During this week from December 11 to 15, the FireCompass research team uncovered a substantial number of Common Vulnerabilities and Exposures (CVEs) marked as high severity. Notably, ransomware, botnets, and various threat actors were causing significant disruptions. Among the identified CVEs were vulnerabilities found in widely-used commercial products across various industries. Additionally, new and familiar malware strains were observed targeting different sectors throughout the week. In this overview, we will highlight the crucial CVEs that were discovered, along with a list of the most active malware, threat actors, and botnets, specifying the CVEs exploited in their campaigns.
List of Critical Vulnerabilities That Were Exploited – FireCompass Research :
- CVE-2023-46157 – CloudPanel OS Command Injection
- CVE-2021-44228 – Apache Log4j Code Execution
- CVE-2021-44832 – Apache Log4j Code Execution
- CVE-2022-23307 – Apache Log4j Code Execution
- CVE-2022-23305 – Apache Log4j Code Execution
- CVE-2022-23302 – Apache Log4j Code Execution
- CVE-2023-49804 – Uptime Kuma Unauthorized Access
- CVE-2023-42325 – NetgatePFsense Privilege Escalation
- CVE-2023-42327 – NetgatePFsense Cross-Site Scripting
- CVE-2023-42326 – NetgatePFsense Code Execution
- CVE-2023-6790 – Palo Alto PANOS Code Execution
List Of Malwares And Threat Actors:
- CVE-2021-44228 – Apache Log4j2
- CVE-2023-42793 – APT29 hacking group
- CVE-2023-50164 – Hackers
-> Hackers Won't Wait For Your Next Pen Test: Know Automated Continuous Pen Test
Detailed Analysis: Vulnerabilities
CVE-2023-46157 – CloudPanel OS Command Injection
CVE-2023-46157 is a vulnerability in MGT CloudPanel 2.0.0 through 2.3.2 that allows any user to execute arbitrary commands on the underlying operating system. This is due to a flaw in the File-Manager component that allows users to change file ownership and permissions in a way that grants them unauthorized access.
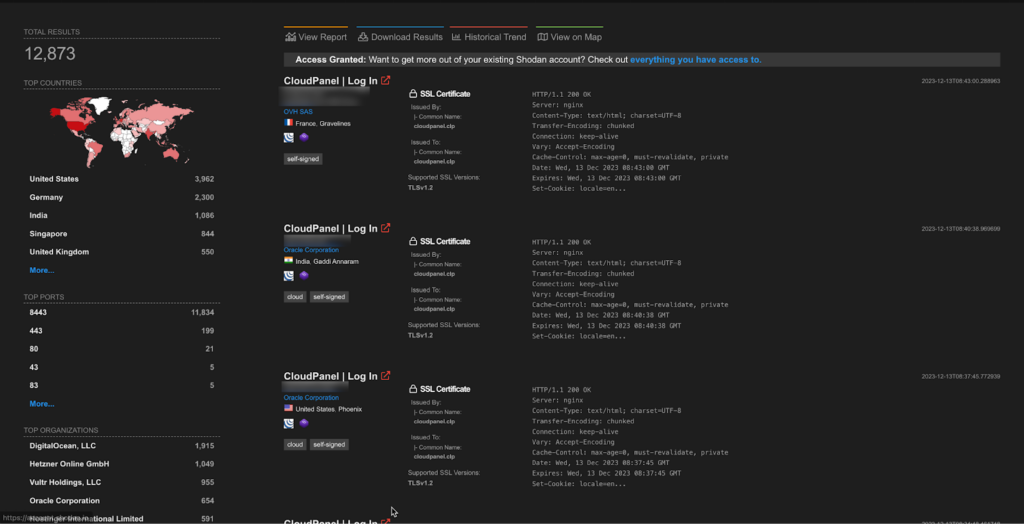
A total of more than 12K endpoints of CloudPanel are exposed on the Shodan.
CVE-2021-44228, CVE-2021-44832, CVE-2022-23307, CVE-2022-23305 and CVE-2022-23302 – Apache Log4j Multiple Vulnerability
CVE-2021-44228
Apache Log4j2 2.0-beta9 through 2.15.0 (excluding security releases 2.12.2, 2.12.3, and 2.3.1) JNDI features used in configuration, log messages, and parameters do not protect against attacker controlled LDAP and other JNDI related endpoints. An attacker who can control log messages or log message parameters can execute arbitrary code loaded from LDAP servers when message lookup substitution is enabled. From log4j 2.15.0, this behavior has been disabled by default. From version 2.16.0 (along with 2.12.2, 2.12.3, and 2.3.1), this functionality has been completely removed. Note that this vulnerability is specific to log4j-core and does not affect log4net, log4cxx, or other Apache Logging Services projects.
CVE-2021-44832
Apache Log4j2 versions 2.0-beta7 through 2.17.0 (excluding security fix releases 2.3.2 and 2.12.4) are vulnerable to a remote code execution (RCE) attack when a configuration uses a JDBC Appender with a JNDI LDAP data source URI when an attacker has control of the target LDAP server. This issue is fixed by limiting JNDI data source names to the java protocol in Log4j2 versions 2.17.1, 2.12.4, and 2.3.2.
CVE-2022-23307
CVE-2020-9493 identified a deserialization issue that was present in Apache Chainsaw. Prior to Chainsaw V2.0 Chainsaw was a component of Apache Log4j 1.2.x where the same issue exists.
CVE-2022-23305
By design, the JDBCAppender in Log4j 1.2.x accepts an SQL statement as a configuration parameter where the values to be inserted are converters from PatternLayout. The message converter, %m, is likely to always be included. This allows attackers to manipulate the SQL by entering crafted strings into input fields or headers of an application that are logged allowing unintended SQL queries to be executed. Note this issue only affects Log4j 1.x when specifically configured to use the JDBCAppender, which is not the default. Beginning in version 2.0-beta8, the JDBCAppender was re-introduced with proper support for parameterized SQL queries and further customization over the columns written to in logs. Apache Log4j 1.2 reached end of life in August 2015. Users should upgrade to Log4j 2 as it addresses numerous other issues from the previous versions.
CVE-2022-23302
JMSSink in all versions of Log4j 1.x is vulnerable to deserialization of untrusted data when the attacker has write access to the Log4j configuration or if the configuration references an LDAP service the attacker has access to. The attacker can provide a TopicConnectionFactoryBindingName configuration causing JMSSink to perform JNDI requests that result in remote code execution in a similar fashion to CVE-2021-4104. Note this issue only affects Log4j 1.x when specifically configured to use JMSSink, which is not the default. Apache Log4j 1.2 reached end of life in August 2015. Users should upgrade to Log4j 2 as it addresses numerous other issues from the previous versions.
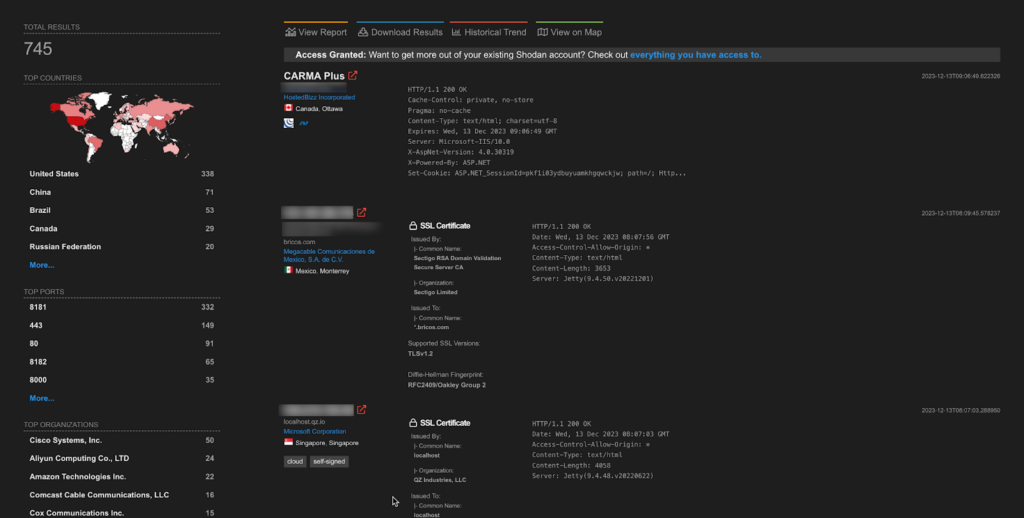
A total of around 700 endpoints of Apache Log4j are exposed on the Shodan.
>> Find Critical Risks in 72 Hours & Continuous Risk Hunting (Request Demo)
CVE-2023-49804 – Uptime Kuma Unauthorized Access
Uptime Kuma is an easy-to-use self-hosted monitoring tool. Prior to version 1.23.9, when a user changes their login password in Uptime Kuma, a previously logged-in user retains access without being logged out. This behavior persists consistently, even after system restarts or browser restarts. This vulnerability allows unauthorized access to user accounts, compromising the security of sensitive information. The same vulnerability was partially fixed in CVE-2023-44400, but logging existing users out of their accounts was forgotten. To mitigate the risks associated with this vulnerability, the maintainers made the server emit a `refresh` event (clients handle this by reloading) and then disconnecting all clients except the one initiating the password change. It is recommended to update Uptime Kuma to version 1.23.9.
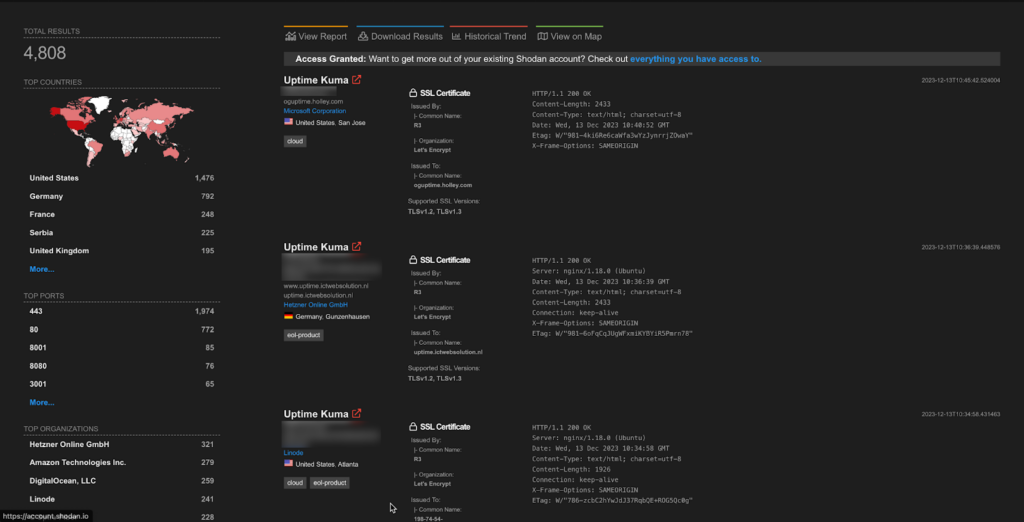
Approximately 8 thousand endpoints for Netgate Pfsense Plus are exposed on shodan.
>> [Request RECON Demo] - Reconnaissance Techniques As Threat Actors
CVE-2023-42325, CVE-2023-42327 and CVE-2023-42326 – NetgatePFsense Multiple Vulnerability
CVE-2023-42325
Cross Site Scripting (XSS) vulnerability in Netgate pfSense v.2.7.0 allows a remote attacker to gain privileges via a crafted url to the status_logs_filter_dynamic.php page.
CVE-2023-42327
Cross Site Scripting (XSS) vulnerability in Netgate pfSense v.2.7.0 allows a remote attacker to gain privileges via a crafted URL to the getserviceproviders.php page.
CVE-2023-42326
An issue in Netgate pfSense v.2.7.0 allows a remote attacker to execute arbitrary code via a crafted request to the interfaces_gif_edit.php and interfaces_gre_edit.php components.
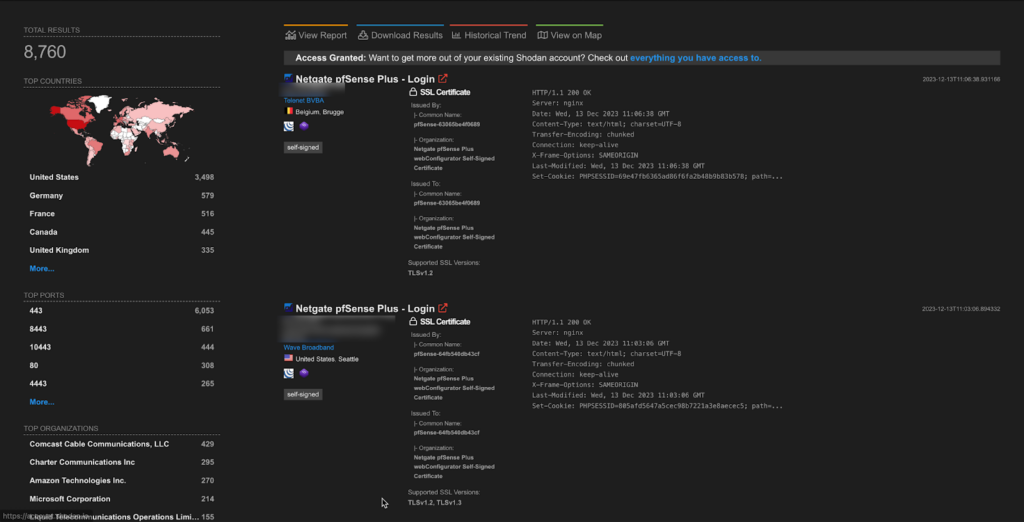
A total of more than 8k endpoints of NetgatePFsense are exposed on the Shodan.
CVE-2023-6790 – Palo Alto PANOS Code Execution
A DOM-Based cross-site scripting (XSS) vulnerability in Palo Alto Networks PAN-OS software enables a remote attacker to execute a JavaScript payload in the context of an administrator’s browser when they view a specifically crafted link to the PAN-OS web interface.
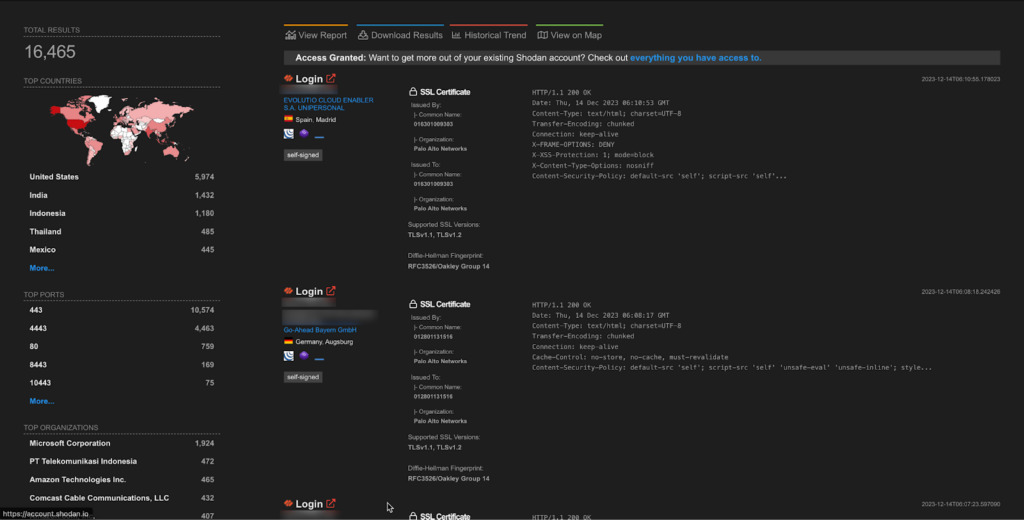
A total of more than 16k endpoints of PAN-OS are exposed on the Shodan.
Important Weekly Threat Actors
CVE-2021-44228 – NineRAT and DLRAT and a malware downloader named BottomLoader
The notorious North Korean hacking group known as Lazarus continues to exploit CVE-2021-44228, aka “Log4Shell,” this time to deploy three previously unseen malware families written in DLang.
The new malware are two remote access trojans (RATs) named NineRAT and DLRAT and a malware downloader named BottomLoader.
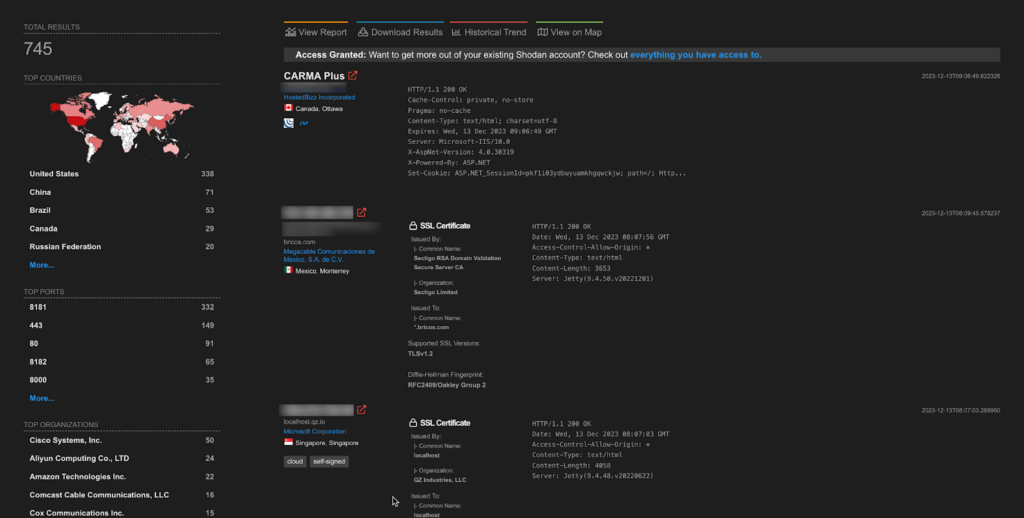
A total of around 700 endpoints of Apache Log4j are exposed on the Shodan.
CVE-2023-42793 – APT29 Hacking group
APT29 is known for breaching several U.S. federal agencies following the SolarWinds supply-chain attack they orchestrated three years ago.
The TeamCity security flaw they’re exploiting in these attacks is identified as CVE-2023-42793 and rated with a critical severity score of 9.8/10, which unauthenticated threat actors can exploit in low-complexity remote code execution (RCE) attacks that don’t require user interaction.
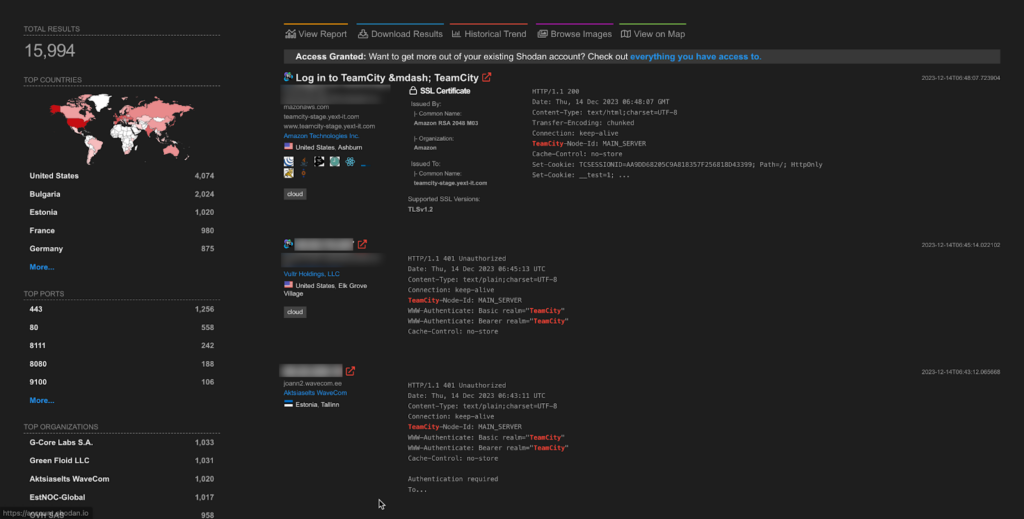
A total of more than 15k endpoints of Team City are exposed on the Shodan.
CVE-2023-50164 – Hackers
Hackers are attempting to leverage a recently fixed critical vulnerability (CVE-2023-50164) in Apache Struts that leads to remote code execution, in attacks that rely on publicly available proof-of-concept exploit code.
It appears that threat actors have just started, according to the Shadowserver scanning platform, whose researchers observed a small number of IP addresses engaged in exploitation attempts.
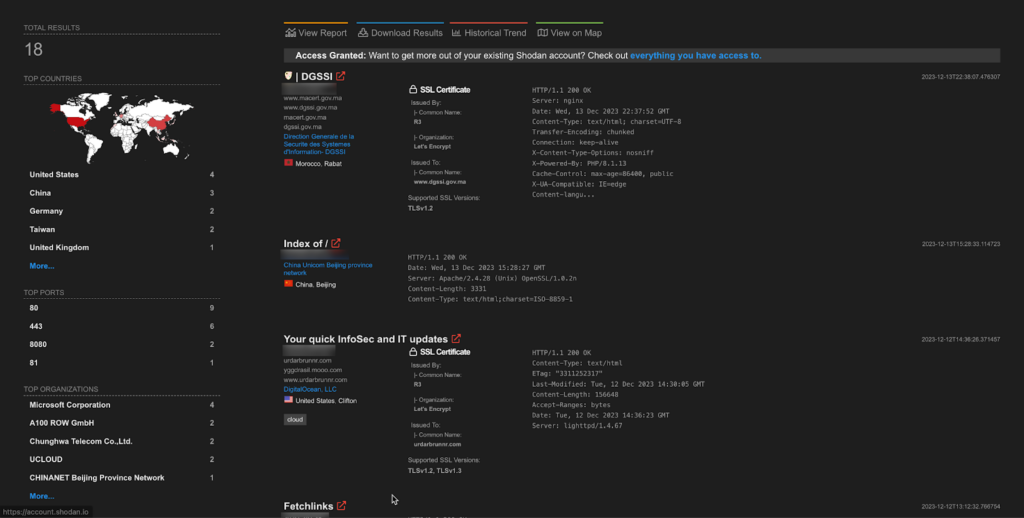
A total of 18 endpoints of Apache Struts are exposed on the Shodan.
Author: Debdipta Halder
Assisted By: Soumyanil Biswas, Faran Siddiqui, Anirban Bain
About FireCompass:
FireCompass is a SaaS platform for Continuous Automated Pen Testing, Red Teaming and External Attack Surface Management (EASM). FireCompass continuously indexes and monitors the deep, dark and surface webs using nation-state grade reconnaissance techniques. The platform automatically discovers an organization’s digital attack surface and launches multi-stage safe attacks, mimicking a real attacker, to help identify breach and attack paths that are otherwise missed out by conventional tools.
Feel free to get in touch with us to get a better view of your attack surface.










