During the week of December 25 to 29, FireCompass research team identified a huge number of CVEs that are high in severity and ransomware, botnets, and threat actors creating havoc. Some of the CVEs identified are of popular commercial products used by variants of industries and somenew & well known malwares targeting industries for this week. In this, we will list important CVEs discovered as well as list of malware, threat actors and botnets which were most active along with the CVEs that they were using in their campaigns.
List of Critical Vulnerabilities That Were Exploited – FireCompass Research :
- CVE-2023-51098, CVE-2023-51099, CVE-2023-51100, CVE-2023-51094 Tenda Multiple Vulnerability
- CVE-2023-50968 – Apache Software Foundation Apache OFBiz
- CVE-2021-38927 – IBM Aspera Console
List of Malwares And Threat Actors:
- CVE-2023-7102 – Barracuda Networks Inc. Barracuda ESG Appliance
-> Hackers Won't Wait For Your Next Pen Test: Know Automated Continuous Pen Test
Detailed Analysis: Vulnerabilities
CVE-2023-51098, CVE-2023-51099, CVE-2023-51100, CVE-2023-51094 Tenda Multiple Vulnerability
CVE-2023-51098 – Command Injection
CVE-2023-51098 is a critical vulnerability in the Tenda W9 V1.0.0.7(4456)_CN router that allows attackers to inject malicious commands into the device through the form Set Diagnose Info function. This could give them complete control over the router, enabling them to steal data, spy on your network activity, or even launch attacks against other devices on your network. To protect yourself, update your router to the latest firmware as soon as possible and be on the lookout for suspicious activity on your network.
CVE-2023-51099 – Command Injection
CVE-2023-51099 is another critical command injection vulnerability found in the Tenda W9 V1.0.0.7(4456)_CN router. This time, the vulnerability lies within the form exe Command function, allowing attackers to potentially inject malicious commands and seize control of the device.
CVE-2023-51100 – Command Injection
The Tenda W9 V1.0.0.7(4456)_CN router is vulnerable to yet another critical command injection flaw, this one residing in the form Get Diagnose Info function. Similar to the previously mentioned vulnerabilities, this one allows attackers to inject malicious commands, potentially compromising the device and enabling them to steal data, spy on network activity, or launch further attacks.
CVE-2023-51094 – Command Injection
CVE-2023-51094 is a critical vulnerability in the Tenda M3 V1.0.0.12(4856) router that allows attackers to remotely execute arbitrary commands on the device through the TendaTelnet function. This could grant them full control over the router, enabling them to steal sensitive data, disrupt network operations, or launch further attacks.
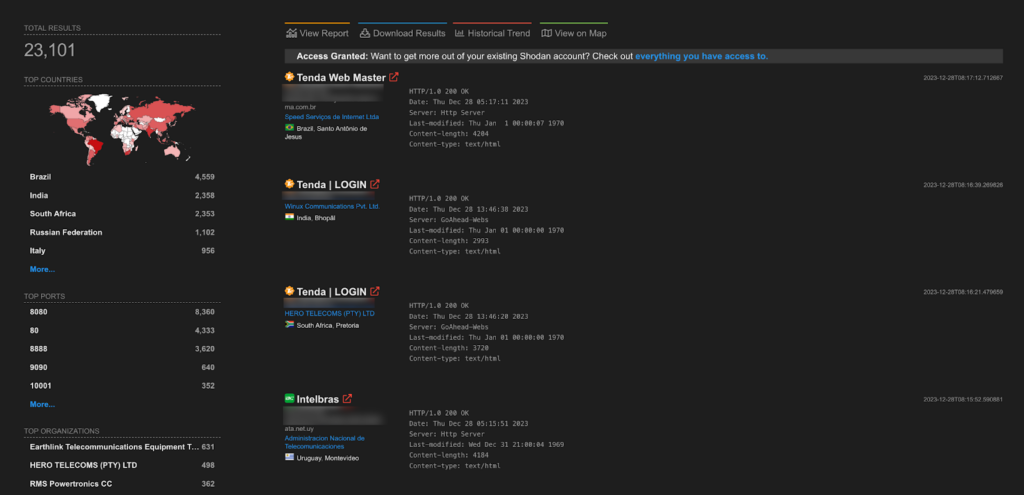
A total of 2,304 endpoints of IBM DB2 are exposed on the Shodan.
CVE-2023-50968 – Apache Software Foundation Apache OFBiz
Arbitrary file properties reading vulnerability in Apache Software Foundation Apache OFBiz when user operates an uri call without authorizations. The same uri can be operated to realize a SSRF attack also without authorizations. Users are recommended to upgrade to version 18.12.11, which fixes this issue.
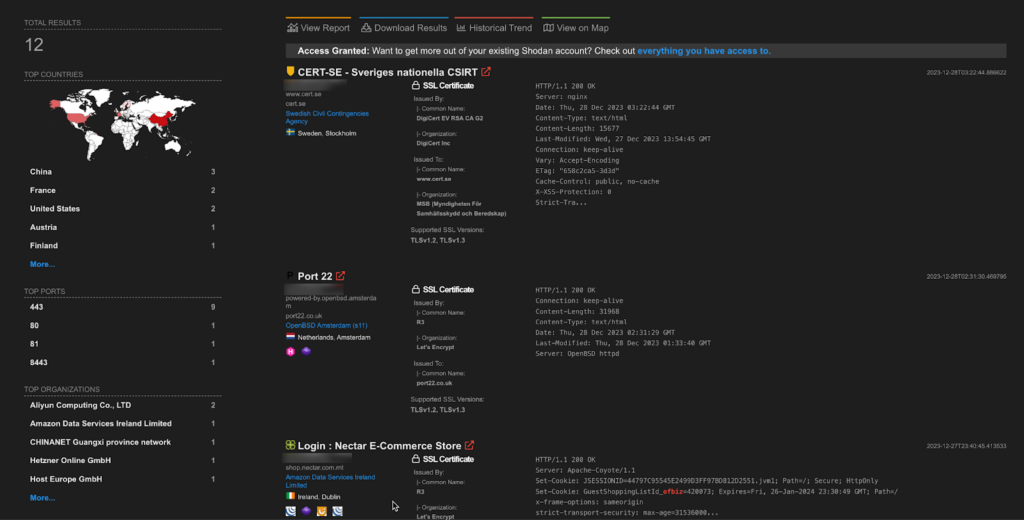
A total of 12 endpoints of Apache Software Foundation Apache OFBiz are exposed on the Shodan.
>> Find Critical Risks in 72 Hours & Continuous Risk Hunting (Request Demo)
CVE-2021-38927 – IBM Aspera Console
CVE-2021-38927 is a high-severity cross-site scripting (XSS) vulnerability found in IBM Aspera Console version 3.4.0. It allows attackers to inject malicious JavaScript code into the Web UI, potentially leading to credential theft, unauthorized actions, or other attacks within a user’s trusted session. IBM has assigned it the X-Force ID 210322.
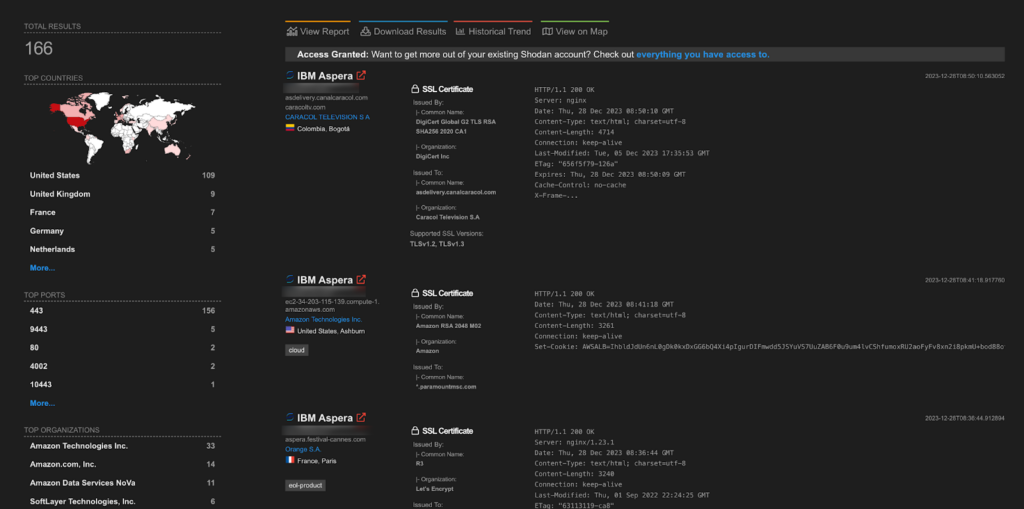
Approximately 8 thousand endpoints for Netgate Pfsense Plus are exposed on shodan.
>> [Request RECON Demo] - Reconnaissance Techniques As Threat Actors
Important Weekly Threat Actors
CVE-2023-7102 – Barracuda Networks Inc. Barracuda ESG Appliance
Barracuda took swift action to address a zero-day vulnerability (CVE-2023-7102) in its Email Security Gateway (ESG) appliances by remotely patching all active devices on December 21. This came in response to exploitation attempts by the Chinese hacking group UNC4841, who had already managed to deploy SeaSpy and Saltwater malware on some compromised appliances. A second wave of security updates was deployed the following day to address these compromised systems. The vulnerability stemmed from a weakness in a third-party library used by the Amavis virus scanner on the ESG appliances.
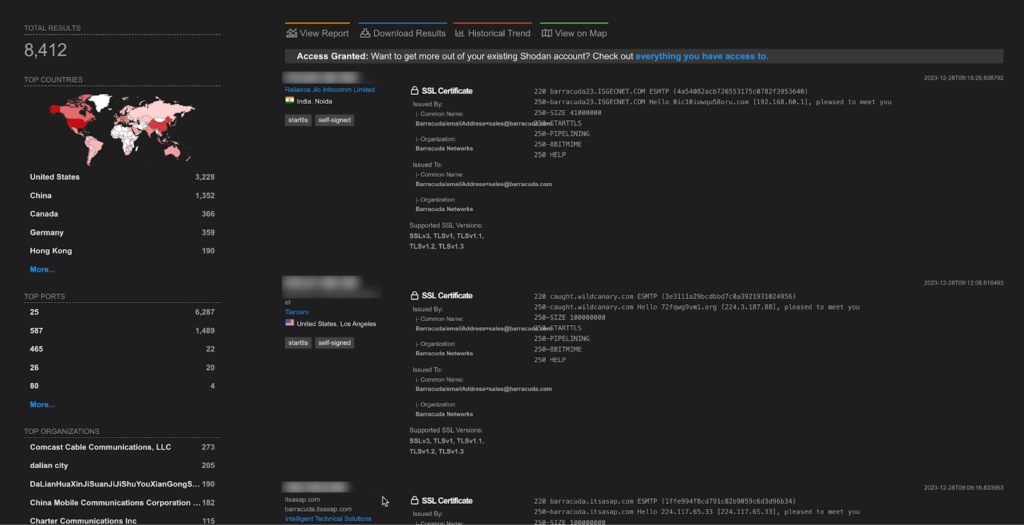
A total of more than 8K endpoints of Barracuda ESG Appliance are exposed on the Shodan.
Author: Debdipta Halder
Assisted By: Soumyanil Biswas, Faran Siddiqui, Anirban Bain
About FireCompass:
FireCompass is a SaaS platform for Continuous Automated Pen Testing, Red Teaming and External Attack Surface Management (EASM). FireCompass continuously indexes and monitors the deep, dark and surface webs using nation-state grade reconnaissance techniques. The platform automatically discovers an organization’s digital attack surface and launches multi-stage safe attacks, mimicking a real attacker, to help identify breach and attack paths that are otherwise missed out by conventional tools.
Feel free to get in touch with us to get a better view of your attack surface.










