A critical vulnerability, CVE-2025-54253, was discovered in Adobe Experience Manager (AEM) Forms on JEE, a widely used enterprise Java application platform. This vulnerability arises from improper handling of OGNL expressions in an exposed debug servlet, allowing attackers to bypass authentication and remotely execute arbitrary code. With a maximum severity rating of CVSS 10.0, this vulnerability presents a significant risk to organizations running affected versions of AEM Forms on JEE.
In this blog, we will explore the technical details of CVE-2025-54253, outline how attackers exploit this vulnerability in real-world scenarios, and provide actionable mitigations organizations can implement to secure their environments.
What Is CVE-2025-54253?
CVE-2025-54253 is a critical OGNL injection vulnerability (CVSS 10.0) affecting Adobe AEM Forms on JEE, up to version 6.5.23.0. The flaw results from the dangerously exposed /adminui/debug servlet, which evaluates user-supplied OGNL expressions as Java code without requiring authentication or input validation. The endpoint’s misuse enables attackers to execute arbitrary system commands with a single crafted HTTP request.
Key Details:
- Severity: Critical (CVSS 10.0)
- Affected Systems: Adobe AEM Forms on JEE ≤ 6.5.23.0
- Exploit Status: In the wild, with PoC publicly available.
- Vulnerable Module: /adminui/debug endpoint with unsanitized OGNL evaluation
What is OGNL?
OGNL stands for Object-Graph Navigation Language, and is a powerful expression language for Java applications, originally designed to simplify data binding between user interfaces and backend Java objects. It enables developers to write compact expressions such as:
- Accessing and modifying object properties
- Iterating over collections
- Invoking methods dynamically
Essentially, OGNL is used to make template engines, frameworks (such as Apache Struts), and administrative/debug features more flexible by letting developers manipulate the “object graph” of a Java program without having to write large amounts of code.
Why It’s so Dangerous in This Context
While OGNL is convenient for developers, it’s inherently risky if inputs are not validated and sandboxed. OGNL expressions can invoke methods directly on Java objects, meaning that if an attacker can inject arbitrary OGNL payloads into an evaluation context, they can often escalate that into direct command execution on the underlying system.
This exact scenario plays out in AEM Forms on JEE: the debug servlet (/adminui/debug) takes arbitrary, user-supplied OGNL input and evaluates it without authentication. That design flaw turns what should be an administrative debug feature into a pre-authentication RCE vector, making exploitation trivially easy.
Root Cause Analysis
- Improper Input Validation: /adminui/debug trusts and executes unsanitized OGNL.
- No Authentication Needed: Endpoint is accessible to any network-origin request.
- Design Pattern Flaw: Debug and dev features left enabled in non-isolated environments.
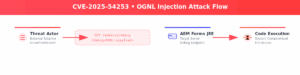
How Attackers are Exploiting This Vulnerability?
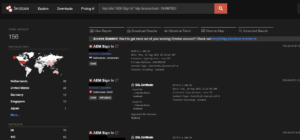
- Target Scanning
- Attackers mass-scan the Internet for (/adminui/debug) endpoints on port 443 or use tools like Shodan and Censys to find a vulnerable target.
Shodan Query:
http.title:”AEM Sign In” http.favicon.hash:-194997824
http.title:”AEM Sign In” port:4502
- Exploit Request Crafting
- Malicious HTTP GET requests are created, injecting arbitrary commands via the debug=OGNL:<payload> parameter.
Example: curl “http://127.0.0.1:4502/adminui/debug?debug=OGNL:whoami”
- Authentication Bypass
- No authentication or session token is needed; any inbound payload is parsed for OGNL by the vulnerable servlet.
- Achieving Remote Code Execution
- The server executes the injected command, granting the attacker control equivalent to the running Java process.
Visual Representation of OGNL Injection attack Flow
Automated Detection Using Nuclei and PoC Scripts
Security researchers and administrators can check if their Adobe AEM Forms on JEE instances are vulnerable to CVE-2025-54253 using this script..
Real-World Exploitation
- Exploit code is widely available; attacks are automated and opportunistic.
- First confirmed exploitations occurred within days of disclosure.
- Organizations are at risk for massive data exposure, persistence, and post-exploit ransomware or data theft campaigns.
Mitigation Strategies
Customers are requested to follow the mitigations and Remediations immediately.
- Patch Now
- Deploy Adobe’s fixed version: AEM Forms on JEE 6.5.0-0108 or later.
- Fully restrict the /adminui/debug endpoint.
- Harden Access
- Block access to all debug/dev endpoints via firewalls and reverse proxies.
- Ensure debug settings and servlets are disabled in all production deployments.
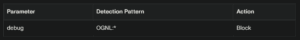
- Use WAF/IDS to detect/drop requests containing debug=OGNL:*.
Sample WAF Logic:
How To Detect If You Are Vulnerable To Exploited Instances Of CVE-2025-54253 ?
FireCompass has developed a multi-stage attack tree to detect vulnerable instances of CVE-2025-54253. By leveraging Continuous Automated Red Teaming (CART), FireCompass proactively scans attack surfaces, identifying weaknesses before attackers can exploit them.
FireCompass customers can execute a dedicated module to scan for Adobe AEM Forms on JEE Critical OGNL Injection (CVE-2025-54253). This ensures that security teams can take swift remediation actions to secure their infrastructure.
>>Want To Know If You Are Vulnerable to CVE-2025-54253?
Conclusion
CVE-2025-54253 highlights the risk posed by exposing debug features and failing to enforce input validation. As observed with recent supply chain and web RCE trends, even a single insecure endpoint can undermine entire organizational security postures. Patching alone is not sufficient—removal or restriction of legacy features, continuous monitoring, and defensive coding practices are mandatory.
FireCompass continuously scans and detects such vulnerabilities, providing real-time risk assessments and attack surface visibility. Don’t wait for attackers to exploit your systems — stay ahead with FireCompass Continuous Automated Red Teaming (CART).
Get started today!











