Critical CVEs And Active Threats: Apache Solr, Traccar, Kodbox and More
This week from January 15 to January 19, FireCompass research team identified a huge number of CVEs that are high in severity and ransomware, botnets, and threat actors creating havoc. Some of the CVEs identified are of popular commercial products used by variants of industries and somenew & well known malwares targeting industries for this week. In this, we will list important CVEs discovered as well as list of malware, threat actors and botnets which were most active along with the CVEs that they were using in their campaigns.
List of Critical Vulnerabilities That Were Exploited – FireCompass Research :
- CVE-2023-50290 – Apache Solr
- CVE-2023-46749 – Apache Shiro
- CVE-2023-50729 – Traccar
- CVE-2023-52069 – kodbox
List of Malwares And Threat Actors:
- CVE-2023-46805, CVE-2024-21887 – Ivanti Multiple Vulnerability
-> Hackers Won't Wait For Your Next Pen Test: Know Automated Continuous Pen Test
Detailed Analysis: Vulnerabilities
CVE-2023-50290 – Apache Solr
CVE-2023-50290 is a vulnerability in Apache Solr that can expose sensitive information, such as unprotected environment variables, to unauthorized actors through the Solr Metrics API. This API, which is designed to provide system metrics, inadvertently publishes all environment variables associated with an instance unless specifically configured to hide them. The vulnerability affects Apache Solr versions 9.0.0 to 9.2.9, and users are strongly advised to upgrade to version 9.3.0 or later, where the issue has been addressed by removing environment variables from the Metrics API output.
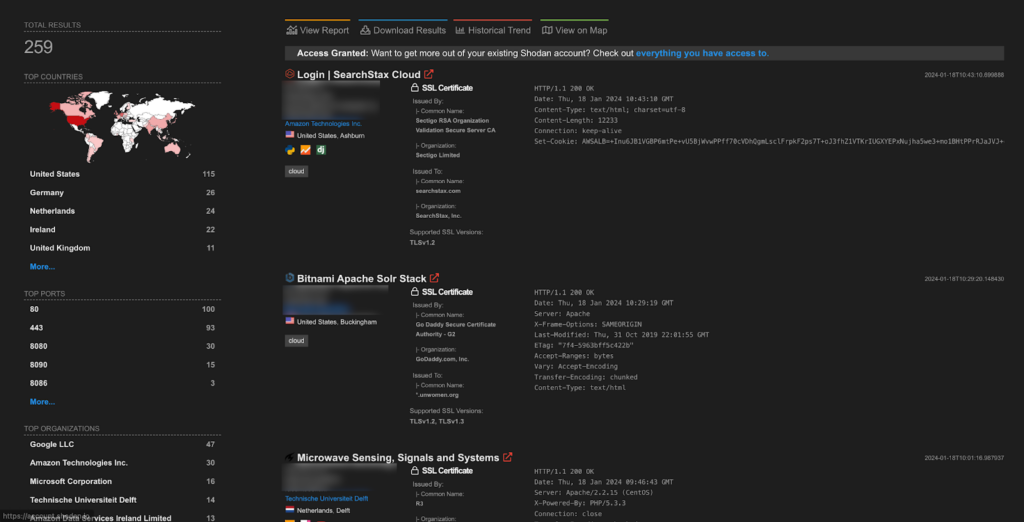
A total of 259 endpoints of Apache Solr are exposed on the Shodan.
CVE-2023-46749 – Apache Shiro
Outdated Apache Shiro versions (before 1.13.0 or 2.0.0-alpha-4) are vulnerable to a path traversal attack via specially crafted URLs, possibly letting attackers bypass authentication and access unauthorized resources. Upgrade immediately or enable blockSemicolon in Shiro to mitigate.
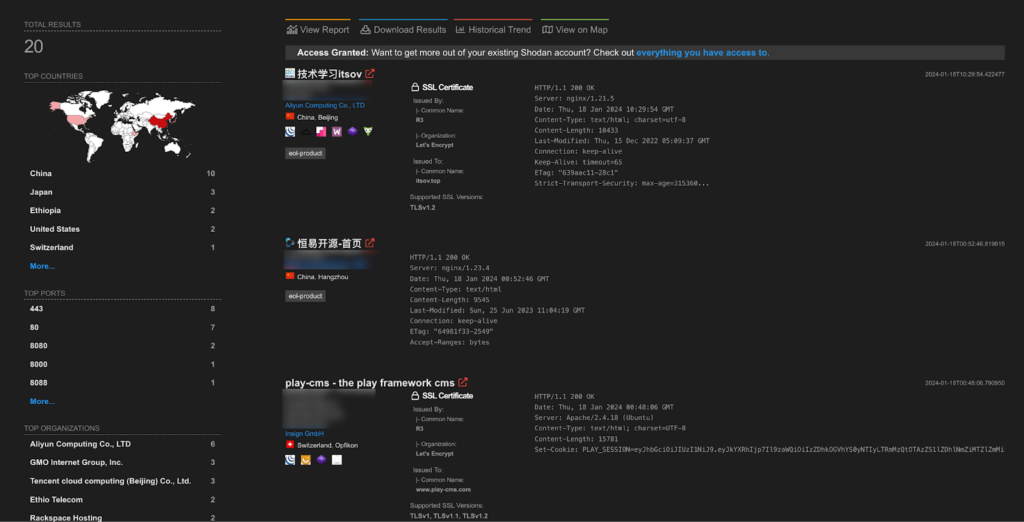
A total of 20 endpoints of Apache Shiro are exposed on the Shodan.
>> Find Critical Risks in 72 Hours & Continuous Risk Hunting (Request Demo)
CVE-2023-50729 – Traccar
Danger lurks in Traccar’s file uploads! A sneaky vulnerability called CVE-2023-50729 lets attackers upload malicious files that can take full control of your server, like a mischievous raccoon slipping through a pet door and wreaking havoc on your kitchen. This “unrestricted file upload” flaw is especially worrisome because Traccar often runs with the highest privileges, like a raccoon with a master key. Imagine a devious hacker uploading a file disguised as a cute kitten picture, but it secretly installs malware or steals your data! Yikes!
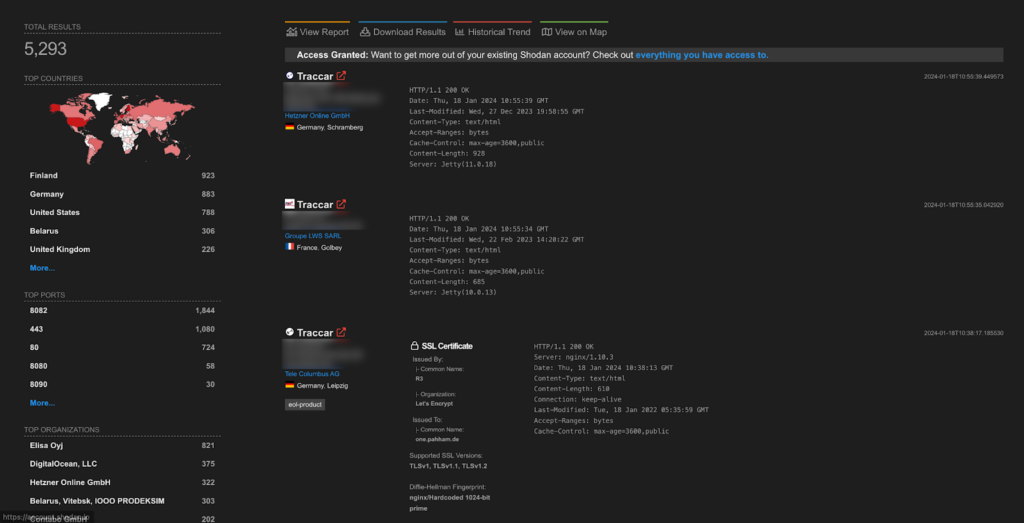
A total of more than 5K endpoints of Traccar are exposed on the Shodan.
CVE-2023-52069 – Kodbox
CVE-2023-52069 is a cross-site scripting (XSS) vulnerability lurking within kodbox, a popular open-source media center platform. This sneaky flaw allows attackers to inject malicious scripts into URLs, potentially tricking users into running harmful code when they click on them. Imagine a movie night gone wrong, where instead of enjoying a heartwarming film, you’re unknowingly installing malware on your device!
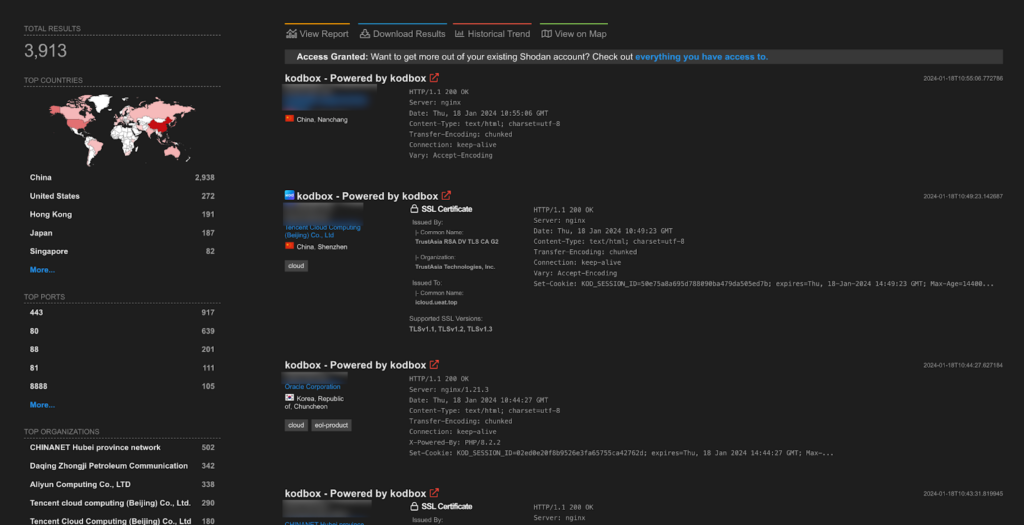
A total of more than 3.5K endpoints of kodbox are exposed on the Shodan.
>> [Request RECON Demo] - Reconnaissance Techniques As Threat Actors
Important Weekly Threat Actors
CVE-2023-46805 – Ivanti Multiple Vulnerability
CVE-2023-46805 – Ivanti ICS and Ivanti PS
CVE-2023-46805 is a sneaky vulnerability lurking in Ivanti Connect Secure and Policy Secure gateways that lets attackers bypass security checks and access restricted resources remotely, like a master thief cracking a safe without setting off any alarms. This high-severity flaw, rated 8.2 on the CVSS scale, essentially grants attackers an all-access pass to sensitive data and systems within your network. Imagine the chaos a thief could unleash with unrestricted access to your most valuable assets! Patching immediately is crucial to keep your Ivanti gateways secure and your data safe from prying eyes.
CVE-2024-21887 – Ivanti Connect Secure
CVE-2024-21887 is a critical, command injection vulnerability in Ivanti Connect Secure and Policy Secure gateways. Imagine handing your system administrator a malicious script disguised as a harmless update. That’s essentially what this flaw allows: authenticated attackers can inject and execute any commands they want on the device, potentially taking complete control. It’s like giving away the master key to your digital kingdom!
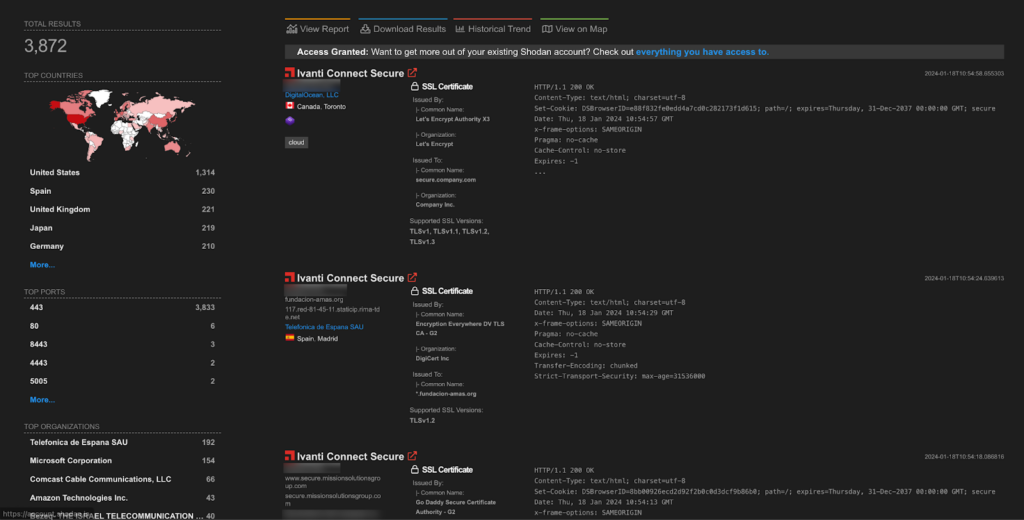
A total of more than 3.5K endpoints of Ivanti ICS & Policy Secure are exposed on the Shodan.
Author: Debdipta Halder
Assisted By: Soumyanil Biswas, Faran Siddiqui, Anirban Bain
About FireCompass:
FireCompass is a SaaS platform for Continuous Automated Pen Testing, Red Teaming and External Attack Surface Management (EASM). FireCompass continuously indexes and monitors the deep, dark and surface webs using nation-state grade reconnaissance techniques. The platform automatically discovers an organization’s digital attack surface and launches multi-stage safe attacks, mimicking a real attacker, to help identify breach and attack paths that are otherwise missed out by conventional tools.
Feel free to get in touch with us to get a better view of your attack surface.










