Critical CVEs: FortiOS, Microsoft Exchange, vSphere, SolarWinds and More
From February 12th to 16th, the FireCompass research team identified a huge number of CVEs that are high in severity and ransomware, botnets, and threat actors creating havoc. Some of the CVEs identified are of popular commercial products used by various industries and some new & well-known malware targeting industries for this week. In this, we will list important CVEs discovered as well as the list of malware, threat actors and botnets which were most active along with the CVEs that they were using in their campaigns.
List of Critical Vulnerabilities That Were Exploited – FireCompass Research :
- CVE-2020-12812, CVE-2024-21762 – FortiOS Multiple Vulnerability
- CVE-2020-0688, CVE-2021-34523, CVE-2024-21410 – Microsoft Exchange Multiple Vulnerability
- CVE-2021-21972 – vSphere Client
- CVE-2023-35188 – SolarWinds Platform
- CVE-2024-21364, CVE-2024-21376, CVE-2024-20667 – Microsoft Azure Multiple Vulnerability
- CVE-2024-21413, CVE-2024-21378 – Microsoft Outlook Multiple Vulnerability
-> (Request Demo) 10 X Pen Testing Frequency & 100% Asset Coverage
Detailed Analysis: Vulnerabilities
CVE-2020-12812, CVE-2024-21762 – FortiOS Multiple Vulnerability:
CVE-2020-12812
CVE-2020-12812 is a vulnerability in FortiOS SSL VPN that allows users to bypass two-factor authentication (2FA) by simply changing the case of their username. This vulnerability exists because of inconsistent case-sensitivity handling between local and remote authentication methods. For example, if a user’s username is stored in lowercase on the local system but uppercase on the remote authentication server, they can bypass 2FA by logging in with a mixed-case username (e.g., “jUsEr” instead of “user”). This vulnerability affects FortiOS versions 6.4.0, 6.2.0 to 6.2.3, and 6.0.9 and below. It is recommended to upgrade to FortiOS 6.4.1 or later, 6.2.4 or later, or 6.0.10 or later to address this vulnerability.
CVE-2024-21762
CVE-2024-21762 is a critical vulnerability in Fortinet FortiOS and FortiProxy software that exposes devices to attackers. This vulnerability, caused by an out-of-bounds write issue, allows attackers to remotely execute arbitrary code or commands on affected devices by sending specially crafted requests. This means attackers could potentially take full control of your device and use it for malicious purposes. If you use Fortinet FortiOS or FortiProxy, it’s crucial to update to the latest patched version immediately to address this vulnerability and protect your devices.
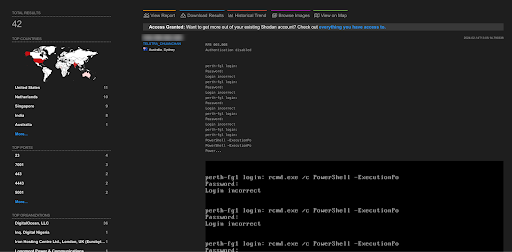
A total of 42 endpoints of FortiOS are exposed on the Shodan.
CVE-2021-21972 – vSphere Client
A critical vulnerability in VMware vCenter Server (versions 7.x before 7.0 U1c, 6.7 before 6.7 U3l, and 6.5 before 6.5 U3n) and VMware Cloud Foundation (versions 4.x before 4.2 and 3.x before 3.10.1.2) allows remote attackers with network access to port 443 to execute arbitrary code with unrestricted privileges on the underlying operating system. This vulnerability exists due to an unauthenticated remote code execution flaw within a vCenter Server plugin.
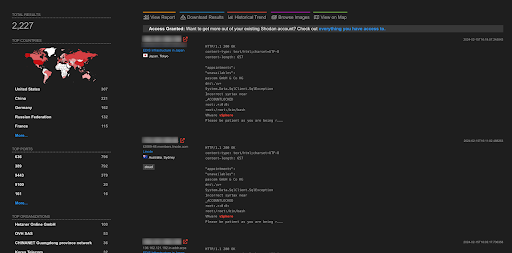
A total of more than 2K endpoints of vSphare are exposed on the Shodan.
CVE-2023-35188 – SolarWinds Platform
CVE-2023-35188 exposes a critical security risk in SolarWinds Platform versions up to 2023.4.2. It allows attackers to remotely execute malicious code within the platform if they have valid user credentials. This vulnerability arises from a flaw in how the platform handles SQL statements, specifically within the “create” function. While user authentication is required for exploitation, attackers could potentially leverage stolen credentials or social engineering tactics to gain access. Upgrading to the latest SolarWinds Platform version (2023.4.3 or later) is essential to mitigate this risk.
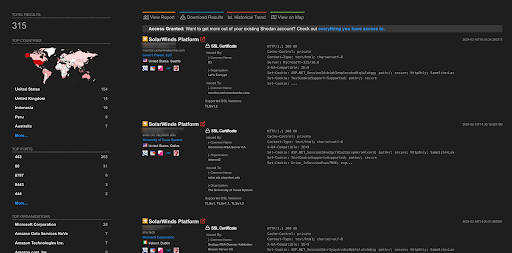
A total of 315 endpoints of SolarWinds Platform are exposed on the Shodan.
>> [Request RECON Demo] - Reconnaissance Techniques As Threat Actors
CVE-2024-21364, CVE-2024-21376, CVE-2024-20667 – Microsoft Azure Multiple Vulnerability:
CVE-2024-21364
CVE-2024-21364 is a recently discovered critical vulnerability in Microsoft Azure Site Recovery that allows attackers to escalate their privileges on the system. While specific details of the exploit are still emerging, it’s crucial to prioritize patching your Azure Site Recovery instance immediately to prevent potential compromise.
CVE-2024-21376
CVE-2024-21376 is a critical vulnerability in Microsoft Azure Kubernetes Service (AKS) affecting Confidential Containers (AKSCC). It allows attackers to remotely execute malicious code within AKS, potentially granting them unrestricted access to sensitive data and resources. This vulnerability arises due to improper isolation between untrusted AKS nodes and AKSCC, enabling attackers to exploit specific configurations and gain control over confidential guests and containers. The vulnerability requires no authentication and carries a CVSSv3 score of 9.0, indicating a severe risk. Microsoft has released security patches, and immediate patching is crucial to mitigate this vulnerability.
CVE-2024-20667
A critical vulnerability (CVE-2024-20667) exists in Azure DevOps Server versions 2019.1.2, 2020.1.2, and 2022.1, allowing attackers to remotely execute malicious code on affected servers. This vulnerability, categorized as “remote code execution,” grants attackers complete control over the server, enabling them to steal sensitive data, disrupt operations, or install malware.The vulnerability stems from an issue with how the server processes specific requests. Exploiting this vulnerability requires no user interaction or authentication, making it highly dangerous.
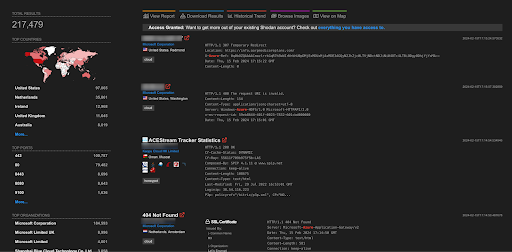
A total of more than 217K endpoints of Azure are exposed on the Shodan.
-> Hackers Won't Wait For Your Next Pen Test: Know Automated Continuous Pen Test
CVE-2024-21413, CVE-2024-21378 – Microsoft Outlook Multiple Vulnerability:
CVE-2024-21413
CVE-2024-21413 is a critical remote code execution vulnerability affecting Microsoft Outlook versions included in Microsoft Office 2019, Microsoft 365 Apps for Enterprise, Microsoft Office LTSC 2021, and Microsoft Office 2016. It allows attackers to gain high privileges on a vulnerable system, potentially leading to data theft, malware installation, or complete system compromise.The vulnerability arises from a flaw in how Outlook handles malicious links that bypass the Protected View Protocol. This enables attackers to leak local NTLM credential information and ultimately achieve remote code execution (RCE) without requiring any user interaction or specific privileges.
CVE-2024-21378
A critical vulnerability (CVE-2024-21378) exists in Microsoft Outlook, potentially affecting various versions within Microsoft Office suites (2019, 365 Apps, LTSC 2021, 2016). This vulnerability allows attackers to remotely execute malicious code on your system, granting them complete control and potentially leading to data breaches, malware installation, or system disruption.
A total of 698 endpoints of Microsoft Outlook are exposed on the Shodan.
Blog By
Author: Debdipta Halder
Assisted By: Soumyanil Biswas, Faran Siddiqui, Anirban Bain
About FireCompass:
FireCompass is a SaaS platform for Continuous Automated Pen Testing, Red Teaming and External Attack Surface Management (EASM). FireCompass continuously indexes and monitors the deep, dark and surface webs using nation-state grade reconnaissance techniques. The platform automatically discovers an organization’s digital attack surface and launches multi-stage safe attacks, mimicking a real attacker, to help identify breach and attack paths that are otherwise missed out by conventional tools.
Feel free to get in touch with us to get a better view of your attack surface.










