This week from November 13 to November 17, Firecompass research identified a huge number of CVEs that are high in severity and ransomware, botnets, and threat actors creating havoc. Some of the CVEs identified are of popular commercial products used by variants of industries and somenew & well known malwares targeting industries for this week. In this, we will list important CVEs discovered as well as list of malware, threat actors and botnets which were most active along with the CVEs that they were using in their campaigns.
Also this week there was Microsoft Patch Tuesday of the month as well
The Key Vulnerabilities That FireCompass Has Focused On Are:
- CVE-2023-26205 – FortiADC Automation Privilege Escalation
- CVE-2023-34991 – Fortinet FortiWLM SQL Command Injection
- Microsoft Exchange Vulnerabilities
- CVE-2023-36425 – Microsoft DFS RCE
- CVE-2023-34060 – VMWare Cloud Director Authentication Bypass
- CVE-2023-36437 – Azure DevOps Server RCE
- CVE-2023-5189 – Ansible Path Traversal
- CVE-2023-36402 – Microsoft WDAC OLE DB RCE
- CVE-2023-41699 – Payara Server URL Redirection
- CVE-2023-48365 – Qlik Sense Enterprise
The Key Malwares And Threat Actors That FireCompass Has Focused On Are:
- CVE-2023-4966 – NetScaler ADC and NetScaler Gateway
- CVE-2023-27350 – PaperCut NG
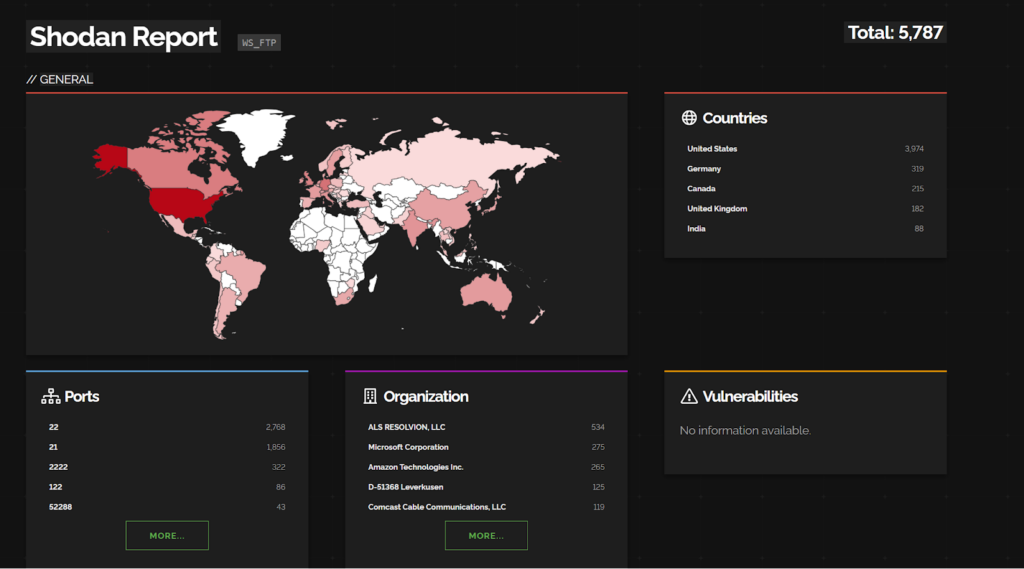
- CVE-2023-40044 and CVE-2023-42657 – WS_FTP Server
- CVE-2023-42115, CVE-2023-42116 and CVE-2023-42117, – Exim
- CVE-2023-44487 – HTTP/2
- CVE-2023-41763 – Skype
- CVE-2023-22515 – Atlassian -Confluence Data Center & Server
- CVE-2023-20101 – Cisco Emergency Responder
- CVE-2020-1472 – Netlogon secure channel connection
-> Hackers Won't Wait For Your Next Pen Test: Know Automated Continuous Pen Test
Know The Vulnerabilities Impacting Key Industries and Companies:
CVE-2023-26205 – FortiADC Automation Privilege Escalation
FortiADC Automation version 7.1.0 through 7.1.2, 7.0 all versions, 6.2 all versions, 6.1 all versions may allow an authenticated low-privileged attacker to escalate their privileges to super_admin via a specific crafted configuration of fabric automation CLI script.
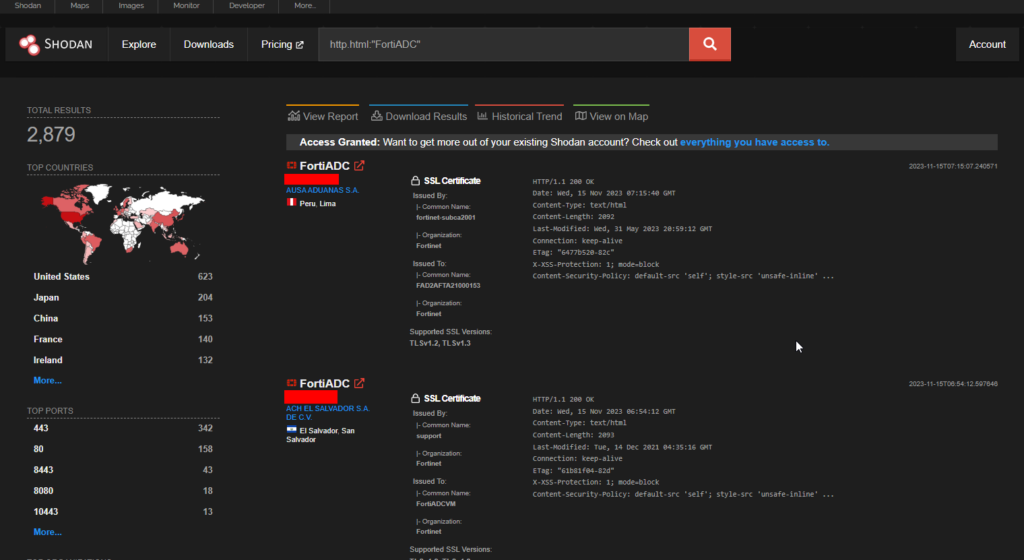
Shodan shows 2879 endpoints and the USA has the most number of them.
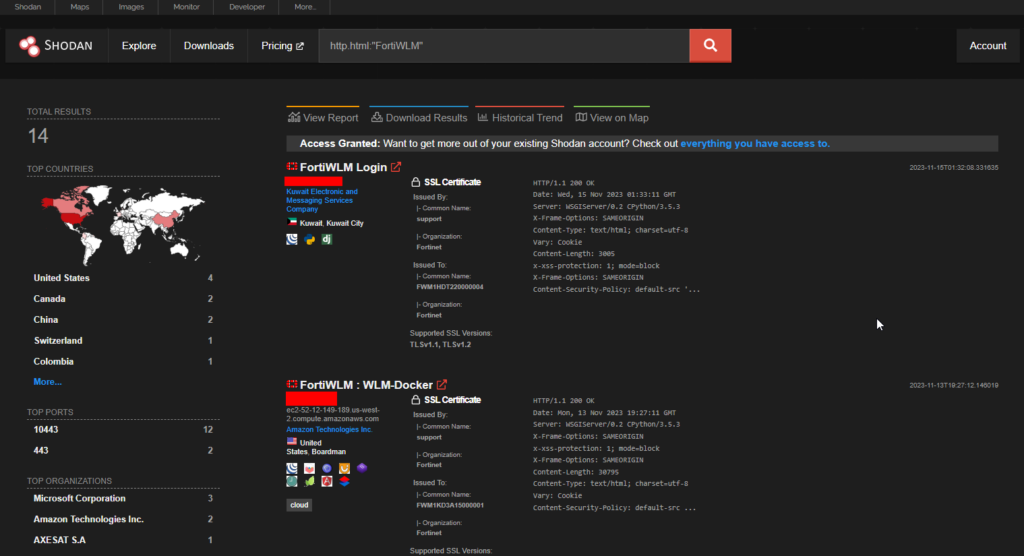
CVE-2023-34991 – Fortinet FortiWLM SQL Command Injection
A improper neutralization of special elements used in an sql command (‘sql injection’) in Fortinet FortiWLM version 8.6.0 through 8.6.5 and 8.5.0 through 8.5.4 and 8.4.0 through 8.4.2 and 8.3.0 through 8.3.2 and 8.2.2 allows attacker to execute unauthorized code or commands via a crafted http request.
>> Find Critical Risks in 72 Hours & Continuous Risk Hunting (Request Demo)
Microsoft Exchange Server Vulnerabilities
This on 14th November, 2023 – Tuesday was the Microsoft Patch Tuesday where they disclosed several numbers of vulnerabilities. One of them being the popular Microsoft Exchange Server which is a prime target for threat actors. Four vulnerabilities were released, here is the list.
- CVE-2023-36035 – Microsoft Exchange Server Spoofing Vulnerability
- CVE-2023-36039 – Microsoft Exchange Server Spoofing Vulnerability
- CVE-2023-36050 – Microsoft Exchange Server Spoofing Vulnerability
- CVE-2023-36439 – Microsoft Exchange Server Remote Code Execution
CVE-2023-36425 – Microsoft DFS RCE
From the patch Tuesday, a remote code execution vulnerability is present in Microsoft Distributed File System(DFS).
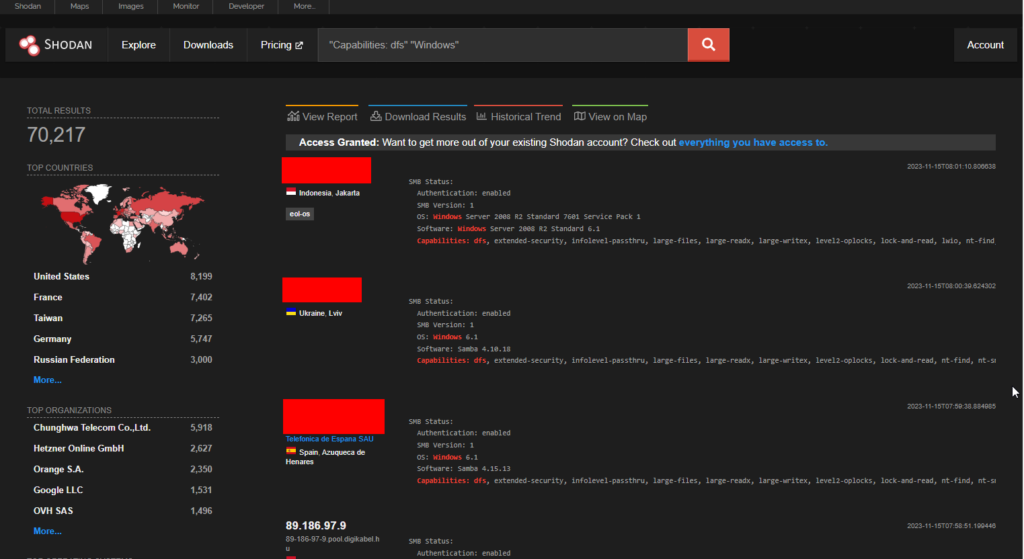
Shodan displays more than 70k endpoints. Countries like the USA, France and Taiwan have the highest number of endpoints
>> [Request RECON Demo] - Reconnaissance Techniques As Threat Actors
CVE-2023-34060 – VMWare Cloud Director Authentication Bypass
VMware Cloud Director Appliance contains an authentication bypass vulnerability in case of VMware Cloud Director Appliance on version 10.5. A malicious actor with network access to the appliance can bypass login restrictions when authenticating on port 22 (ssh) or port 5480 (appliance management console).
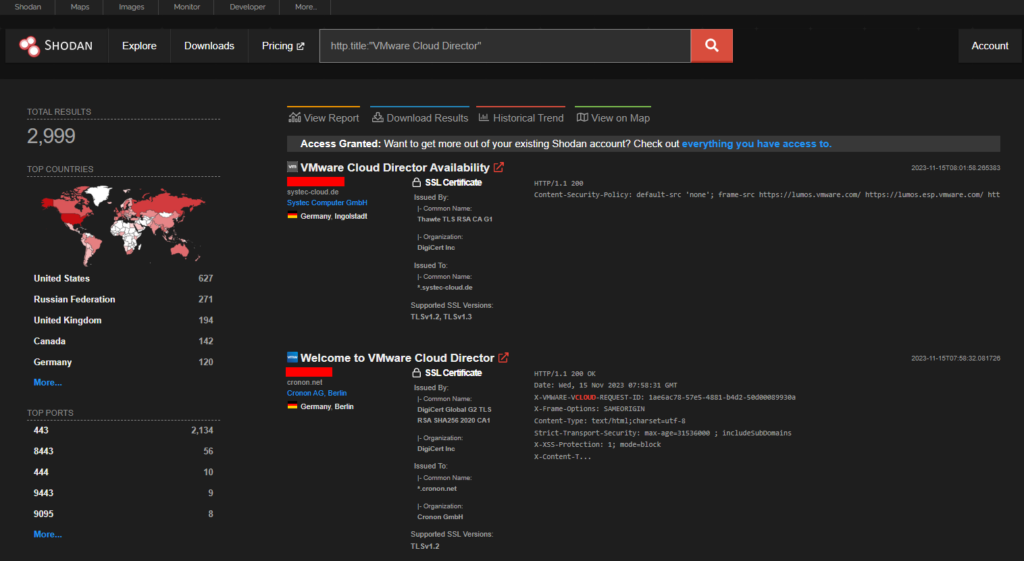
Approximately 3000 endpoints are displayed in Shodan.
-> [Request Demo] - Get the Hacker’s View Of Your Attack Surface
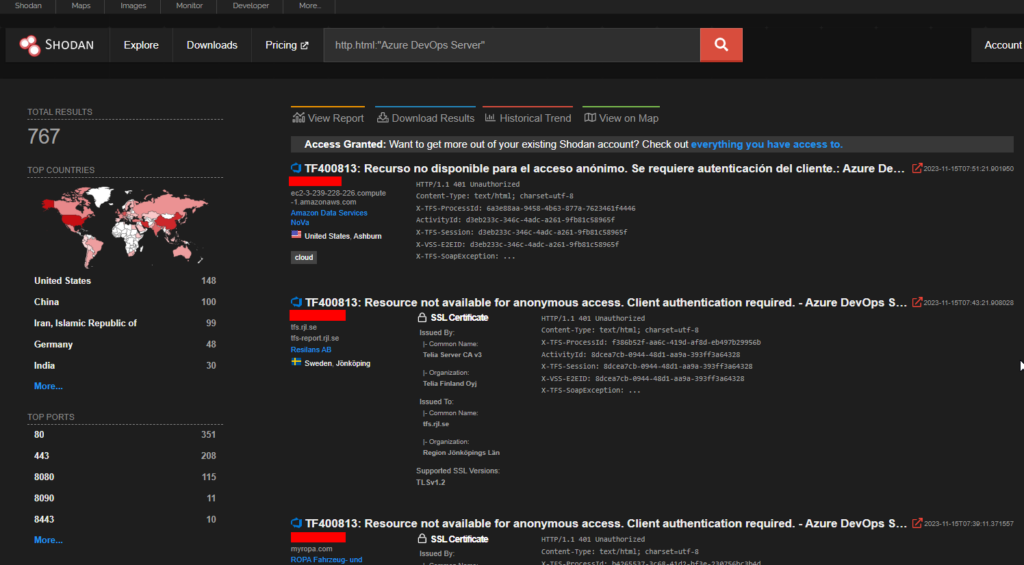
CVE-2023-36437 – Azure DevOps Server RCE
From patch Tuesday, Azure DevOps Server is vulnerable to remote code execution.
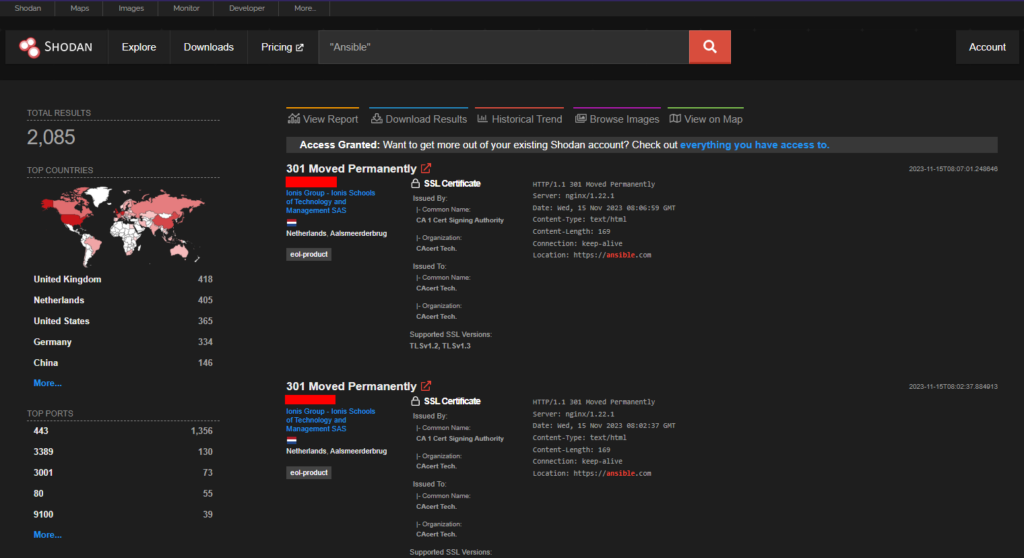
CVE-2023-5189 – Ansible Path Traversal
A path traversal vulnerability exists in Ansible when extracting tarballs. An attacker could craft a malicious tarball so that when using the galaxy importer of Ansible Automation Hub, a symlink could be dropped on the disk, resulting in files being overwritten.
>> (Learn More) "Automated Pen Testing Significantly Improved The Depth & Breadth Of Testing" - Ed Adams, Security Innovation
CVE-2023-36402 – Microsoft WDAC OLE DB For SQL Server RCE
Microsoft WDAC OLE DB provider for SQL Server is vulnerable to remote code execution
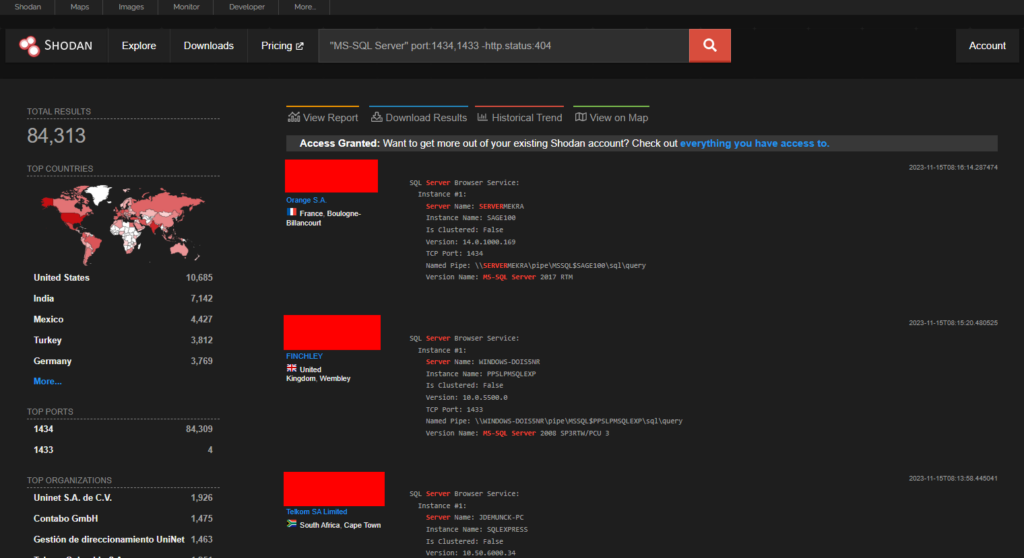
Shodan shows approximately 84,000 endpoints. The United States has the most number of endpoints.
CVE-2023-41699 – Payara Server URL Redirection
Payara Server is an open-source application server from GlassFish which has URL Redirection to Untrusted Site (‘Open Redirect’) vulnerability in Payara Platform Payara Server, Micro and Embedded (Servlet Implementation modules) allows Redirect Access to Libraries.
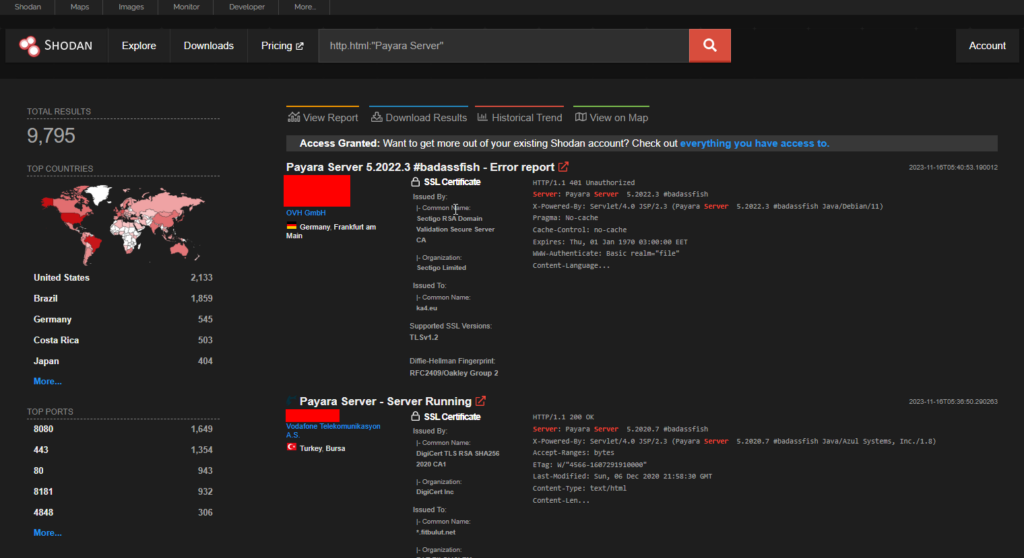
The USA has the highest number of endpoints.
-> (Request Demo) 10 X Pen Testing Frequency & 100% Asset Coverage
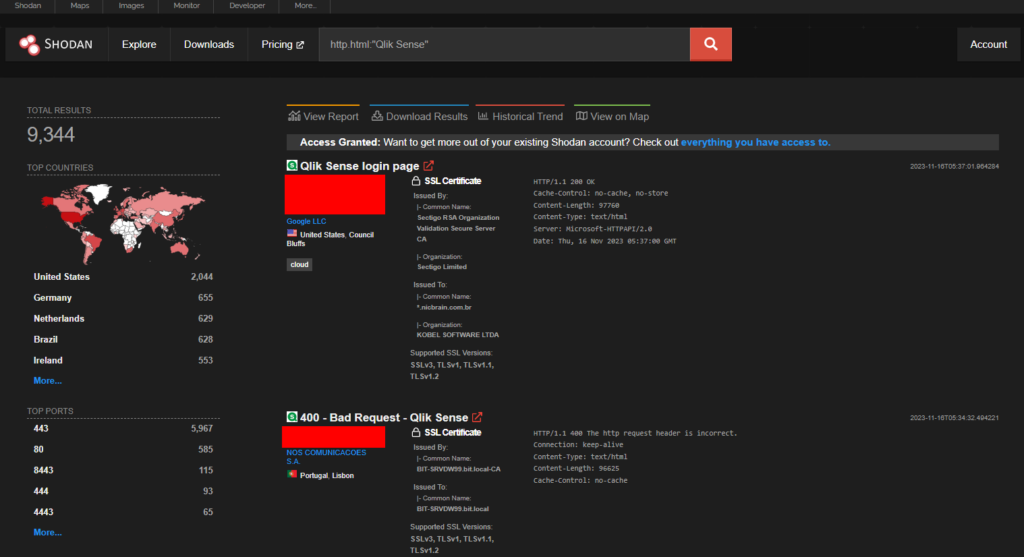
CVE-2023-48365 – Qlik Sense Enterprise RCE
Qlik Sense Enterprise is vulnerable to improper validation of HTTP headers, a remote attacker is able to elevate their privilege by tunneling HTTP requests, allowing them to execute HTTP requests on the backend server that hosts the repository application.
Know The Threat Actors Impacting Key Industries and Companies:
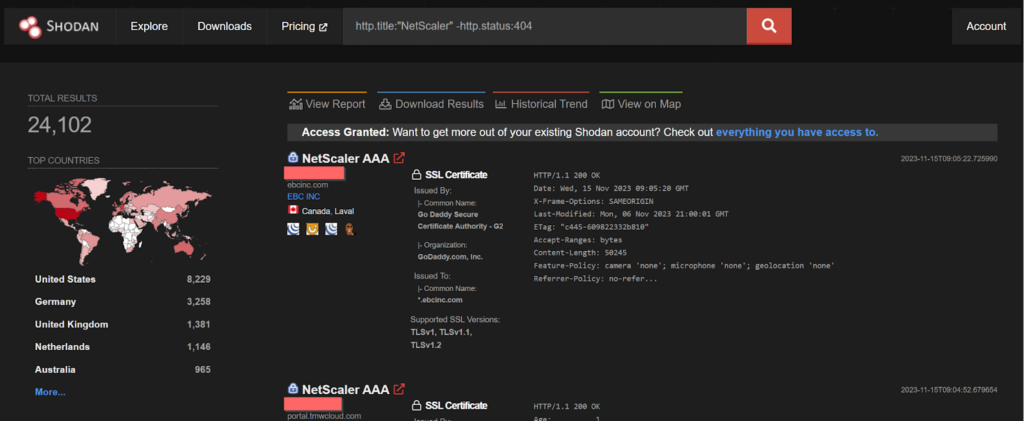
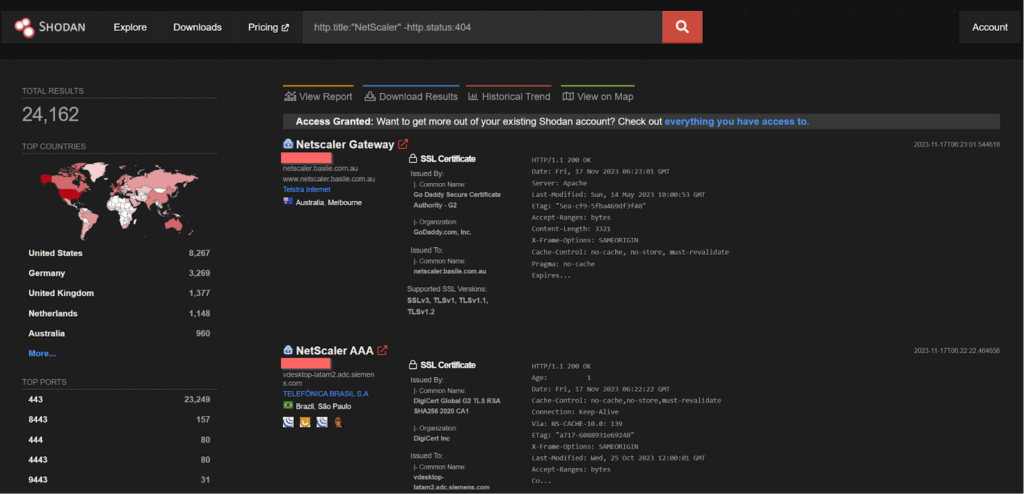
CVE-2023-4966 – LockBit Ransomware Gang
Sensitive Information Disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA virtual server. This vulnerability is found to be exploited by the LockBit ransomware gang.
POC of the above vulnerabilty:
https://github.com/mlynchcogent/CVE-2023-4966-POC
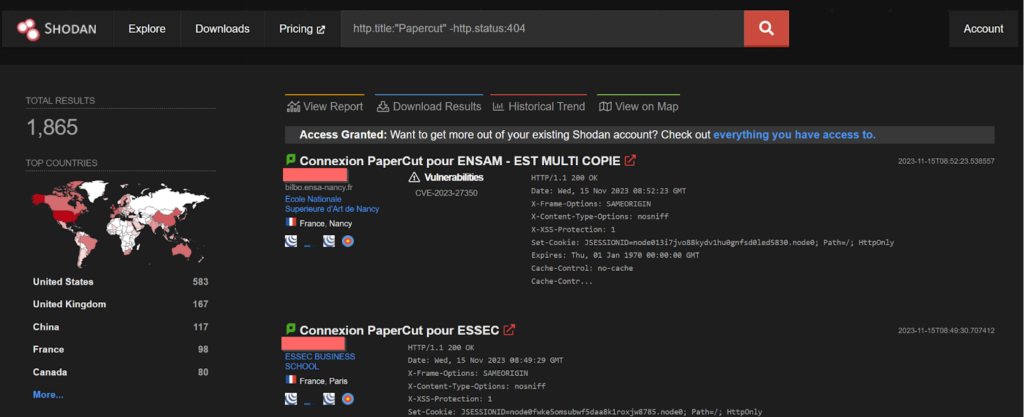
CVE-2023-27350 – MuddWater Iranian APT
This vulnerability allows remote attackers to bypass authentication on affected installations of PaperCut NG. Authentication is not required to exploit this vulnerability. The specific flaw exists within the SetupCompleted class. The issue results from improper access control. This vulnerability is found to be exploited by the MuddWater Iranian APT.
POC of the vulnerbility:
https://packetstormsecurity.com/files/172512/PaperCut-NG-MG-22.0.4-Remote-Code-Execution.html
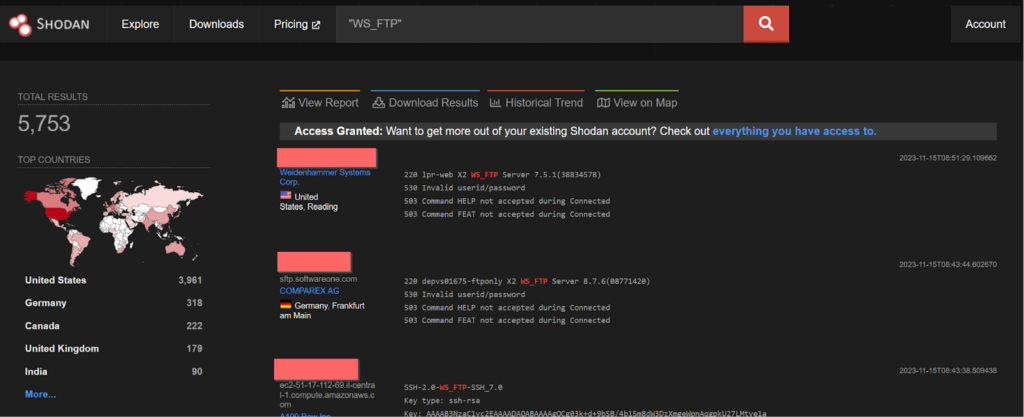
CVE-2023-40044 and CVE-2023-42657 – Dark Pink APT
In WS_FTP Server versions prior to 8.7.4 and 8.8.2, a pre-authenticated attacker could leverage a .NET deserialization vulnerability in the Ad Hoc Transfer module to execute remote commands on the underlying WS_FTP Server operating system and
a directory traversal vulnerability was discovered. An attacker could leverage this vulnerability to perform file operations on files and folders outside of their authorized WS_FTP folder path. Attackers could also escape the context of the WS_FTP Server file structure and perform the same level of operations (delete, rename, rmdir, mkdir) on file and folder locations on the underlying operating system. These vulnerabilities are found to be exploited by Dark Pink APT group.
PoC for CVE-2023-40044:
http://packetstormsecurity.com/files/174917/Progress-Software-WS_FTP-Unauthenticated-Remote-Code-Execution.html
CVE-2023-42115, CVE-2023-42116 and CVE-2023-42117 – Dark Pink APT
An out-of-bounds write flaw exists in Exim within the smtp service, which listens on TCP port 25 by default and another vulnerability was found in Exim within the handling of NTLM challenge requests. The issue results from the lack of proper validation of the length of user-supplied data prior to copying it to a fixed-length stack-based buffer. An attacker can leverage this vulnerability to execute code in the context of the service account or current process. In all of these cases, authentication is not required to exploit this vulnerability. All these vulnerabilities are found to be again exploited by Dark Pink APT group.
CVE-2023-44487 – Dark Pink APT
This vulnerability allows HTTP/2 protocol to allow a denial of service (server resource consumption) because request cancellation can reset many streams quickly. This vulnerability has been found to be again exploited by Dark Pink APT group.
CVE-2023-41763 – Dark Pink APT
Skype for Business Elevation has suffered a serious vulnerability which allows it to perform Privilege Escalation Remotely. This vulnerability has been found to be again exploited by Dark Pink APT group.
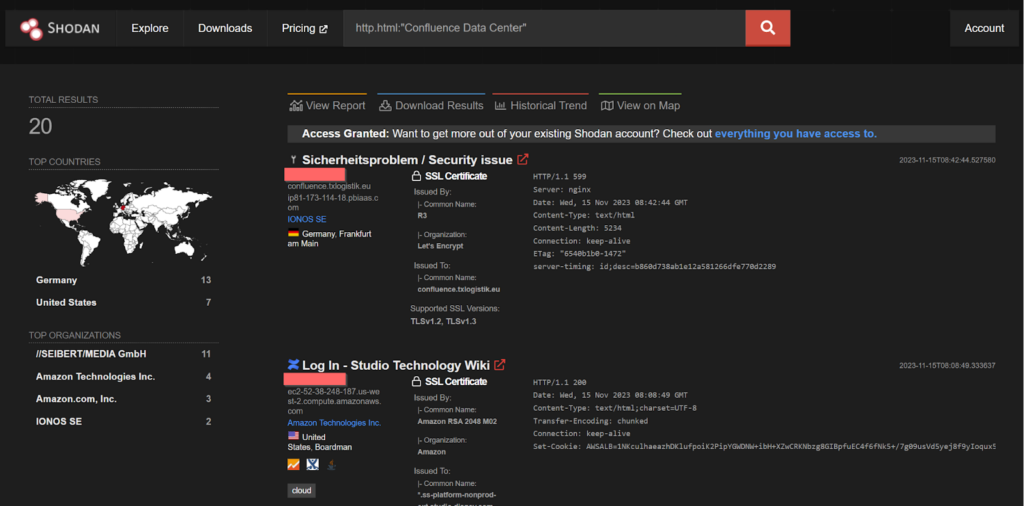
CVE-2023-22515 – Dark Pink APT
Atlassian has been made aware of an issue reported by a handful of customers where external attackers may have exploited a previously unknown vulnerability in publicly accessible Confluence Data Center and Server instances to create unauthorized Confluence administrator accounts and access Confluence instances. This vulnerability has been found to be again exploited by Dark Pink APT group.
POC the vulnerability:
http://packetstormsecurity.com/files/175225/Atlassian-Confluence-Unauthenticated-Remote-Code-Execution.html
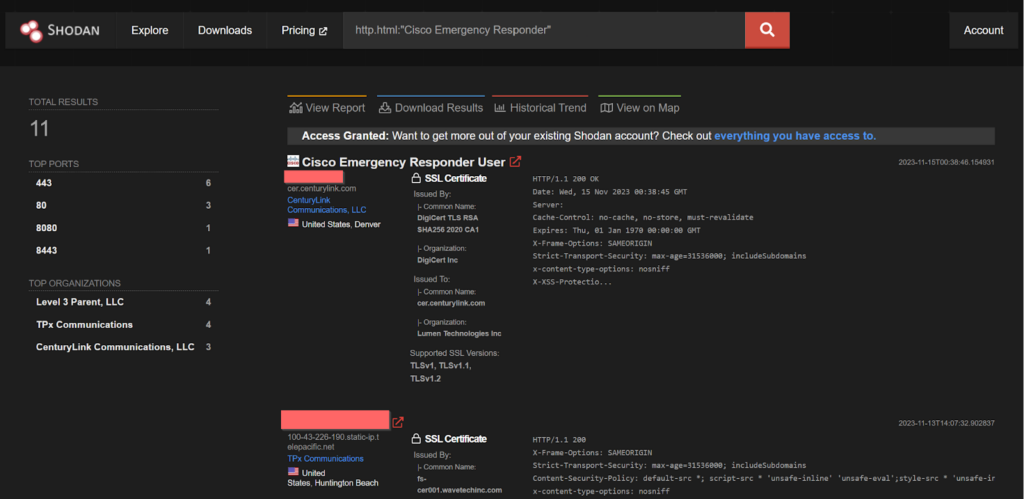
CVE-2023-20101 – Dark Pink APT
A vulnerability in Cisco Emergency Responder could allow an unauthenticated, remote attacker to log in to an affected device using the root account, which has default, static credentials that cannot be changed or deleted. This vulnerability is due to the presence of static user credentials for the root account that are typically reserved for use during development. An attacker could exploit this vulnerability by using the account to log in to an affected system. This vulnerability has been found to be again exploited by Dark Pink APT group.
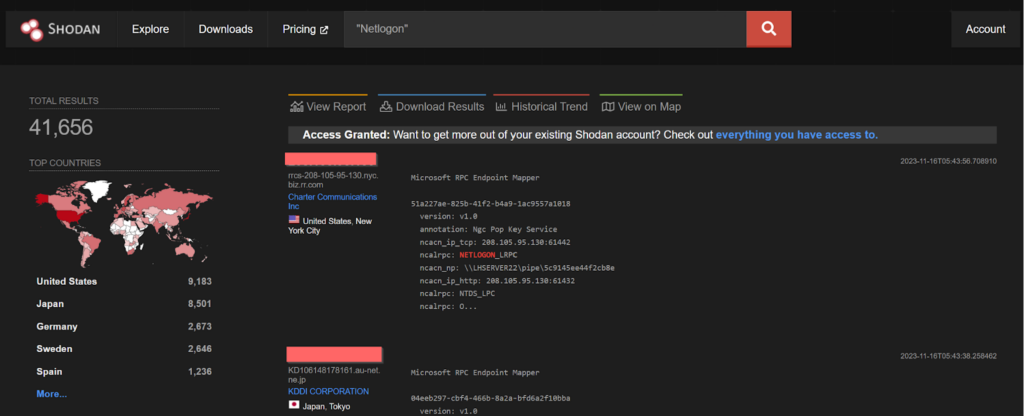
CVE-2020-1472 – Rhysida Ransomware Gang
An elevation of privilege vulnerability exists in Netlogon secure channel connection, when an attacker establishes a vulnerable Netlogon secure channel connection to a domain controller, using the Netlogon Remote Protocol (MS-NRPC), aka ‘Netlogon Elevation of Privilege Vulnerability’. This vulnerability was found to be exploited by the Rhysida ransomware gang.
The POC of the above vulnerability:
https://github.com/SecuraBV/CVE-2020-1472
CVE-2023-4966 – Medusa Ransomware
Sensitive information disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA virtual server. This vulnerability was found to be actively exploited by Medusa ransomware group.
The POC of the above vulnerability:
https://github.com/mlynchcogent/CVE-2023-4966-POC
By: Firecompass Research Team – Debdipta Halder, Soumyanil Biswas, Faran Siddiqui, Anirban Bain
About FireCompass:
FireCompass is a SaaS platform for Continuous Automated Pen Testing, Red Teaming and External Attack Surface Management (EASM). FireCompass continuously indexes and monitors the deep, dark and surface webs using nation-state grade reconnaissance techniques. The platform automatically discovers an organization’s digital attack surface and launches multi-stage safe attacks, mimicking a real attacker, to help identify breach and attack paths that are otherwise missed out by conventional tools.
Feel free to get in touch with us to get a better view of your attack surface.










