Take any of your favorite movies, and you cannot have a script without a villain. And your favorite heroes evolve only because villains exist. The only difference is that the truth is stranger than fiction. In real life, the villains are too many, and heroes are few. But we do have superheroes who take on all the bad guys at once.
As per Forbes data, 83% of enterprise workloads will move to the cloud by 2020, making it easy for hackers to target more and more businesses. Presently, according to a study conducted by the University of Maryland, hackers attack every 39 seconds, on average 2,244 times a day. While Accenture data reinforces that attacks have increased by 67% since 2018.
Amidst this alarming data, the reassurance comes from the fact that technology, as we know it today, is evolving too. In contrast, the threat actors are trying to break your organization’s shield and steal your data. Your only chance at a great defense is to use the right technology that will keep your guard up. As the saying goes, “a good defense is a great offense.”
In this blog, we will discuss two such techniques – Red Teaming and Penetration Testing and understanding how they are different. And how each one of them helps you against the bad actors.
Red Teaming is a multilayered attack simulation that can measure how well an organization’s people and network systems can withstand an attack from a real-life adversary.
In a rather layman’s term, one may call it “ethical hacking.” It helps independent security teams configure real-life attacks to check where the organizational barrier might break, which will help the organization fix it.
The concept of red teaming arose from the military and intelligence community. Red teaming’s core idea is to get an adversary’s perspective into an organization’s defense mechanism. Red Teaming needs to be done continuously because it’s a long term challenge, and at a point in time, red teaming might not give the same result in today’s world.
Red teams get a mandate, and the exercise is built around the same mandate, not on the scope. The red team itself defines the scope, the mandate will change the scope as well.
What Is Penetration Testing?
Penetration testing is a type of audit done to assess a part of a network or an application. In this, typically, your team can scan your network by manual or automated vulnerability discovery. It’s based on scoping only, carried out in the development environment, and not in the production environment. The results because of which can differ.
Typically people who are looking for pentesting are trying to achieve the following objectives:
- Validating the potential impact of a breach: Pentesting can validate data in the environment that can be manipulated by an attacker. It also helps in risk assessment, assessing security architecture, and operation decisions.
- Verifying detection and response: It can assess the organization in terms of incident control and detection. It also confirms the detection mechanism in place.
- Accessing current vulnerabilities and learning how attackers can manipulate them in the future
- Addressing Compliance requirement put forth by the organization
Pentest is usually requested by organizations to identify all vulnerabilities, with an intent to fix the problems. This approach is incorrect since pentesters are not looking for all visible vulnerabilities. They only look for issues that only go with their objectives.
How Red Teaming Differs From Pen Testing?
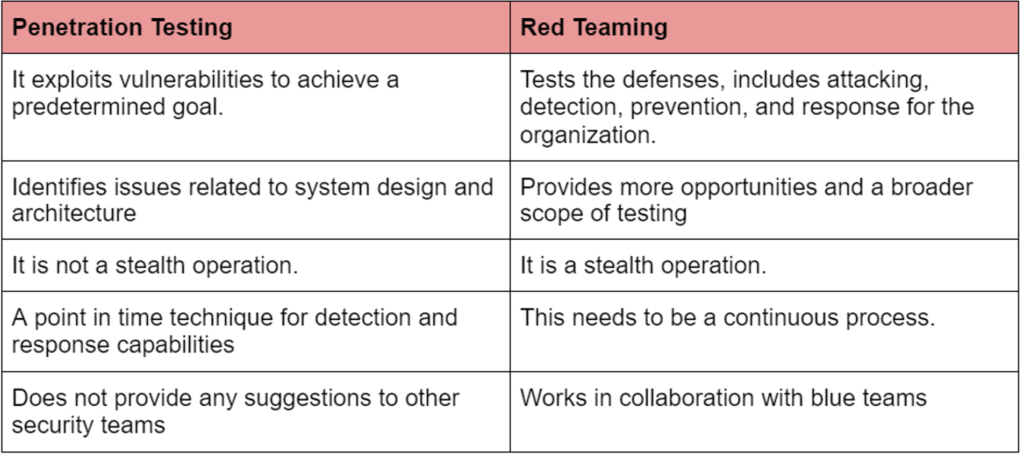
While pen-testing is more scenario-based, red teaming is goal-based. Goals can be set like gaining access to sensitive servers or business-critical information.
Pentest are conducted with knowledge. It is not stealth or evasive or does not have the blue team’s ability to detect and respond mostly because the blue team is aware of the conducted scope and test.
Penetration testing is conducted on less than 5% of the attack surface. It only covers the crown jewels and often excludes other systems that can serve as a pathway to break into. Pre-production systems, for example, are rarely tested but frequently contain production data or keys.
Whereas red teaming focuses on advanced threat actors using stealth and conducting real-life attacks. This is done to find gaps in the defensive strategy. The real value of this can be derived by understanding how an organization responds to real-world attacks.
Since red teaming is a stealth exercise, it is conducted without the blue team’s knowledge. If the blue team finds a malicious activity, it responds to it as a real-world attack.
At the end of the engagement, the blue team will give the red team the compromise indicators. This data can be made into a report. And it’s used to close the security gaps.
Some of the key differences between red teams and pentesting are added below:
The Red Team Operation Model
- Continuous Process – Red teams find opportunities for newer attack methods. Finds weaknesses in the blue team’s practices and processes and uses techniques that take more time than penetration technique. Continuous exercises help the organization to do more granular and targeted testing when new attack methods are discovered, without waiting for a scheduled pentest.
- Based On Collaboration – One thing to understand here is that Red Teams are not here to work against the blue teams or expose the lack of blue teams defenses. Red teams are here to find the gaps and then fill them along with the blue teams. Red teams’ real value comes only when they present the first report and then collaborate with blue teams to better the security infrastructure. It should be a situation where red teams can say, “ here’s how we managed to breach your defenses, and this is how we set it up now so that it becomes unbreachable.”
- Threat Based Scenarios – A red team attack is based on real threat-based scenarios. The red approach teams use “assume breach analysis,” under this, the red teams assume that an attack has happened and then formulate the response. Threat intelligence and threat assessment reports are often made to feed the red teams with potential attack strategies.
- Broad Scope And Less Restriction Than Pentest – Red Teams work on a mandate. Once the mandate is clear, the scope of the operation can be defined. Which already means that the scope can be vast. There is also a risk and unpredictability involved in the red team exercise, which keeps the blue teams on their toes.
Use of Red Teaming in Strategic Planning
Red teaming can be tailored according to the specific needs of an organization. But it won’t do scenario analysis; as mentioned before, the red team acts as opponents designed to sense an organization’s ability to respond to adversaries.
It can help enterprise risk management to overcome cognitive biases. According to Gartner, 92% of strategic initiatives experience challenges during execution.
Applying the red team mindset in risk assessment and decision making can combat common pitfalls and test assumptions using red teaming techniques.
Leveraging Red Teaming For Defense
As the saying goes, “ prevention can take a long time, detection is better and helps you fix things fast.” Red teaming focuses on visibility. If an attacker customizes, they can primarily go undetected. Red teaming focuses on understanding the capabilities of the attacker and applying threat models and simulations. It hunts for treats by performing attacks.
Delivering High Value With Low Cost
Red Teaming helps enterprise risk managers weigh multiple known and unknown factors and present outcomes. It builds a framework to analyze the cost, risks, and opportunities and presents to decision-makers with different results.
If implemented correctly, it can support the development indicators monitor for signs that a particular future is becoming more or less likely, action plans can be reassessed.
Is A Point-in-Time Red Teaming Assessment Enough?
While many organizations have focussed on doing a point-in-time red teaming, the truth of the matter is that adversaries are trying to breach your organization every day. While bad actors need to win once, you need to win everyday. This brings us to the need for Continuous Automated Red Teaming.
Why Is Continuous Automated Red Teaming(CART) The Future Of Security Testing?
The traditional red teaming is hard to scale, considering it takes a lot of manual effort and exercises stretches for an extended period. This new technology can do the same thing without any manual intervention every day seamlessly, let alone the fact that it is scalable.
The Firecompass CART Platform can search and index deep, dark, and surface web using similar recon techniques of that of a hacker. It then automatically discovers your organization’s digital attack surface, exposed databases, cloud buckets, open ports, exposed credentials, etc. The attack engine then launches safe multi-stage attacks to discover attack paths & security blind spots before hackers do. The platform also provides a dashboard to prioritize risks and suggestions to mitigate.




