What is API Discovery?
API discovery plays an important role while mapping the attack surface for a company during a security assessment or any kind of engagement. The discovery allows an organization to map its all API’s and can check which person has what permissions on the API.
The Importance Of API Discovery
API discovery is important because it helps developers to quickly find their APIs, especially those best suited for use in their apps or websites. It also helps them to mitigate risks by uncovering hidden vulnerabilities, like shadow APIs that are utilizing sensitive data like credit card info, social security numbers, and other personally identifiable information (PII). The importance of API discovery is rapidly increasing as more companies are using APIs to build their products and services.
Discovering API’s
Postman Public API Network
Just like github repositories postman has it own public API network, Every company who choose to make it’s API workflow public will be available to any user on postman which lead to company’s new api discovery, API keys, PII data being disclosed in post requests and the structure of the API.
Install postman from https://www.postman.com/downloads/ or you can simply use the browser based web version.
Reference tool for integration : https://github.com/cosad3s/postleaks
The home page of postman will look like the below screenshot.
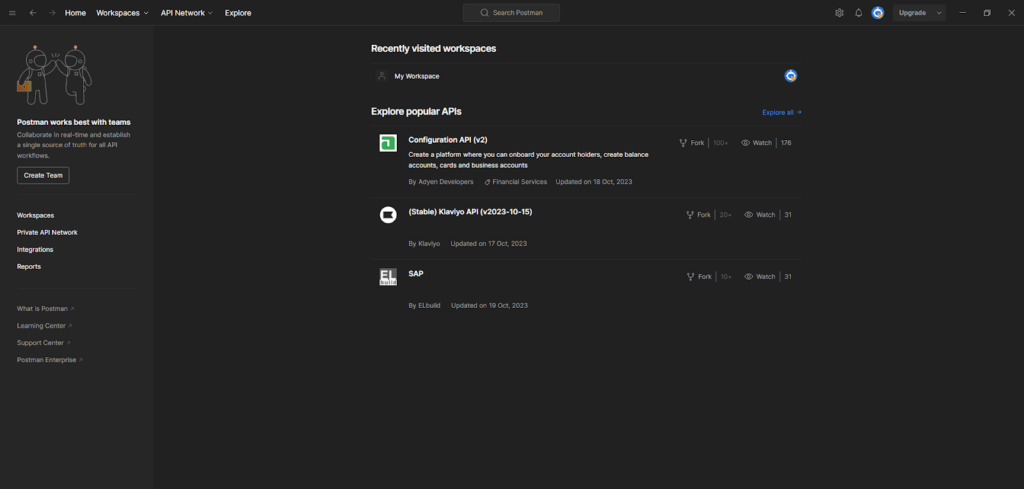
To search for a company’s api search for the domain name for example facebook.com
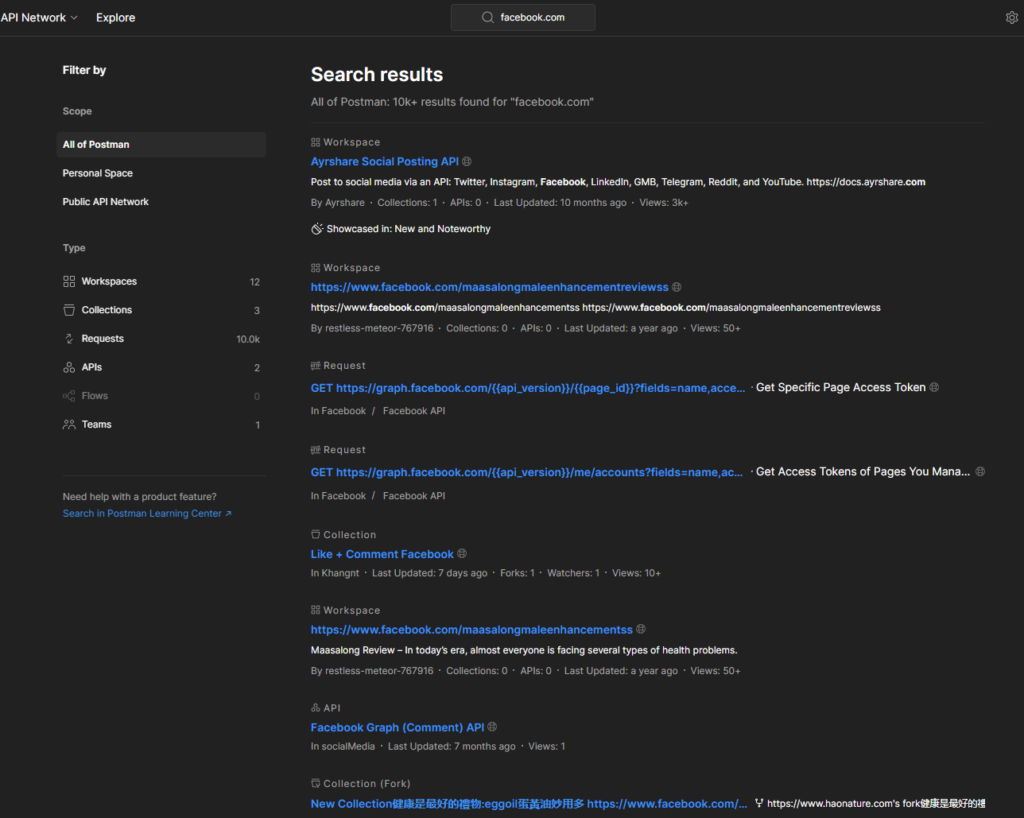
As a result we can see multiple numbers of results that contain workspace + Collections + Requests + APIs, Flows and Teams.
Further if looking closely at a request, the API’s get/post requests containing the body, parameters, authorizations and more information can be seen.
The body can contain sensitive information like API keys and PII data.
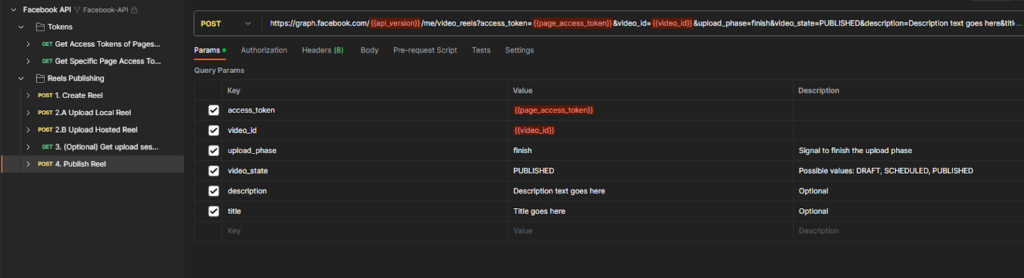
That’s how it is possible with the help of postman to discover and enumerate the API’s passively.
Usage Example
Postleaks -k $DOMAIN -o output.json
-> Hackers Won't Wait For Your Next Pen Test: Know Automated Continuous Pen Test
Discovering APIs With Google Dorking
Google dorking plays a big role in discovering new assets for an organization and it can be used to discover new APIs related to an organization. There are couple of API keywords that can be specified in the dorks for the discovery, Some of the top keywords are as follows
| # | Key word | Google Dork |
| 1 | api* | site:”*.company.com” “api*” |
| 2 | api* | inurl:”api*.company.com” |
| 3 | v1 | site:”*.company.com” inurl:”/v1/API” |
| 4 | api | site:”*.company.com” intitle:”api” |
| 5 | apidocs | site:”*.company.com” intext:”apidocs” |
More permutation and combination can be done to get more keywords for dorking.
A example dorking on the facebook.com domain site:*.facebook.com api
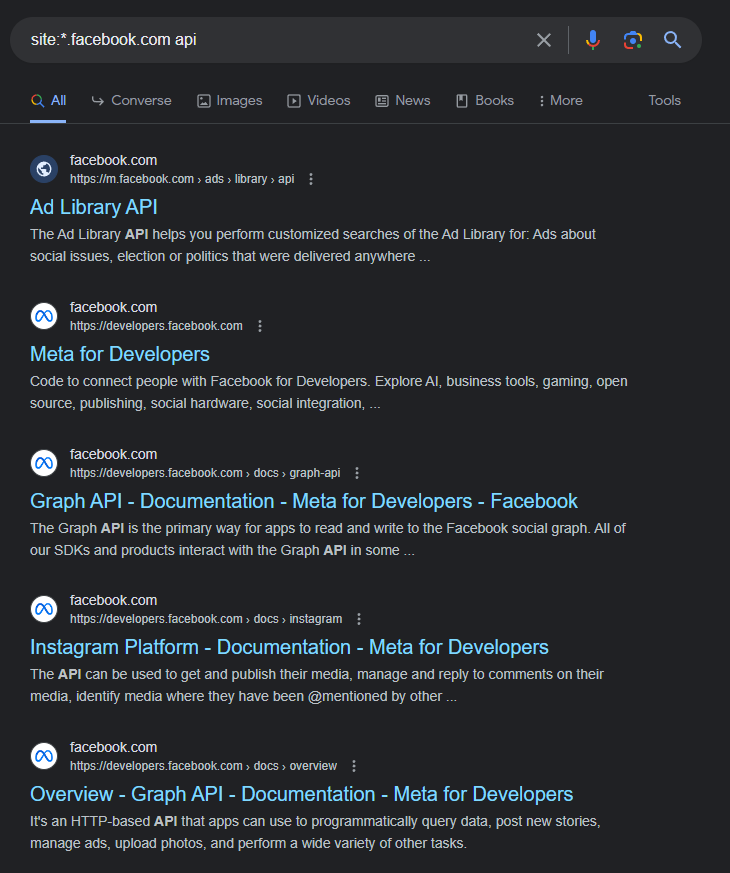
Searching for the api keyword in the url site:*.facebook.com inurl:api, A good wordlist for the google dorks can be found out at
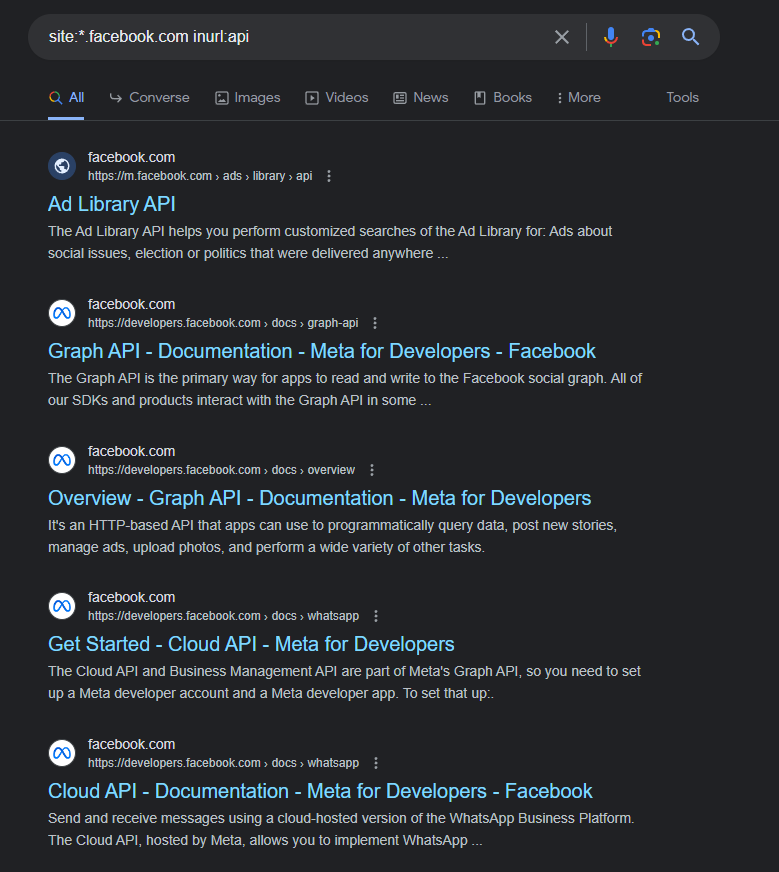
Multiple Dorks with multiple keywords can be used to discover new APIs and API endpoints.
There are some popular APIs that can be discovered by just their name for example we have to find out swagger API’s locations for a company the dork for that will be as follows
| # S.NO. | DORK |
| 1 | site”*.company.com” intitle:swagger |
Same like swagger multiple popular APIs can be found with google dorking.
API Subdomains Discovery With Alterx
After discovering subdomains from various sources, it is possible to use alterx to generate a list of permutation lists of subdomains that can be further filtered with the live and active subdomains.
Save the below list of keywords as api-keywords.txt
| # S.NO. | Keyword |
| 1 | api |
| 2 | api-prod |
| 3 | api-uat |
| 4 | api-dev |
| 5 | v1.api |
| 6 | v1-api |
| 7 | v1.api-prod |
| 8 | v1.api-uat |
| 9 | v1.api-dev |
| 10 | v2.api |
| 11 | v2-api |
| 12 | v2.api-prod |
| 13 | v2.api-uat |
| 14 | v2.api-dev |
| 15 | api-metrics |
| 16 | api-development |
| 17 | api1 |
| 18 | api2 |
| 19 | api-public |
| 20 | public-api |
Pass the list through the alterx to check how many permutations it makes
-> (Request Demo) 10 X Pen Testing Frequency & 100% Asset Coverage
cat fb-subs.txt| alterx -p “{{sub}}-{{word}}.{{suffix}}” -pp “word=api-keywords.txt” -es
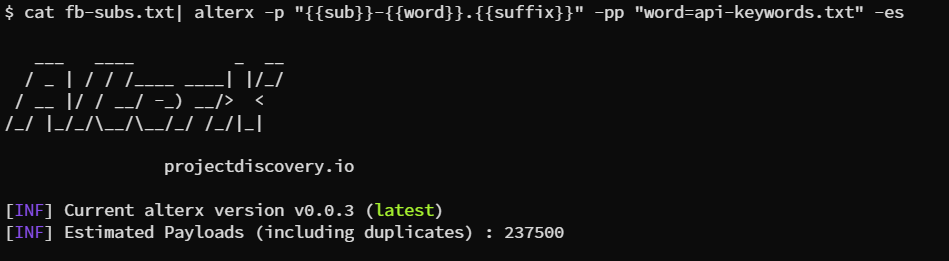
Numbers are depending on numbers of subdomains and keywords
Further the alterx can be combined with dnsx to find the alive subdomains
cat fb-subs.txt | alterx -p “{{sub}}-{{word}}.{{suffix}}” -pp “word=api-keywords.txt” -silent | dnsx -silent -o api-subdomains.txt
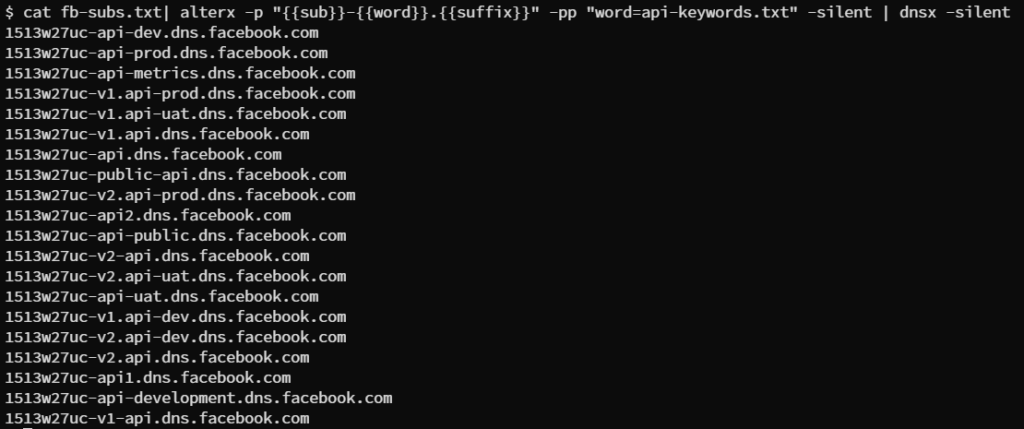
This will result in active API subdomains.
-> [Request Demo] - Get the Hacker’s View Of Your Attack Surface
API Discovery Via Directory Fuzzing
APIs can be deployed not only on subdomains but also within directories on web servers. For instance, a company’s website, such as http://company.com, which hosts its portfolio pages, can offer APIs through directories like /api and /v1/api. Detecting these directories containing the API can be achieved through a method known as “directory fuzzing.”
A fuzzing tool called FUFF can be used to perform the same scenario. The tool can be found at https://github.com/ffuf/ffuf.
Here are top keywords that can be used to enumerate the API’s
| # S.NO. | Path |
| 1 | api |
| 2 | v1/api |
| 3 | v2/api |
| 4 | apidocs |
| 5 | api/graphql |
| 6 | apikey |
| 7 | api/proxy |
| 8 | apis |
| 9 | api/v1 |
| 10 | nternal_api/1/accounts/ |
| 11 | internal_api/ |
| 12 | internal_api |
| 13 | api/v1/account/users |
| 14 | api/v1/account/users/password |
| 15 | api/v1/account/users/summaries |
| 16 | api/v1/asset/asset |
| 17 | api/v1/asset/assets |
| 18 | api/v1/common/accounts |
| 19 | api/v1/monitoring/accounts |
| 20 | api/3.0/artists/ |
Save the wordlist as a txt file and further pass it with ffuf on the target where you want to find out the API directories.
ffuf -u ‘https://company.com/FUZZ’ -w wordlist.txt
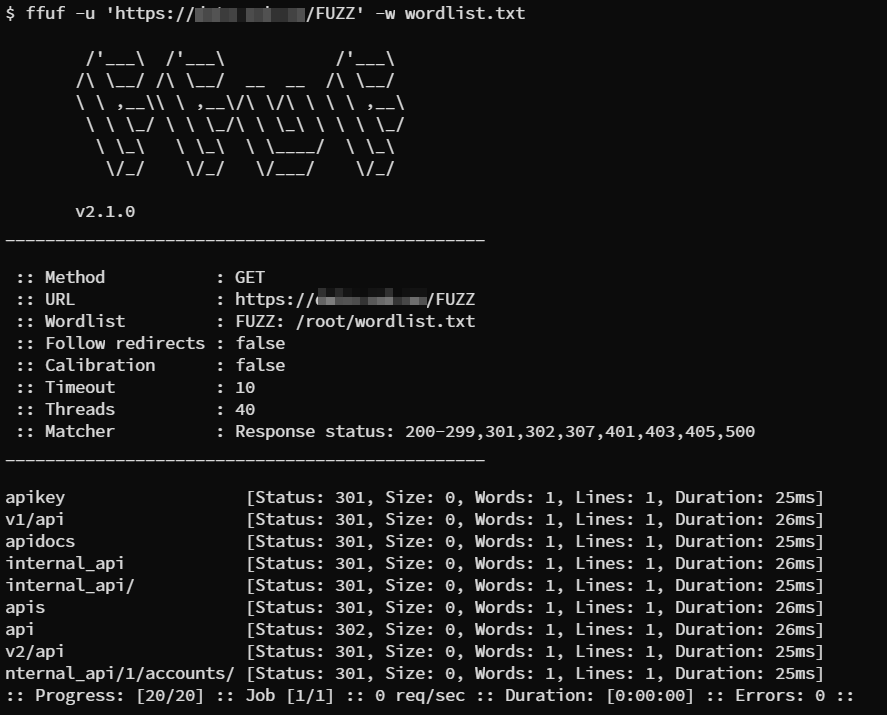
As a positive result we got multiple directories containing the possible API paths which can further have API’s in any of those.
POC Code for API Subdomains Discovery With Alterx
import subprocess
import sys
def run_subdomain_search(subdomain_list_file, api_keywords_file):
# Read the subdomain list from the file
with open(subdomain_list_file, ‘r’) as subdomain_file:
subdomains = subdomain_file.read().splitlines()
# Build the command with double curly braces for placeholders
command = f”cat {subdomain_list_file} | alterx -p ‘{{{{sub}}}}{{{{word}}}}.{{{{suffix}}}}’ -pp ‘word={api_keywords_file}’ -silent | dnsx -silent -o api-subdomains.txt”
# Print the command before running it
print(“Running the following command:”)
print(command)
# Execute the command and capture its output
try:
output = subprocess.check_output(command, shell=True, universal_newlines=True)
print(“nCommand output:”)
print(output)
print(“Subdomain search completed successfully.”)
except subprocess.CalledProcessError as e:
print(“nAn error occurred while running the subdomain search command.”)
print(e)
if __name__ == ‘__main__’:
if len(sys.argv) != 3:
print(“Usage: python subdomain_search.py <subdomain_list_file> <api_keywords_file>”)
else:
subdomain_list_file = sys.argv[1]
api_keywords_file = sys.argv[2]
run_subdomain_search(subdomain_list_file, api_keywords_file)
>> Discover & Test your Ransomware Attack Surface
POC Code For Api Discovery Via Directory Fuzzing
Since the directory fuzzing playbook is already available on the portal, That can be used with the keywords provided in the section API discovery via directory fuzzing.
By: FireCompass Research Team – Prashant Saini
About FireCompass:
FireCompass is a SaaS platform for Continuous Automated Pen Testing, Red Teaming and External Attack Surface Management (EASM). FireCompass continuously indexes and monitors the deep, dark and surface webs using nation-state grade reconnaissance techniques. The platform automatically discovers an organization’s digital attack surface and launches multi-stage safe attacks, mimicking a real attacker, to help identify breach and attack paths that are otherwise missed out by conventional tools.
Important Resources:
Get a free demo to find out how FireCompass can help you to prioritize risks with real-time alerts for faster detection and remediation.





