Welcome to FireCompass Research Team’s Weekly Cybersecurity Threat Report, highlighting critical CVEs and active threats from October 9 to October 13, 2023. Presenting an insightful overview of the latest vulnerabilities, malware, and threat actors impacting the cybersecurity landscape. Stay informed to protect your organization from emerging risks.
The Key Vulnerabilities That FireCompass Has Focused On Are:
- CVE-2023-3519 – Citrix ADC and Citrix Gateway
- CVE-2023-39362 – Cacti
- CVE-2023-32707 – Splunk Enterprise
- CVE-2023-4966 – NetScaler ADC and NetScaler Gateway
- Juno OS multiple vulnerabilities
- Microsoft Exchange Server – CVE-2023-36778
- Apache Tomcat Multiple Vulnerabilities
The Key Malwares & Threat Actors That FireCompass Has Focused On Are:
- CVE-2023-5360 – WordPress – Royal Elementor Addons and Templates by ‘WP Royal’
- CVE-2023-36780, CVE-2023-36786, CVE-2023-36789 – Skype Multiple Vulnerability
- CVE-2019-19356 – Netis WF2419
Latest Hacks That FireCompass Has Focused On Are:
- Maharashtra: 4 hack into software of firm, siphon Rs. 25 crore
- Over 17,000 WordPress Sites Compromised by Balada Injector
- British Cable Manufacturer Volex Confirms Unauthorized Access to its Systems and Data
- Safexpay Technology’s payment gateway hacked, Thane Police probe Rs 16,180-cr scam
Know The Vulnerabilities Impacting Key Industries and Companies:
CVE-2023-3519 – Citrix ADC and Citrix Gateway
The vulnerability is caused by a flaw in the way that Citrix ADC and Citrix Gateway handle certain HTTP requests. An attacker can exploit this flaw by sending a specially crafted HTTP request to a vulnerable appliance. If the request is successful, the attacker will be able to execute arbitrary code on the appliance.
The impact of this vulnerability is that it can allow attackers to take complete control of affected Citrix ADC and Citrix Gateway devices. This could allow attackers to steal sensitive data, disrupt operations, or install malware on downstream systems.
Here is the POC:
https://packetstormsecurity.com/files/173997/Citrix-ADC-NetScaler-Remote-Code-Execution.html
Here are the industries and companies that are affected by this CVE:
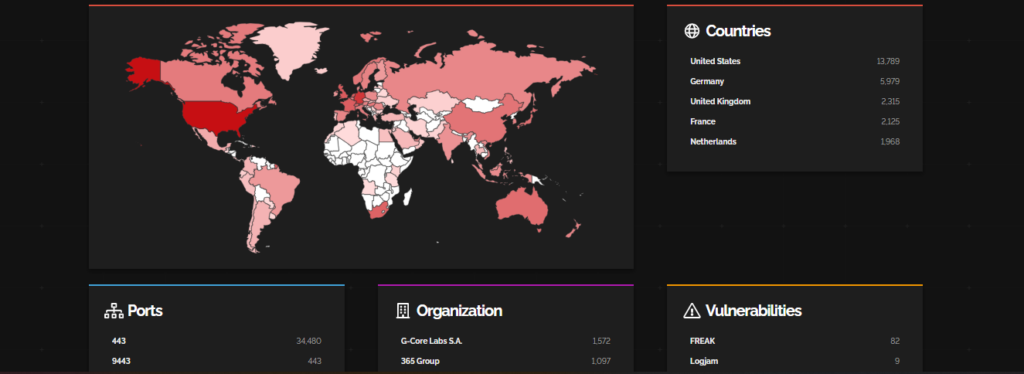
Most impacted countries are USA and Germany while CDN service providing companies are getting affected the most.
-> Hackers Won't Wait For Your Next Pen Test: Know Automated Continuous Pen Test
CVE-2023-4966 & CVE-2023-4967 – NetScaler ADC and NetScaler Gateway
CVE-2023-4966 :
A critical security vulnerability in NetScaler ADC and NetScaler Gateway. It allows an unauthenticated attacker to access sensitive information on the NetScaler appliance by sending specially crafted HTTP requests.
CVE-2023-4967 :
Privilege escalation vulnerability that can be exploited by an authenticated attacker to gain root access to the NetScaler device.
The vulnerability is caused by a flaw in the way that NetScaler ADC and NetScaler Gateway handle certain HTTP requests. An attacker can exploit this flaw by sending a specially crafted HTTP request to a vulnerable appliance. If the request is successful, the attacker will be able to access sensitive information on the appliance, such as user credentials, configuration files, and application data.
Here are the countries that are running the NetScaler instances and are vulnerable. Most impacted being the USA and Germany:

>> Discover & Test your Ransomware Attack Surface
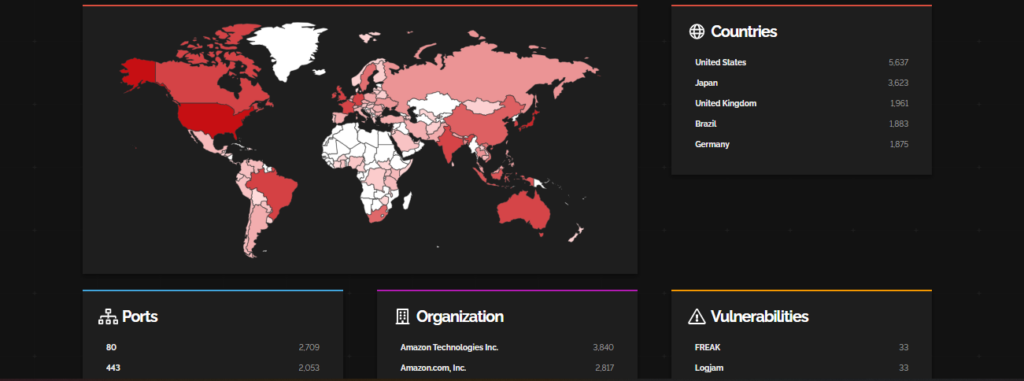
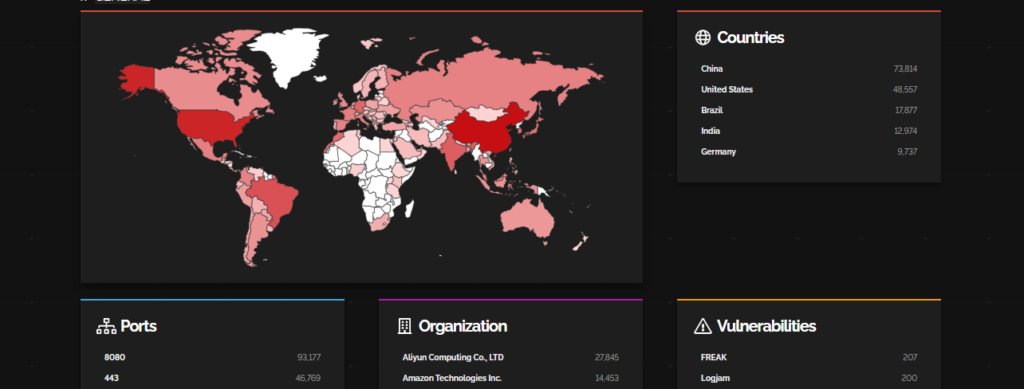
CVE-2023-39362 – Cacti
This is a critical authenticated remote code execution (RCE) vulnerability in Cacti, an open source operational monitoring and fault management framework. The vulnerability allows an authenticated user with administrator privileges to execute arbitrary code on the underlying server by injecting malicious code into the SNMP options of a device.
Here is the POC: https://packetstormsecurity.com/files/175029/Cacti-1.2.24-Command-Injection.html
Shodan analysis of the companies that are vulnerable to this CVE. Most impacted countries are the USA and Japan while Amazon Services are getting affected the most.
>> [Request RECON Demo] - Reconnaissance Techniques As Threat Actors
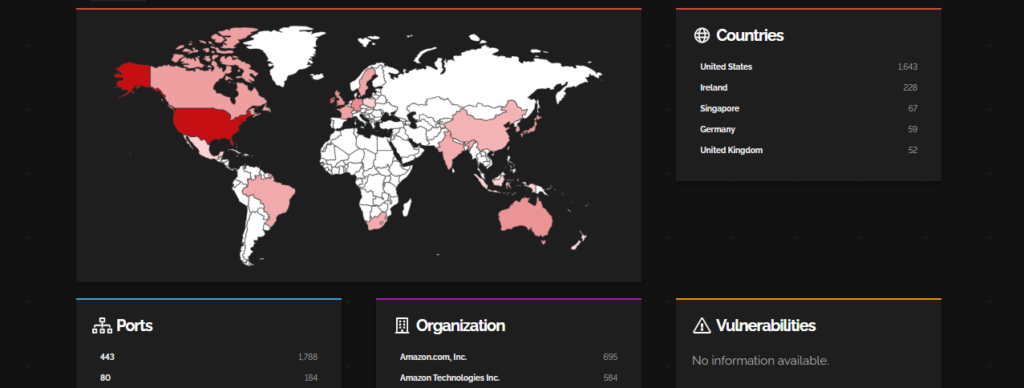
CVE-2023-32707 – Splunk Enterprise
This is a privilege escalation vulnerability in Splunk Enterprise below 9.0.5, 8.2.11, and 8.1.14, and Splunk Cloud Platform below version 9.0.2303.100. It allows a low-privileged user who holds a role that has the edit_user capability assigned to it to escalate their privileges to that of the admin user by providing specially crafted web requests.
The vulnerability is caused by a flaw in the way that Splunk Enterprise validates and processes web requests. An attacker can exploit this flaw by sending a specially crafted web request to a vulnerable appliance. If the request is successful, the attacker will be able to escalate their privileges to that of the admin user.
Most impacted countries are the USA and Ireland while Amazon Services are getting affected the most.
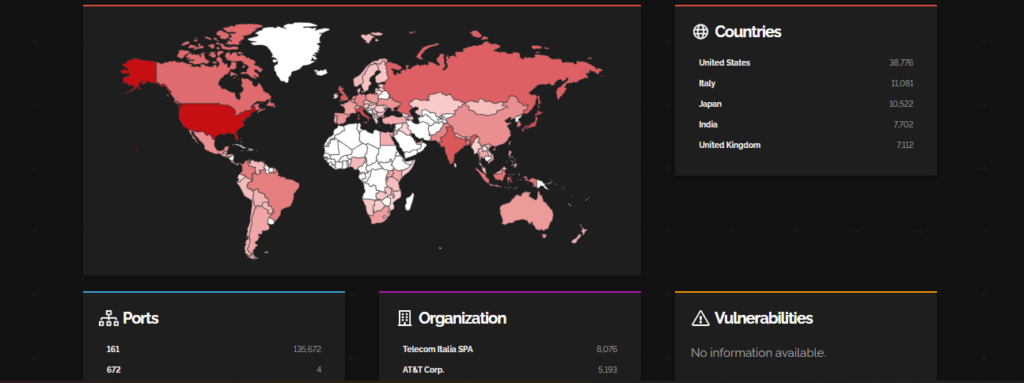
Junos OS Multiple Vulnerabilities
Junos OS which is being exploited by the hackers for past months has released an advisories for the CVEs mentioned below:
CVE-2023-36843, CVE-2023-44175, CVE-2023-44181, CVE-2023-44182, CVE-2023-44183,
CVE-2023-44184, CVE-2023-44185, CVE-2023-44191, CVE-2023-44192, CVE-2023-44194,
CVE-2023-44196, CVE-2023-44197, CVE-2023-44199, CVE-2023-44203, CVE-2023-44204
Most of the companies impacted are running the instances belonging to telecommunication companies affecting the whole telecom industry based in the USA and Italy.
Microsoft Exchange Server – CVE-2023-36778
Microsoft Exchange Server is being trending in the latest attacks by malwares, the CVE-2023-36778 is vulnerable to remote code execution.
Most impacted countries are USA and Germany while German Telecom companies are getting affected the most.
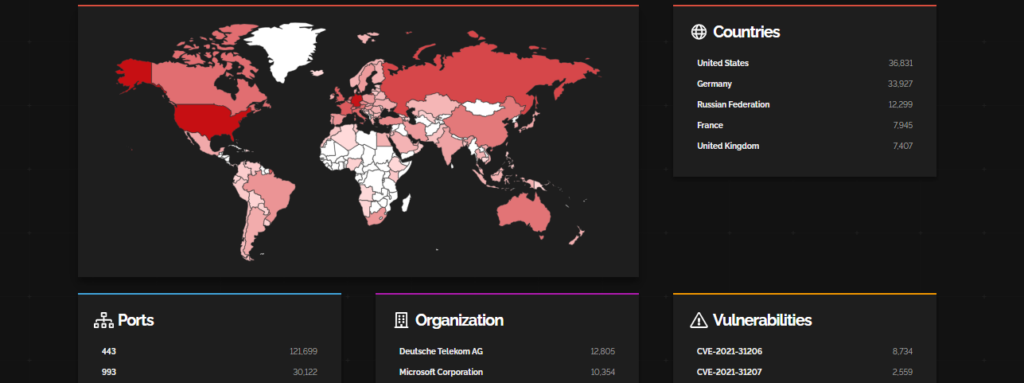
Apache Tomcat Multiple Vulnerabilities
Apache Tomcat is a free and open-source web server which is popular worldwide. It has released three CVEs this week:
- CVE-2023-42794 – Denial of service
- CVE-2023-42795 – Information Disclosure
- CVE-2023-45648 – HTTP Request Smuggling
As per the shodan, the impacted industries are computing, data services and cloud hosting companies.
>> Find Critical Risks in 72 Hours & Continuous Risk Hunting (Request Demo)
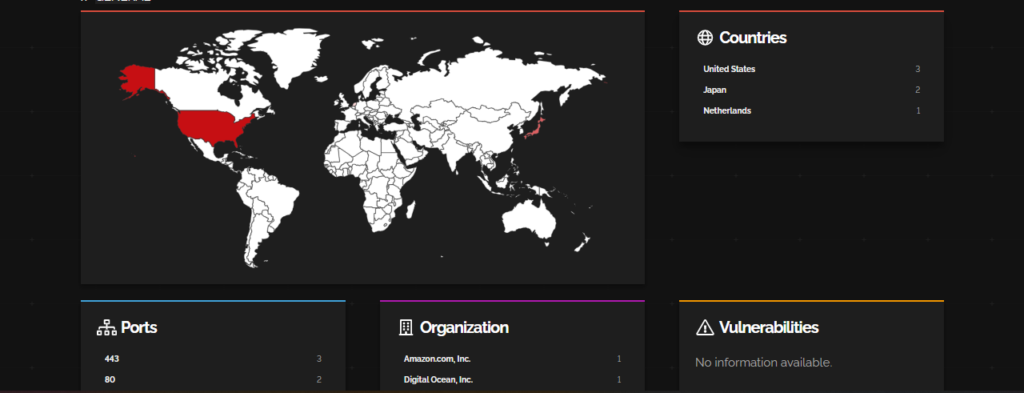
CVE-2023-5360 – WordPress – Royal Elementor Addons and Templates by ‘WP Royal’
CVE-2023-5360 is an unauthenticated arbitrary file upload vulnerability in the Royal Elementor Addons and Templates plugin for WordPress. The vulnerability allows a remote unauthenticated attacker to upload arbitrary files to vulnerable websites, including malicious PHP files that can be used to execute arbitrary code on the server. This CVE is found to be exploited by some unknown hackers in the wild.
This CVE mostly impacted on organizations which provide cloud services like, Amazon, Digital Ocean and Oracle.
CVE-2023-36780, CVE-2023-36786, CVE-2023-36789 – Skype Multiple Vulnerability
CVE-2023-36780, CVE-2023-36786, and CVE-2023-36789 are remote code execution (RCE) vulnerabilities that allow an attacker to execute arbitrary code on a victim’s computer by sending them a specially crafted message.
All three of these vulnerabilities are critical and can be exploited by an unauthenticated attacker. One of such groups is found to be DarkGate malware.
Shodan analysis of the companies that are vulnerable to these CVE:
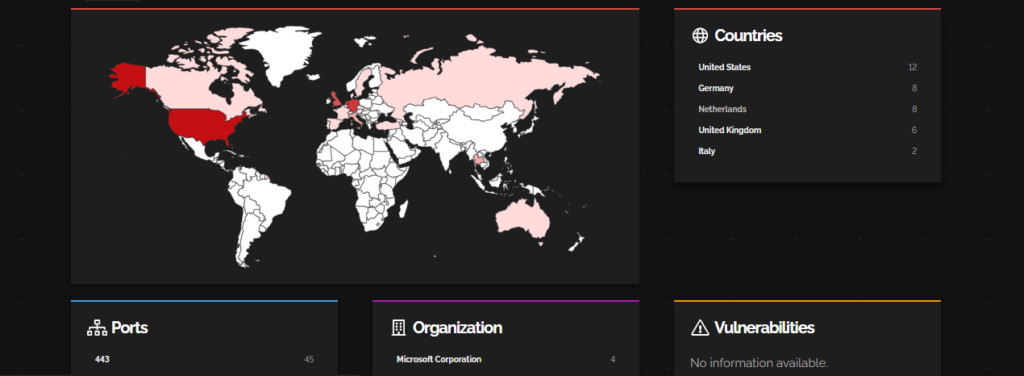
This vulnerability has mostly impacted Microsoft Corporation, Deutsche Bank AG and Gemnet (23)
CVE-2019-19356 – Netis WF2419
CVE-2019-19356 is a remote code execution (RCE) vulnerability in the Netis WF2419 router. It allows an authenticated attacker to execute arbitrary code on the router by sending specially crafted web requests.
The vulnerability is caused by a flaw in the way that the Netis WF2419 router handles certain types of web requests. An attacker can exploit this flaw by sending a specially crafted web request to the router. If the request is successful, the attacker will be able to execute arbitrary code on the router.
A successful exploit of this vulnerability could allow an attacker to take control of the router, steal data from users connected to the router, or even launch attacks against other devices on the network.
This CVE is targeted by Mirai-based DDoS (distributed denial of service) malware botnet.
Here is the POC: https://packetstormsecurity.com/files/156588/Netis-WF2419-2.2.36123-Remote-Code-Execution.html
Shodan analysis of the companies that are vulnerable to these CVE:
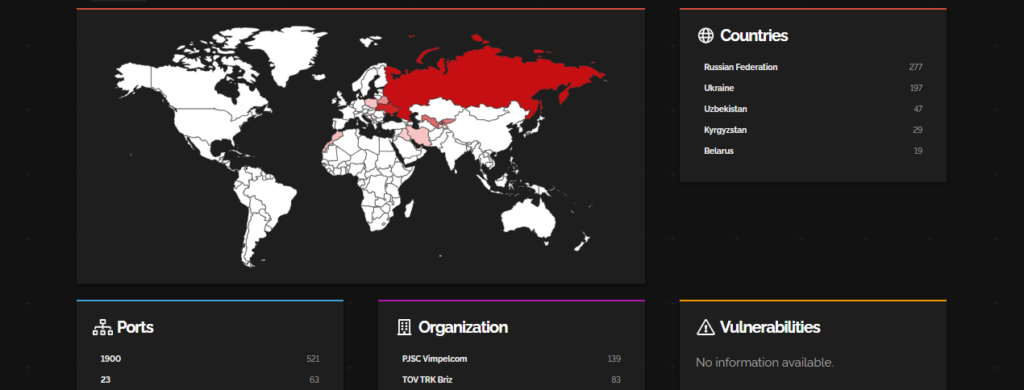
This vulnerability has mostly impacted routers and ISPs of the Soviet area of Asia (Russia).
-> (Request Demo) 10 X Pen Testing Frequency & 100% Asset Coverage
References
- https://packetstormsecurity.com/files/156588/Netis-WF2419-2.2.36123-Remote-Code-Execution.html
- https://www.wordfence.com/blog/2023/10/psa-critical-unauthenticated-arbitrary-file-upload-vulnerability-in-royal-elementor-addons-and-templates-being-actively-exploited/
- https://packetstormsecurity.com/files/175029/Cacti-1.2.24-Command-Injection.html
- https://packetstormsecurity.com/files/173997/Citrix-ADC-NetScaler-Remote-Code-Execution.html
By: Firecompass Research Team – Debdipta Halder, Soumyanil Biswas, Faran Siddiqui, Anirban Bain
References
- FireCompass Threat Intel Team
- https://www.cisa.gov/known-exploited-vulnerabilities-catalog
- NVD CVE Feed
About FireCompass:
FireCompass is a SaaS platform for Continuous Automated Pen Testing, Red Teaming and External Attack Surface Management (EASM). FireCompass continuously indexes and monitors the deep, dark and surface webs using nation-state grade reconnaissance techniques. The platform automatically discovers an organization’s digital attack surface and launches multi-stage safe attacks, mimicking a real attacker, to help identify breach and attack paths that are otherwise missed out by conventional tools.
Feel free to get in touch with us to get a better view of your attack surface.










