Critical CVEs And Active Threats: Apache Tomcat, GoAnywhere MFT, PAS and More
This week from January 22 to 25, the FireCompass research team identified a huge number of CVEs that are high in severity and ransomware, botnets, and threat actors creating havoc. Some of the CVEs identified are popular commercial products used by variants of industries and some new & well-known malwares targeting industries for this week. In this, we will list important CVEs discovered as well as the list of malware, threat actors and botnets which were most active along with the CVEs that they were using in their campaigns.
List of Critical Vulnerabilities That Were Exploited – FireCompass Research :
- CVE-2024-21733 – Apache Tomcat
- CVE-2024-22233 – Spring Framework
- CVE-2024-0204 – GoAnywhere MFT
- CVE-2023-40051 – Progress Application Server (PAS)
- CVE-2023-49657 – Apache Superset
- CVE-2023-50943, CVE-2023-50944, CVE-2023-51702 – Apache Airflow Multiple Vulnerability
List of Malwares And Threat Actors:
- CVE-2023-34048 – vCenter Server
-> Hackers Won't Wait For Your Next Pen Test: Know Automated Continuous Pen Test
Detailed Analysis: Vulnerabilities
CVE-2024-21733 – Apache Tomcat
CVE-2024-21733 is a vulnerability in Apache Tomcat that allows an attacker to potentially access sensitive information through incomplete POST requests, which trigger error messages containing that information. This vulnerability affects Apache Tomcat versions 8.5.7 through 8.5.63 and 9.0.0-M11 through 9.0.43. Users are advised to upgrade to versions 8.5.64 or 9.0.44 or later to address this issue.
![]()
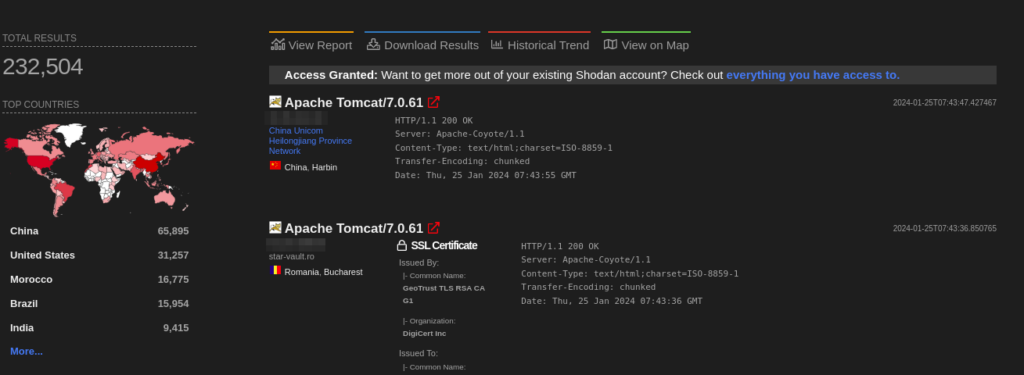
A total of more than 200k endpoints of Apache Tomcat are exposed on the Shodan.
CVE-2024-22233 – Spring Framework
CVE-2024-22233 is a serious vulnerability in Spring Framework versions 6.0.15 and 6.1.2 that could allow attackers to crash vulnerable applications using specially crafted requests. This effectively denies legitimate users access, causing a “denial-of-service” (DoS) attack. To stay protected, upgrade to Spring Framework 6.0.16 or 6.1.3, released January 11, 2024. Be safe!
![]()
A total of more than 500 endpoints of Spring Framework are exposed on the Shodan.
>> Find Critical Risks in 72 Hours & Continuous Risk Hunting (Request Demo)
CVE-2024-0204 – GoAnywhere MFT
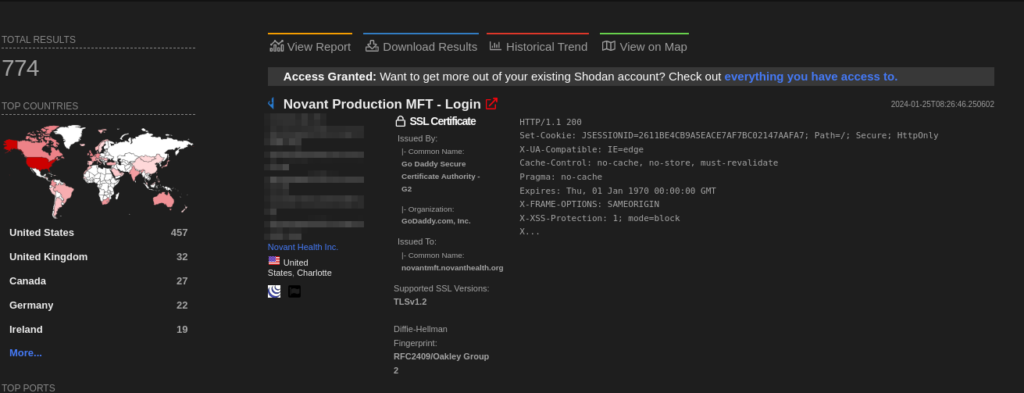
CVE-2024-0204 exposes a critical vulnerability in Fortra’s GoAnywhere MFT software versions before 7.4.1. This flaw allows any unauthenticated user to create an administrator account directly through the software’s administration portal, granting them complete control over sensitive data and system settings. Immediate upgrade to version 7.4.1 or later is strongly recommended to patch this severe security hole.
![]()
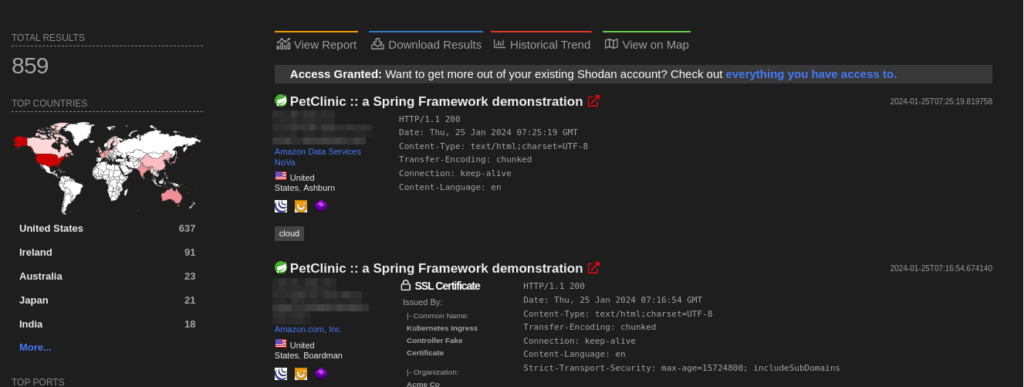
A total of more than 500 endpoints of GoAnywhere MFT are exposed on the Shodan.
CVE-2023-40051 – Progress Application Server (PAS)
Beware of sneaky file uploads! CVE-2023-40051 is a critical vulnerability in Progress Application Server (PAS) for OpenEdge versions before 11.7.18, 12.2.13, and 12.8.0. Imagine an attacker crafting a special request that tricks the server into accepting a file upload. This file could be malware, allowing the attacker to steal data, disrupt operations, or even hijack the server. Upgrade to patched versions 11.7.18, 12.2.13, or 12.8.0 (or later) immediately to plug this security hole!
![]()
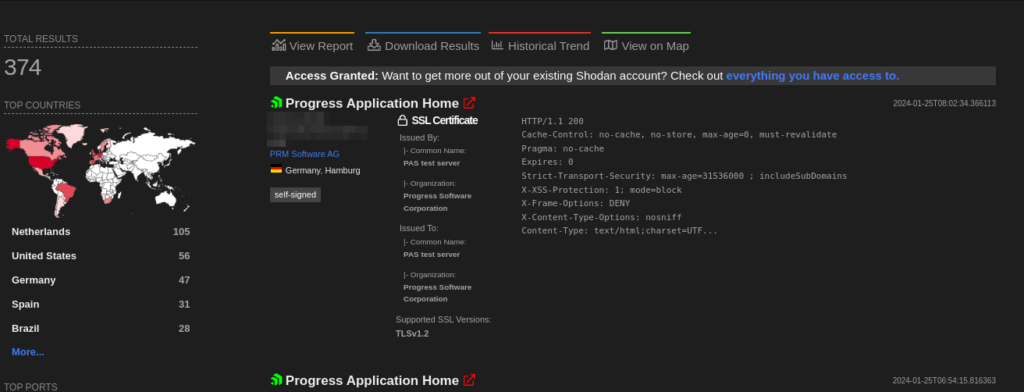
A total of more than 300 endpoints of PAS are exposed on the Shodan.
>> [Request RECON Demo] - Reconnaissance Techniques As Threat Actors
CVE-2023-49657 – Apache Superset
CVE-2023-49657 is a stored cross-site scripting (XSS) vulnerability lurking in Apache Superset versions before 3.0.3. It allows attackers with chart or dashboard creation/update permissions to inject malicious scripts or HTML snippets, which can then be executed by unsuspecting users who view those charts or dashboards.
![]()
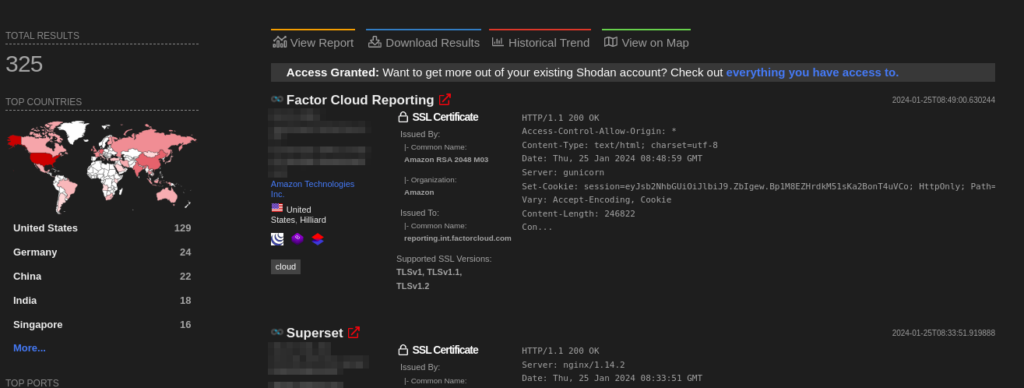
A total of more than 300 endpoints of Apache Superset are exposed on the Shodan.
CVE-2023-50943, CVE-2023-50944, CVE-2023-51702 – Apache Airflow Multiple Vulnerability:
CVE-2023-50943
Imagine a sneaky villain trying to tamper with Airflow’s internal data storage (XCom) to mess with your workflows. That’s essentially what CVE-2023-50943 is all about. This flaw in Airflow versions before 2.8.1 allows attackers to bypass a security setting and inject malicious data into XCom. While considered low risk as only workflow creators can exploit it, it’s still a chink in your Airflow armor.
CVE-2023-50944
Spying without access? Think again! CVE-2023-50944 lets nosy users in Airflow versions before 2.8.1 peek at the source code of workflows they shouldn’t have access to. While this vulnerability requires existing account credentials, it allows unauthorized snooping into workflows and potentially sensitive information. Don’t let your workflows become open books! Upgrade to Airflow 2.8.1 or later to lock the door and keep your workflows private.
CVE-2023-51702
Imagine a security guard accidentally shouting your top-secret password into a megaphone in a crowded street! That’s essentially what CVE-2023-51702 does in Airflow versions 5.2.0 to 6.9.9. This vulnerability exposes sensitive Kubernetes configuration files, allowing anyone with access to Airflow’s metadata or logs to easily snatch them and gain unauthorized access to your Kubernetes cluster. It’s like leaving your house keys dangling on a billboard for anyone to grab!
![]()
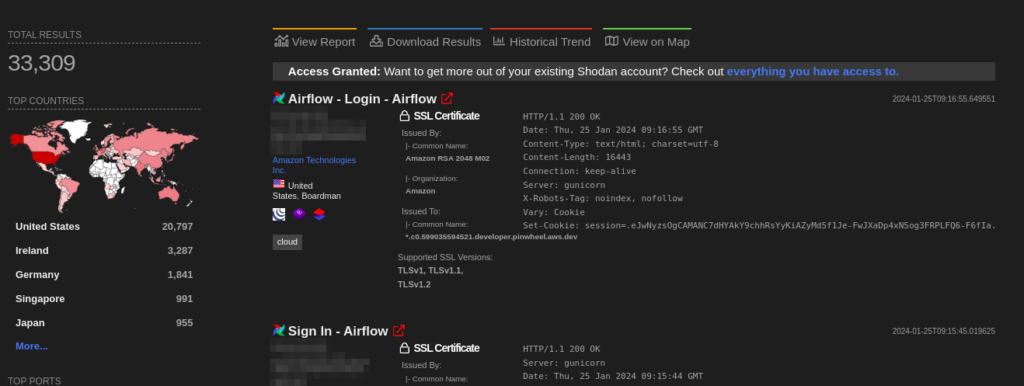
A total of more than 30K endpoints of Apache Airflow are exposed on the Shodan.
Important Weekly Threat Actors
CVE-2023-34048 – vCenter Server
A critical vCenter Server vulnerability dubbed CVE-2023-34048 was secretly exploited by a Chinese hacking group as a zero-day from late 2021 until its patch in October 2023. This previously undisclosed hack used maliciously crafted software bundles to deploy backdoors and steal data from virtual machines. Although details on the attacks are scarce, evidence suggests the group, known as UNC3886, leveraged this zero-day alongside another VMware flaw (CVE-2023-20867) to escalate privileges and pilfer sensitive information. This incident highlights the dangers of zero-day exploits and the importance of timely patching vulnerabilities.
![]()
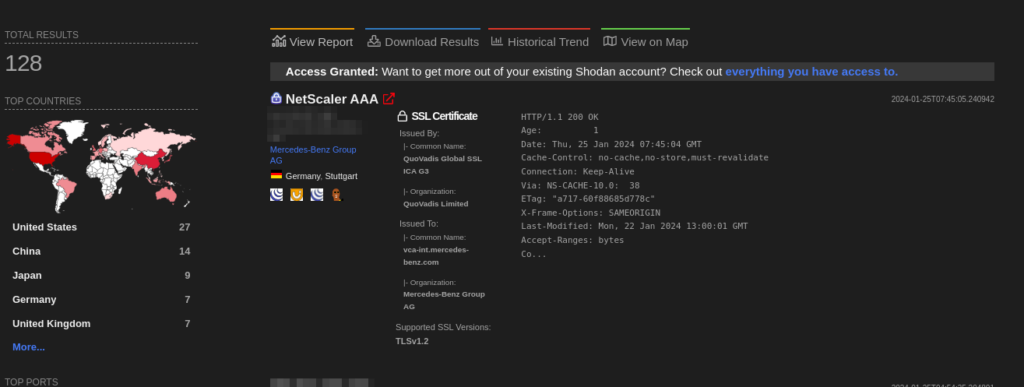
A total of 128 endpoints of vCenter Server are exposed on the Shodan.
Author: Debdipta Halder
Assisted By: Soumyanil Biswas, Faran Siddiqui, Anirban Bain
About FireCompass:
FireCompass is a SaaS platform for Continuous Automated Pen Testing, Red Teaming and External Attack Surface Management (EASM). FireCompass continuously indexes and monitors the deep, dark and surface webs using nation-state grade reconnaissance techniques. The platform automatically discovers an organization’s digital attack surface and launches multi-stage safe attacks, mimicking a real attacker, to help identify breach and attack paths that are otherwise missed out by conventional tools.
Feel free to get in touch with us to get a better view of your attack surface.


