layer) and M2PA (MTP2 User Peer to Peer Adaption Layer): At the MTP2 level of the SS7 protocol stack, M2UA and M2PA are two protocols used by SigTran. Both of these protocols replace the traditional MTP2 (Message Transfer Part Level 2) layer, adapting MTP3 signaling messages to work with the SCTP/IP stack for transport over IP.
- MTP3-User Adaptation Layer (M3UA) operates at a lower layer than SUA, directly replacing MTP3. It enables the transfer of all SS7 MTP3-User Part messages, like ISUP and SCCP, over IP using SCTP.
- SCTP (Stream Control Transmission Protocol): SCTP is the transport layer protocol used in SIGTRAN replacing the MTP2 layer of SS7. Unlike TCP, SCTP is message-oriented, meaning it can handle discrete messages rather than byte streams, which is suitable for signaling protocols.
- SUA (SCCP-User Adaptation Layer): It is a protocol within the SIGTRAN suite designed to facilitate the transport of SCCP-User signaling messages, such as TCAP, over IP networks. SUA allows these messages, which are traditionally handled in SS7 networks, to be sent seamlessly over IP without altering their core functions. By leveraging SCTP (Stream Control Transmission Protocol).
Using SigPloit to Exploit SS7 Vulnerabilities
Install SigPloit
> git clone https://github.com/SigPloiter/SigPloit.git
> cd SigPloit
> sudo pip2 install -r requirements.txt
> python sigploit.py
Use SigPloit to Intercept Messages and Calls
You need to have access to the SS7 network before performing the attack. Which can be done with SigTran as discussed earlier.
Please Enter: 0
 Please Enter: 1
Please Enter: 1
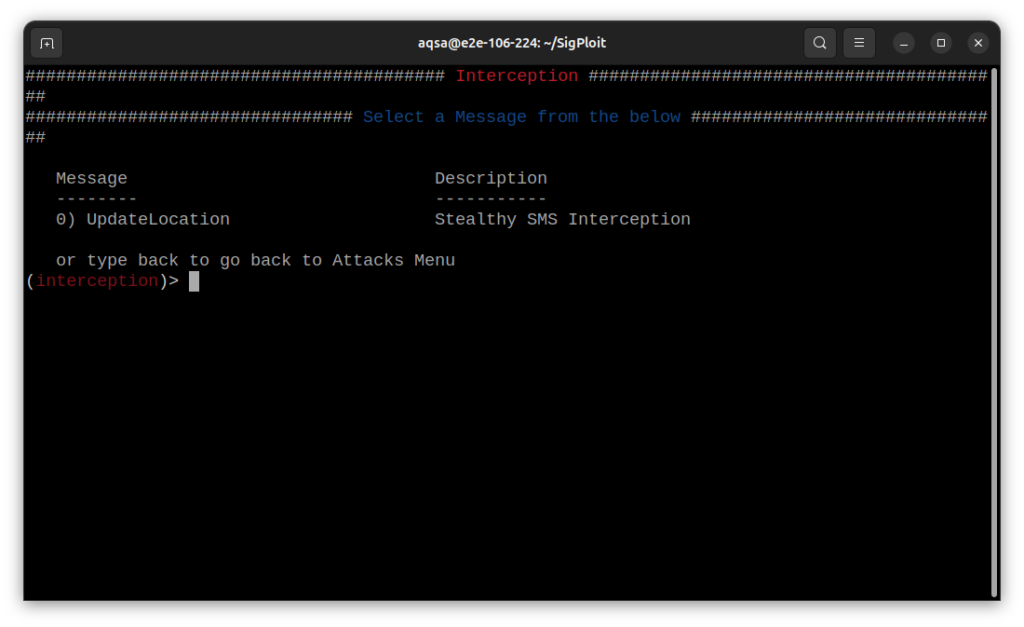 Please Enter: 0
Please Enter: 0
> show options
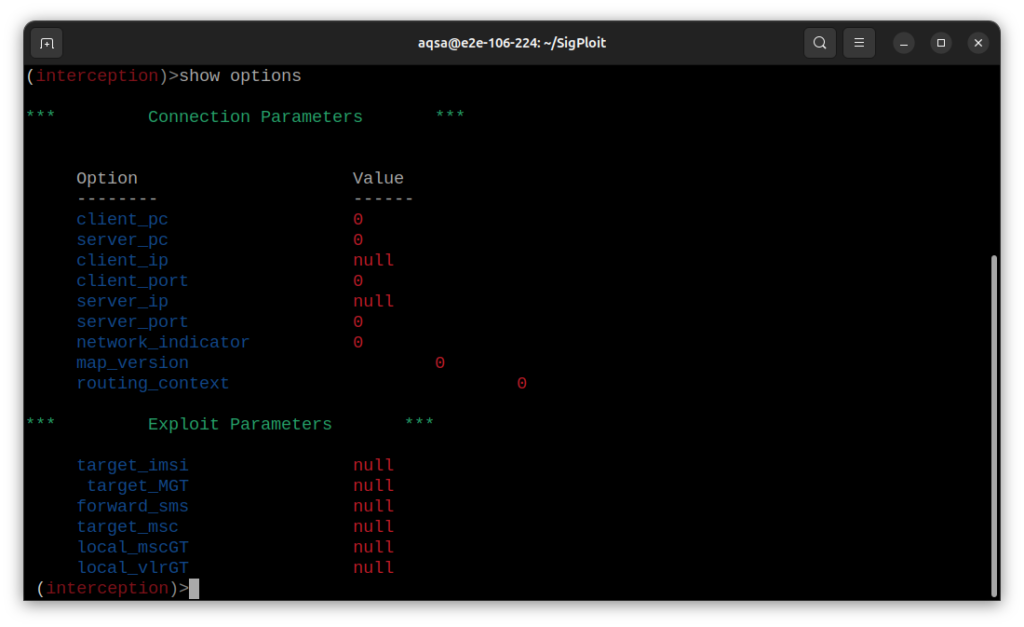
For setting these parameters, refer to the readme file present at this location:
SigPloit/Testing/Server/Attacks/Interception/UpdateLocation_Server
> cat Parameters
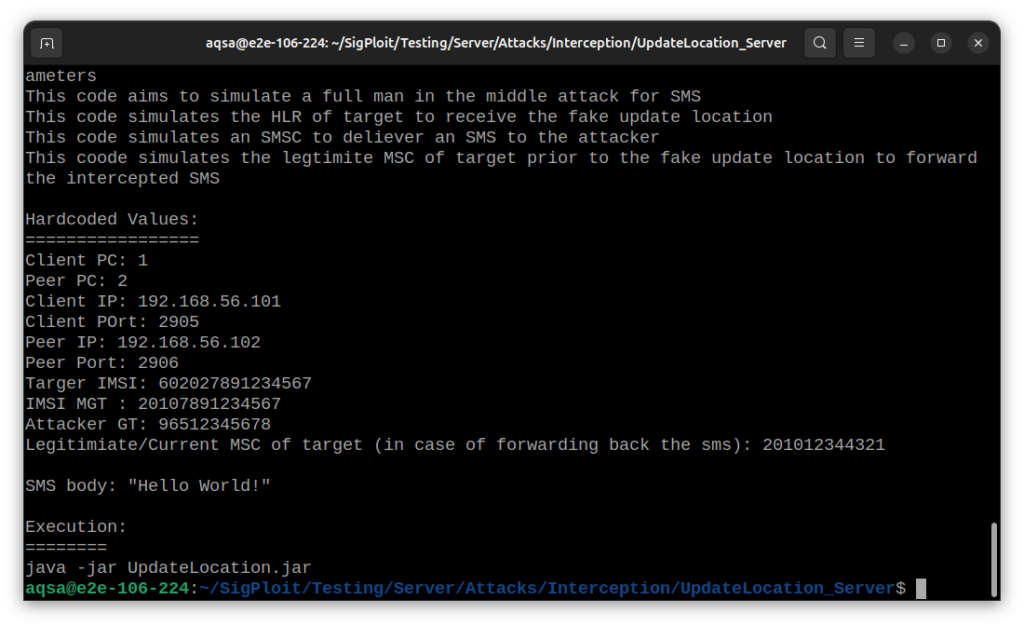
Parameters Explained:
- client_pc: This represents the Point Code (PC) of the attacker’s system, which is configured to communicate within the SS7 network. It identifies the source of the signaling messages initiated by the attacker. In the SIGTRAN setup, it acts as the originating point for sending SCTP packets.
- server_pc: This is the Point Code of the server or the target system within the SS7 network. It designates the destination for the signaling messages, which could be a Mobile Switching Center (MSC) or another entity involved in mobile communication.
- Ports 2905 and 2906: These ports are commonly used for SCTP communication in SIGTRAN setups. They facilitate the transport of SS7 signaling messages over IP networks.
- target_imsi (International Mobile Subscriber Identity): The unique identifier assigned to the mobile subscriber that the attacker aims to intercept or track. By targeting the IMSI, the attacker can monitor or manipulate communications related to that specific subscriber.
- target_MGT (Mobile Global Title): The Global Title used to route messages associated with the target IMSI. The IMSI MGT serves as a routing key, directing the attacker’s messages to the appropriate MSC or other network elements handling the target subscriber’s communications.
- target_msc: It is the Mobile Switching Center currently serving the target subscriber. The legitimate MSC is responsible for managing the call and messaging services for the target IMSI. It is crucial for the attacker to successfully intercept or manipulate communications.
Now add these IP addresses in your machine (i.e., client):
> sudo ip address add 192.168.56.101/32 dev lo
> sudo ip address add 192.168.56.102/32 dev lo
Now set the values in the tool that were found earlier in the config file.
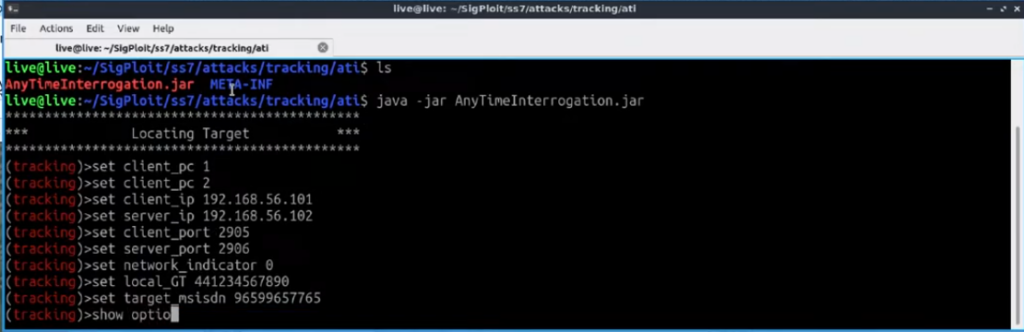
> run
This concludes the interception of calls and SMS using SigPloit. Similarly, we can use other options such as tracking location and launching a DoS attack.
Defending Against SS7 Attacks
Mitigating SS7 attacks is complex due to the vulnerabilities in the SS7 protocol itself, which was designed in the 1970s without security in mind. However, there are several strategies and solutions that can significantly reduce the risk of SS7-based attacks.
- Multi-Factor Authentication (MFA): Encourage subscribers to use MFA for sensitive services. While SS7 attacks can potentially intercept SMS-based OTPs, app-based authentication or hardware tokens add an extra layer of security.
- Limit Access to SS7 Networks: Restrict SS7 network access to trusted partners only. Implement a whitelist of authorized mobile network operators (MNOs) and enforce strict access controls.
- Choosing a reputable carrier: Choose a mobile carrier known for its robust security practices and proactive measures to safeguard customers from SS7 attacks. Such a carrier will typically have specialized protections and policies that work to detect, prevent, and respond to SS7-based threats.
- Advanced SS7 Firewall and Filtering: The carrier should use an advanced SS7 firewall, which continuously monitors and filters all incoming and outgoing SS7 traffic. This technology detects unusual patterns that might indicate an SS7-based intrusion, such as unauthorized location-tracking requests or attempts to redirect messages and calls.
- Beware of Phishing Attempts: Be wary of unsolicited emails, texts, or calls requesting personal information. Avoid clicking on links or downloading attachments from unfamiliar sources.
- Restrict Sharing of Sensitive Information: Refrain from providing details like your full address, date of birth, or social security number over the phone or online, especially to unknown individuals or organizations.
- Encryption Overlays: While SS7 does not support native encryption, some operators have implemented encryption overlays to secure sensitive signaling information. This prevents attackers from easily intercepting or altering SS7 messages even if they gain network access.
Alternatives to SS7 Protocol
There are several alternatives to the SS7 protocol, especially in modern telecom networks like 4G/5G. These alternatives often provide enhanced security for newer technologies.
- Diameter: It is designed to replace SS7 and provide more advanced features for authentication, authorization, and accounting (AAA). It is widely used in 4G and 5G networks for managing network access and services.
- SIP (Session Initiation Protocol): SIP is a signaling protocol used primarily for initiating, maintaining, and terminating real-time sessions that include voice, video, and messaging applications. SIP uses SRTP (Secure Real-time Transport Protocol) and TLS (Transport Layer Security) to encrypt media content and signaling messages.
- SIGTRAN (Signal Transport): An extension of the SS7 protocol family, SIGTRAN uses the Stream Control Transmission Protocol (SCTP) to transport SS7 messages over IP networks instead of TCP/UDP.
Why Are SS7 Networks Still Used?
SS7 networks are widely used due to their integral role in telecom infrastructure and the complexity of replacing them. This is why SS7 is still prevalent:
- Compatibility with Legacy Networks: SS7 has been in use since the 1970s and is the backbone of global telecommunications infrastructure. Replacing SS7 in 2G and 3G networks is technically challenging and costly, especially in regions where these older networks are still in use.
- Interoperability with Modern Networks: Even though 4G and 5G networks use newer signaling protocols (like Diameter for 4G and HTTP/2 for 5G), most mobile carriers need SS7 to enable roaming and handovers between 2G, 3G, and 4G/5G networks. SS7 provides the only way for devices on different network generations to communicate seamlessly.
- Wide Adoption and Standardization: SS7 is a standardized protocol globally, meaning that all telecommunications providers use it for core functions like call setup, routing, billing, and SMS delivery. Replacing SS7 would require significant global coordination and investment.
Conclusion
The SS7 protocol was built for signaling between trusted telecommunication partners, but it is still being used in the backbone of mobile communication with an open market for new operators to serve more than half of the world’s population. SS7 may continue to dominate the mobile core network system for at least the next few years. Security issues of SS7 may cause serious concerns for Indian telecom Scenarios and operators should address these weaknesses and identify all possible mechanisms for addressing those issues.










