This week from November 27 to December 02, Firecompass’s research team identified a huge number of CVEs that are high in severity and ransomware, botnets, and threat actors creating havoc. Some of the CVEs identified are of popular commercial products used by variants of industries and somenew & well known malwares targeting industries for this week. In this, we will list important CVEs discovered as well as list of malware, threat actors and botnets which were most active along with the CVEs that they were using in their campaigns. Also this week there was Microsoft Patch Tuesday of the month as well
The Key Vulnerabilities That FireCompass Has Focused On Are:
- CVE-2023-49103 – OwnCloud Sensitive File Disclosure.
- CVE-2022-41678 – Apache ActiveMQ Remote Code Execution.
- CVE-2023-40056 – SolarWinds Platform Remote Code Execution.
- CVE-2023-45539 – HAProxy Sensitive Information Disclosure.
- CVE-2023-48193 – JumpServer Remote Code Execution.
- CVE-2023-6217 – Progress MoveIT Remote Code Execution.
- CVE-2023-6218 – Progress MoveIT Privilege Escalation.
The Key Malwares And Threat Actors That FireCompass Has Focused On Are:
- CVE-2023-41265 – Qlik Sense Enterprise Remote Privilege Escalation
- CVE-2023-41266 – Qlik Sense Enterprise Unauthenticated RCE
-> Hackers Won't Wait For Your Next Pen Test: Know Automated Continuous Pen Test
Know The Vulnerabilities Impacting Key Industries and Companies:
CVE-2023-49103 – OwnCloud Sensitive File Disclosure
An issue was discovered in OwnCloud GraphAPI on versions before 0.2.1 and 0.3.1. The API reveals the PHPINFO() file which includes environment variables of the webserver, sensitive data such as the ownCloud admin password, mail server credentials, and license key.
POC – https://github.com/creacitysec/CVE-2023-49103
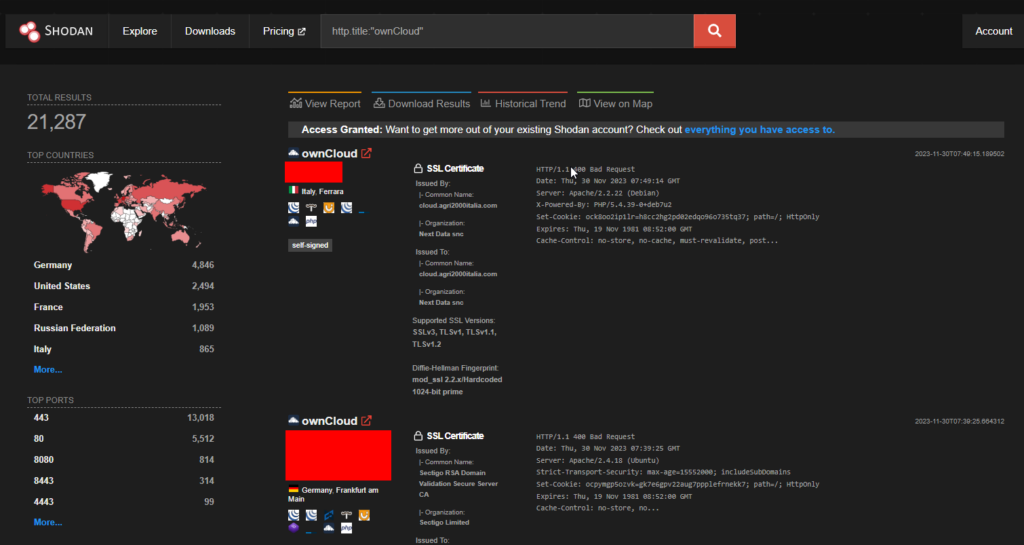
Approximately 21 thousand endpoints of OwnCloud’s servers are exposed on the internet
CVE-2022-41678 – Apache ActiveMQ Remote Code Execution
The Apache ActiveMQ is vulnerable to remote code execution.
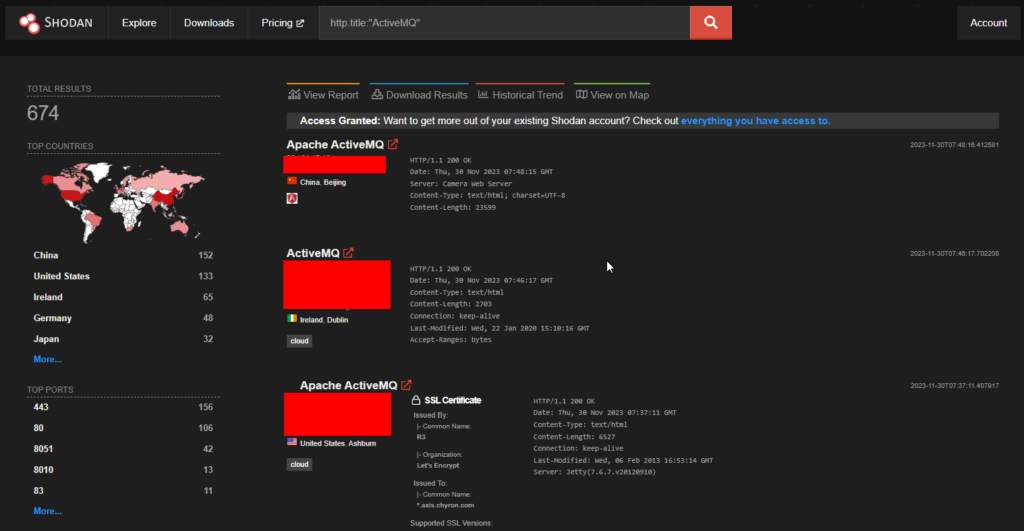
Around 674 endpoints are exposed on shodan.
>> Find Critical Risks in 72 Hours & Continuous Risk Hunting (Request Demo)
CVE-2023-40056 – SolarWinds Platform Remote Code Execution
In SolarWinds Platform, there is a SQL injection vulnerability which lets a low privileged attacker inject malicious SQL queries leading to remote code execution.
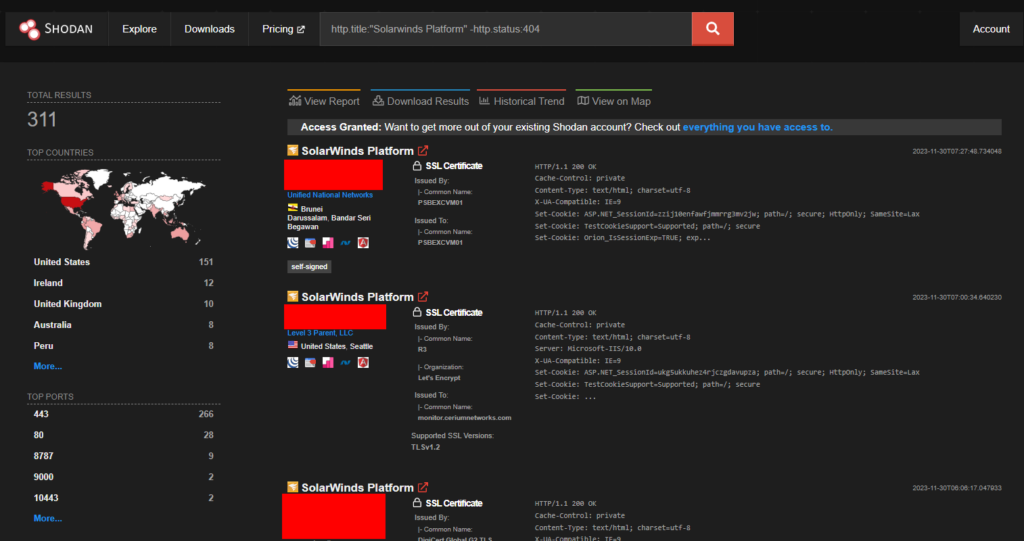
Approximately 311 endpoints of SolarWinds are exposed on shodan.
CVE-2023-45539 – HAProxy Sensitive Information Disclosure
HAProxy is an open source software that provides high availability load balancing and reverse proxy for TCP and HTTP based applications. It has a vulnerability in versions before 2.8.2 that is vulnerable to sensitive information disclosure.
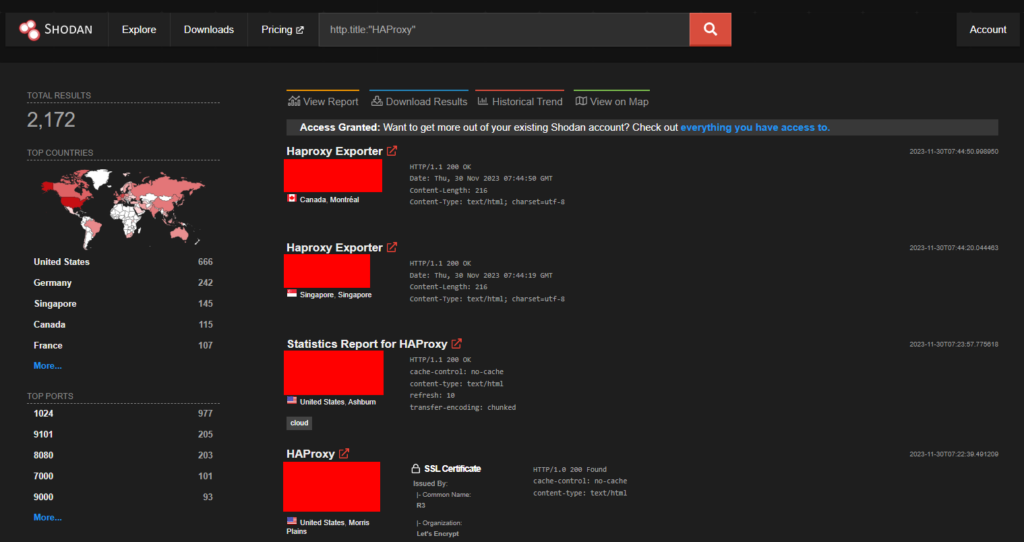
Over 2 thousand endpoints for HAProxy are exposed on Shodan.
>> [Request RECON Demo] - Reconnaissance Techniques As Threat Actors
CVE-2023-48193 – JumpServer Remote Code Execution
The JumpServer version GPL v3.8.0 is vulnerable to insecure permission vulnerability which allows remote attackers to execute arbitrary code via bypassing command filtering function.POC – https://github.com/296430468/lcc_test/blob/main/jumpserver_BUG.md
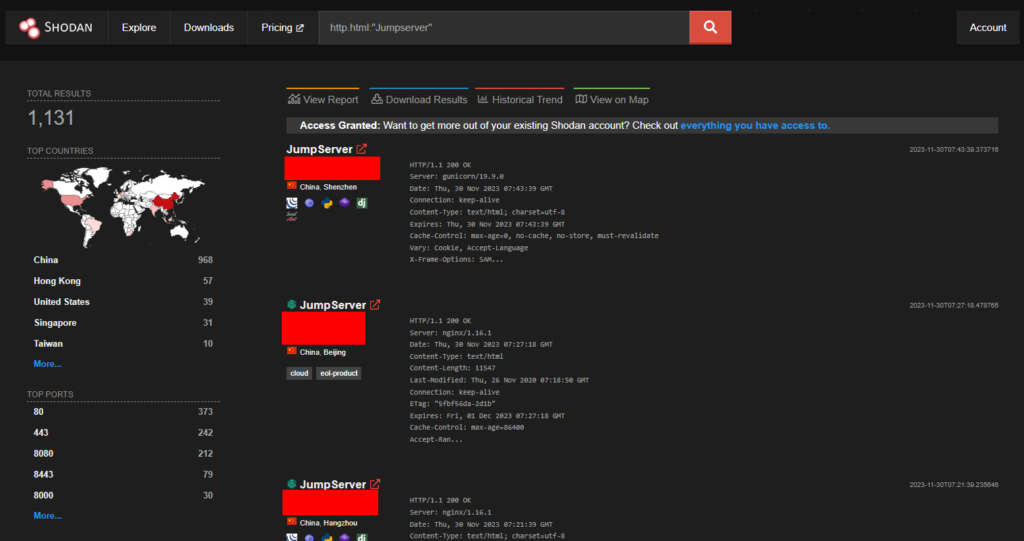
Over one thousand endpoints for JumpServer are exposed on Shodan.
-> [Request Demo] - Get the Hacker’s View Of Your Attack Surface
Progress MoveIT Vulnerabilities
The infamous Progress MoveIT which has been a prime target for ransomware throughout the whole year, this week it released two CVEs
- CVE-2023-6217 – Reflected cross site scripting vulnerability where attacker can craft a malicious payload leading to remote code execution.
- CVE-2023-6218 – Privilege escalation vulnerability where it is possible for group administrators to elevate a group member’s permissions to the role of an organization administrator.
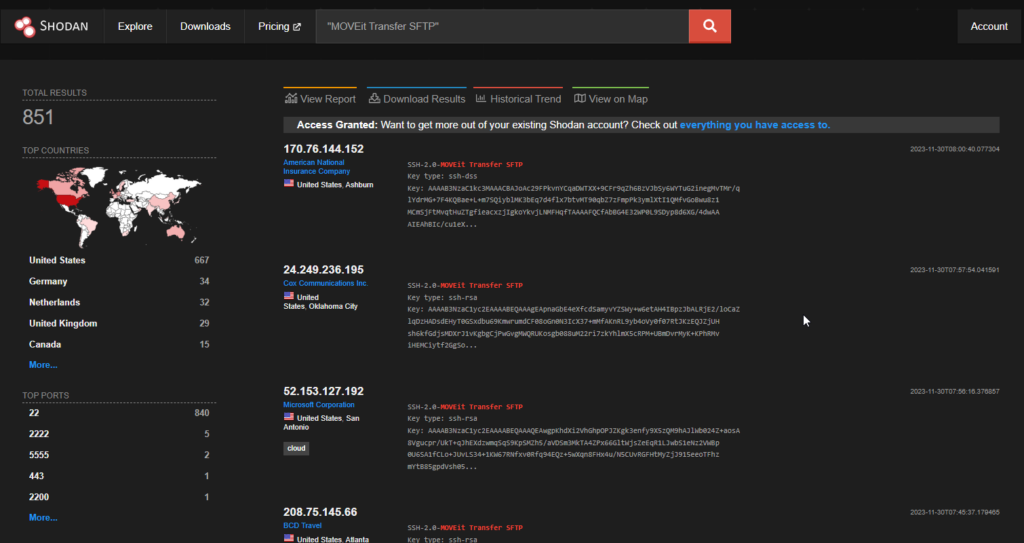
Around 851 endpoints of MoveIT are exposed on Shodan.
>> (Learn More) "Automated Pen Testing Significantly Improved The Depth & Breadth Of Testing" - Ed Adams, Security Innovation
Important Weekly Threat Actors
CVE-2023-41265, CVE-2023-41266 – Cactus ransomware
CVE-2023-41265, an HTTP Request Tunneling vulnerability found in Qlik Sense Enterprise for Windows which allows a remote attacker to elevate their privilege by tunneling HTTP requests in the raw HTTP request. This allows them to send requests that get executed by the backend server hosting the repository application.
CVE-2023-41265 allows a path traversal vulnerability found in Qlik Sense Enterprise for Windows, allowing an unauthenticated remote attacker to generate an anonymous session. This allows them to transmit HTTP requests to unauthorized endpoints.
Both of these vulnerabilities are found to be targeted by Cactus ransomware group.
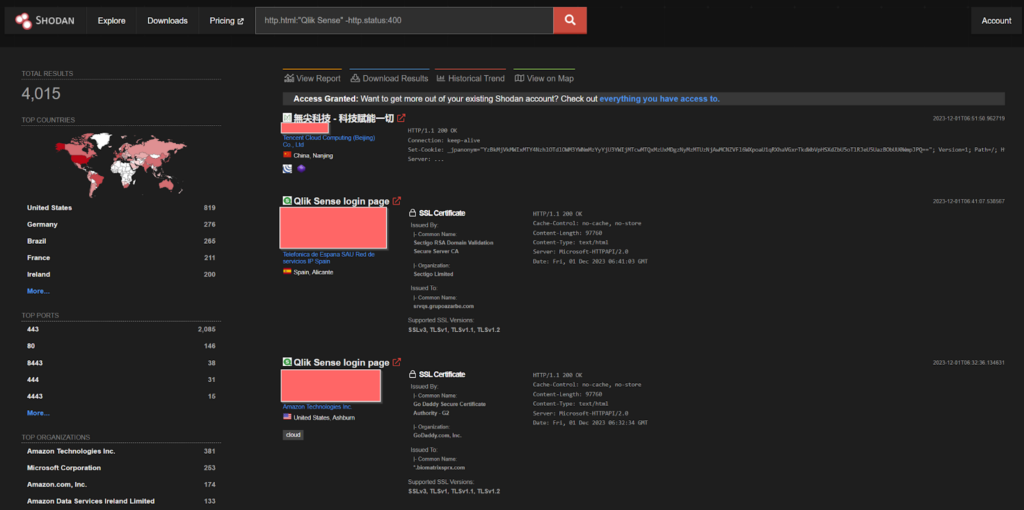
Around 4K Endpoints which are exposed, found in Shodan.
By: Firecompass Research Team – Debdipta Halder, Soumyanil Biswas, Faran Siddiqui, Anirban Bain
About FireCompass:
FireCompass is a SaaS platform for Continuous Automated Pen Testing, Red Teaming and External Attack Surface Management (EASM). FireCompass continuously indexes and monitors the deep, dark and surface webs using nation-state grade reconnaissance techniques. The platform automatically discovers an organization’s digital attack surface and launches multi-stage safe attacks, mimicking a real attacker, to help identify breach and attack paths that are otherwise missed out by conventional tools.
Feel free to get in touch with us to get a better view of your attack surface.










