Gartner® Report
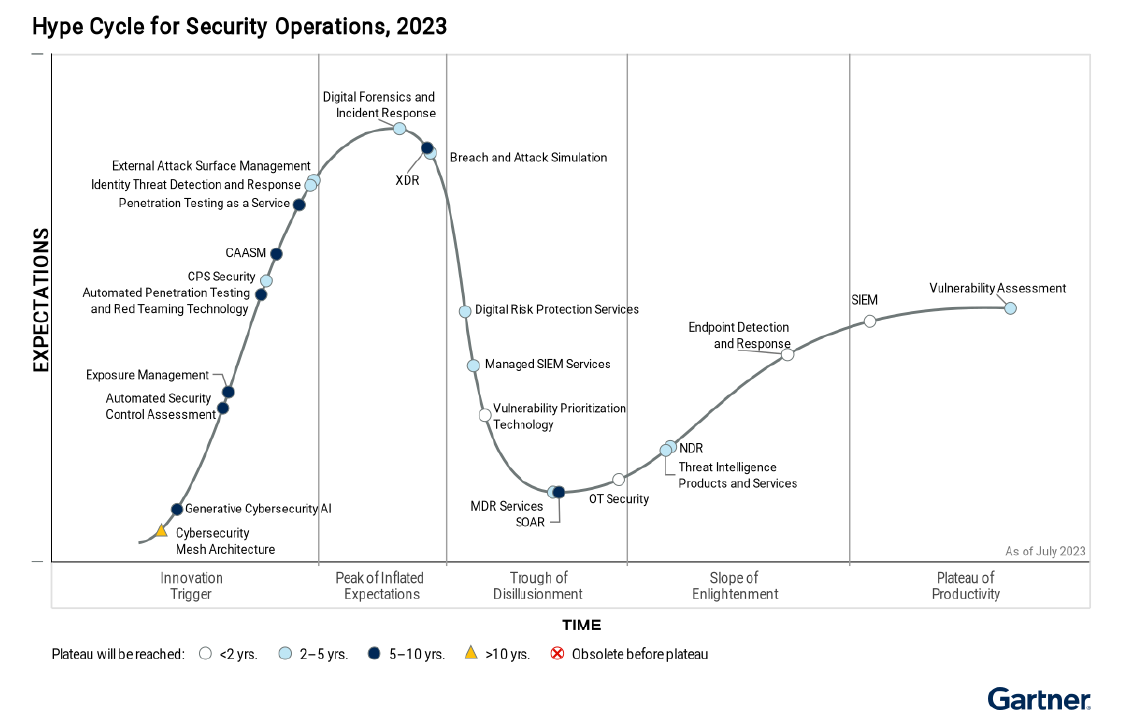
Hype Cycle For Security Operations, 2023
Security and risk management leaders can use this research to strategize and deliver SecOps capability and functions.
Security and risk management leaders can use this research to strategize and deliver SecOps capability and functions.
This year’s Hype Cycle shows that technologies facing more risks are getting a lot of attention. The technologies that have shown significant advancements are MDR, exposure management, external attack surface management (EASM), cyber asset attack surface management, identity threat detection and response and XDR. These technologies highlight the growing need to gather more information, make better decisions, and respond quickly to the increasing threats and risks faced by organizations.
You have successfully joined our subscriber list.
Disclaimer:
Gartner Hype Cycle for Security Operations, 2023 by Jonathan Nunez, Andrew Davies published on 20 July 2023
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
The graphic was published by Gartner, Ins. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from FireCompass.
GARTNER and Hype Cycle are registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and are used herein with permission. All rights reserved.Hype Cycle for Security Operations, 2023

Identify all IPs, Applications, exposed database/cloud buckets, code leaks, leaked credentials, vulnerabilities, exposed test/pre-production systems, etc.
Launches multi-stage attacks on your attack surface and identifies the breach and attack paths.
Discover ransomware attack surface and it’s risk by scanning entire internet for risky assets potentially belonging to the organization

We’ve put together some top talks from global security conferences that could help you get a hang on the debatable topic

We have listed a few breach response tactics that organizations need to keep handy for rainy days. Read to know more about how you can keep your organization safe.

Here we list 10 tools which can be used for Reconnaissance by Security teams in order to assess their own security posture against hackers.
©2024 FireCompass, All Rights Reserved.