A Critical Remote Code Execution (RCE) vulnerability—CVE-2025-53770 (“ToolShell”)— is actively being exploited in the wild, targeting the on-premises SharePoint Servers. In this blog, we break down the technical details, real-world attack flow, and actionable mitigations.
What Is CVE-2025–53770?
CVE-2025-53770 is a critical vulnerability with CVSS score of 9.8. It is an unauthenticated RCE vulnerability affecting Microsoft SharePoint. This flaw stems from unsafe deserialization logic in legacy endpoints, to be specific in ToolPane.aspx, which attackers access using crafted HTTP POST requests with spoofed headers to bypass authentication. Successful exploitation grants threat actors remote code execution, webshell deployment, and the ability to extract cryptographic machine keys. Without prompt machine key rotation, attackers can maintain stealthy, repeated access even after patching.
Key Details:
-
- Severity: Critical
- Affected Systems: Microsoft SharePoint Server 2016, 2019, Subscription Edition (on-premises only). SharePoint Online is not affected.
- Exploitation: Attackers can craft malicious PUT requests to upload files outside the intended directory, leading to RCE.
- Vulnerable Module: ToolPane.aspx (legacy endpoint, unsafe .NET ViewState deserialization)
- Exploitation Status: Active, ongoing (attributed to Chinese APTs)
Root Cause:
- Inadequate Header Validation: The ToolPane.aspx endpoint failed to check the HTTP Referer header, allowing attackers to spoof authentication by providing a crafted Referer value (e.g., /_layouts/SignOut.aspx).
- Unsafe ViewState Deserialization: The endpoint performed .NET BinaryFormatter deserialization on attacker-supplied ViewState data without enforcing proper input validation or signing, enabling arbitrary code execution when malicious payloads were introduced.
- Insufficient Patch Coverage: Microsoft’s initial fixes for related vulnerabilities (CVE-2025-49704/49706) blocked specific attack vectors but did not strengthen header or session validation logic, which allowed bypasses and re-exploitation of the endpoint.
- Gadget Chain Abuse: Attackers crafted ViewState payloads containing gadget chains—series of .NET objects designed to trigger code execution upon deserialization—leveraging the unsafe deserialization environment.
How Can Attackers Exploit This Vulnerability?
The following is the Step-by-Step Attack Flow of how an attacker can exploit a SharePoint On-Prem instance.
- Target Scanning
- Attackers mass-scan the Internet for /_layouts/15/ToolPane.aspx endpoints on port 443 or use tools like Shodan and Censys to find a vulnerable target.
Shodan Query:
“MicrosoftSharePointTeamServices”
“SharePoint”
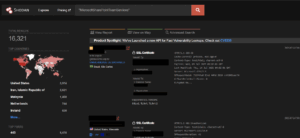
As of writing this blog, we observed over 16k SharePoint Server IPs are exposed to the Internet. But not all of them are vulnerable. Only SharePoint Server 2016, 2019, Subscription Edition are vulnerable to this attack.
- Exploit Request Crafting
- Attackers send an HTTP POST to endpoint /layouts/15/ToolPane.aspx?DisplayMode=Edit
- Include a spoofed Referer header: /_layouts/SignOut.aspx—this tricks SharePoint into treating the user as authenticated.
- POST body includes manipulated ViewState data, often carrying a serialized malicious .NET object payload.
- Attackers send an HTTP POST to endpoint /layouts/15/ToolPane.aspx?DisplayMode=Edit
- Bypassing Authentication & Gaining Code Execution
- SharePoint’s legacy code processes this POST request without further validation, deserializes attacker-supplied ViewState, and executes attacker-chosen code as w3wp (worker process).
- Webshell Planting & Persistence
- Attackers might try to upload a webshell (ex: spinstall0.aspx) into /LAYOUTS/.
- Attackers use the webshell to extract secrets including machine keys (ValidationKey and DecryptionKey), then delete or hide the shell to reduce risk of being detected. .
- Long-term Persistence
- With stolen machine keys, attackers continuously generate signed ViewState payloads, regaining RCE access even after the official Microsoft patch—unless admins rotate machine keys and restart IIS.
Automated Detection Using Nuclei and PoC Scripts
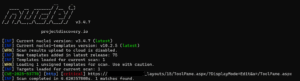
Security researchers and administrators can check if their Microsoft SharePoint servers are vulnerable to CVE-2025-53770 (“ToolShell”) using the Nuclei’s template which is available here. Also a script for detecting this vulnerability can be found.here.
Real-World Exploitation & APT Attribution
Attack Waves and Statistics
- First Exploitation: Microsoft says that the first exploitation was observed on 7th July, 2025;
- Spike after PoC release: Rapid acceleration post-block-release of exploit and PoCs by July 17-19.
- Known Impact: At least 75 organizations confirmed breached in the initial two weeks after the disclosure.
- Internet Exposure: Over 9,000 internet-facing vulnerable servers as of July 24, 2025.
- Sectors Targeted: Government, telecom, financial, education, and critical infrastructure are priorities.
Responsible Threat Actors (APTs):
Microsoft has reported that state-sponsored Chinese Advanced Persistent Threat (APT) groups began exploiting the ToolShell vulnerability weeks before a patch was released.
The following threat groups are believed to be actively exploiting CVE-2025-53770:
- Linen Typhoon (China state-sponsored)
- Violet Typhoon (China state-sponsored)
- Storm-2603 (China-based; medium confidence attribution)
These groups are known for conducting targeted campaigns against sectors like government, telecom, finance, and critical infrastructure.
Mitigation Strategies
Customers are requested to follow the mitigations and Remediations immediately.
Immediate Action Items:
- Patch Now: Deploy Microsoft’s July 2025 out-of-band security updates for all supported SharePoint servers.
- Rotate Machine Keys: Use PowerShell:
Set-SPMachineKey and Update-SPMachineKey for each web application.
Restart IIS (iisreset.exe) on all SharePoint servers to invalidate stolen tokens. - Remove Internet Exposure: Limit public access to SharePoint admin portals, enforce strict network segmentation, and deploy VPN/MFA.
- Anti-malware and AMSI: Enable and properly configure AMSI and Defender Antivirus for SharePoint content scanning.
How To Detect If You Are Vulnerable To Exploited Instances Of CVE-2025-53770 ?
FireCompass has developed a multi-stage attack tree to detect vulnerable instances of CVE-2025-53770. By leveraging Continuous Automated Red Teaming (CART), FireCompass proactively scans attack surfaces, identifying weaknesses before attackers can exploit them.
FireCompass customers can execute a dedicated module to scan for Microsoft SharePoint RCE (CVE-2025-53770). This ensures that security teams can take swift remediation actions to secure their infrastructure.
>>Want To Know If You Are Vulnerable to CVE-2025-53770?
Conclusion
CVE-2025–53770 highlights how a minor header validation oversight can lead to a machine-key theft, ViewState forgery, and full RCE. Patching alone is insufficient—key rotation is must to ensure SharePoint servers are fully secure. Organizations must act swiftly to patch affected systems, restrict access, and monitor for signs of exploitation.
FireCompass continuously scans and detects such vulnerabilities, providing real-time risk assessments and attack surface visibility. Don’t wait for attackers to exploit your systems — stay ahead with FireCompass Continuous Automated Red Teaming (CART).
Get started today!











