Link-Local Multicast Name Resolution (LLMNR), a seemingly important protocol in Windows environments, can be a silent accomplice for cyber adversaries seeking to exploit network vulnerabilities. Let us understand the technical intricacies of LLMNR and unravel how it can be exploited for reconnaissance purposes, examining each step from a Red Teamer’s perspective.
Understanding LLMNR
LLMNR is a protocol designed to resolve names of neighboring computers in the absence of a Domain Name System (DNS) server. Operating on UDP port 5355, LLMNR serves as a backup mechanism for DNS resolution, enabling devices to discover local hosts without relying on centralized servers.
The Link-Local Multicast Name Resolution (LLMNR) is a protocol based on the Domain Name System (DNS) packet format that authorizes both IPv4 and IPv6 hosts to execute name resolution for hosts on the same local link.
>> Discover & Test your Ransomware Attack Surface
Protocol Operation
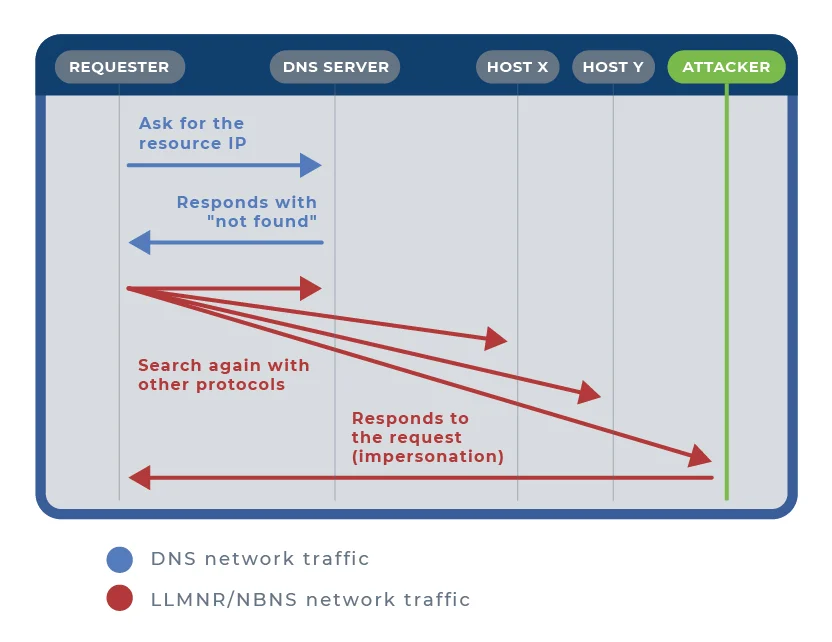
When a Windows device fails to resolve a name using DNS, it sends an LLMNR multicast query to the local network. This multicast query is sent to all devices on the subnet, asking if any device knows the resolution for the requested name. This simple mechanism can be exploited to gather sensitive information about network hosts.
When Will LLMNR Work?
Local Network:
LLMNR is designed for local networks, and it works well within the same subnet or broadcast domain.
DNS Failure:
LLMNR is used as a fallback mechanism when traditional DNS resolution fails. If a device cannot resolve a hostname through DNS, it may use LLMNR to try and resolve the name locally within the same subnet.
When Will LLMNR Not Work?
Across Subnets:
LLMNR is limited to the local subnet or broadcast domain. It doesn’t traverse routers or subnets, so it won’t work for devices on different subnets.
Disabled or Blocked:
LLMNR might not work if it’s explicitly disabled on a device or blocked by network policies. Some security policies or firewalls may block LLMNR traffic.
IPv6 Networks:
LLMNR is primarily designed for IPv4 networks. In IPv6 networks, though LLMNR can be employed in the environment, the multicast-based Neighbor Discovery Protocol (NDP) is used instead as it is a standard protocol for IPv6 Networks.
Security Concerns:
LLMNR may pose some security risks, as it operates in a broadcast/multicast fashion, making it susceptible to certain types of attacks such as spoofing or poisoning. For this reason, in some security-conscious environments, LLMNR might be disabled.
Alternative Mechanisms:
In environments where LLMNR is not suitable or disabled, other mechanisms like NetBIOS or mDNS (Multicast DNS) may be used for local name resolution.
-> [Request Demo] - Get the Hacker’s View Of Your Attack Surface
Concept Of LLMNR Exploitation
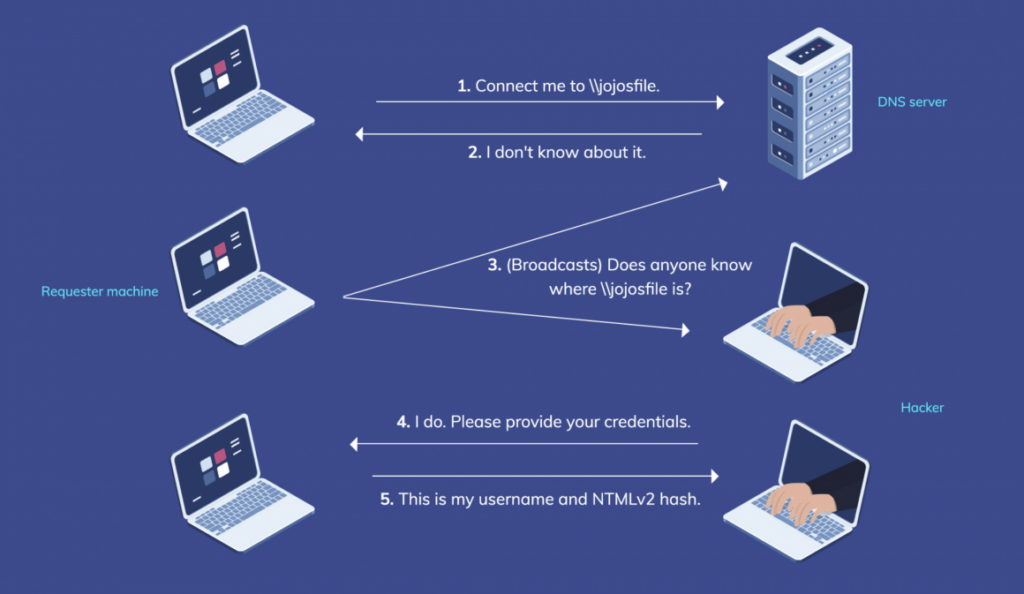
When the LLMNR multicast query is sent to the local network, the attacker sends the client feedback that he knows the network resource and sends him the IP of the desired resource. This IP is supposed to be used to reach the network resource, but it arrives at the server hosted by the attacker.
The client now sends a request to the IP address provided to it. So that the supposed authorization of the client can be checked, the attacker now requires authentication from the client. This can take place via basic auth or challenge response (such as Net-NTLMv2). After authentication, the client now receives an error message so that it appears as if the resource was not found after all. In most cases, authentication takes place without user interaction.
If the attacker has received Basic authentication, he can access resources using these Base64 encoded credentials. For example, if the attacker has received Net-NTLMv2 authentication, he can try to crack it in order to obtain the password of the respective user.
In connection with other misconfigurations, it is also possible to forward challenge-response authentications in order to gain direct access to systems.
-> (Request Demo) 10 X Pen Testing Frequency & 100% Asset Coverage
Types Of Exploitations Of LLMNR
LLMNR Poisoning In An Active Directory Environment:
LLMNR poisoning involves manipulating name resolution responses to redirect authentication requests. In an Active Directory setup, this can be achieved by intercepting LLMNR queries and responding with malicious information.
Attackers can use tools like Responder to capture Net-NTLMv2 hashes, which are often used for authentication in Windows environments.
Domain Controller Exploitation:
Successful LLMNR attacks can provide attackers with the credentials needed to compromise domain controllers. Once on a domain controller, they have access to the central repository of Active Directory data.
Attackers can modify AD objects, create new accounts, or manipulate security settings, potentially leading to a complete compromise of the domain.
Lateral Movement Within Active Directory:
Exploiting LLMNR can act as a pivot point for lateral movement. Attackers, armed with captured credentials, can move laterally within the AD environment.
They may target specific servers, workstations, or services, escalating privileges and extending their influence across the network.
Abuse Of Trust Relationships:
Active Directory relies on trust relationships between domains. LLMNR exploitation can be used to manipulate these trust relationships.
Attackers might abuse trust to move laterally between domains, potentially gaining access to resources in other parts of the organization.
Red Team Exercises And Active Directory Security Audits:
Red team exercises involving LLMNR exploitation simulate real-world scenarios to identify weaknesses in an organization’s Active Directory security.
Security audits should assess the effectiveness of existing defenses, response procedures, and the overall resilience of the Active Directory infrastructure against LLMNR-based attacks.
Exploiting LLMNR for Reconnaissance
- Wireshark Analysis:
To initiate the exploration, capture network traffic using Wireshark with a specific filter for LLMNR traffic:
wireshark udp.port == 5355
Analyzing captured packets provides insights into LLMNR activity, allowing Red Teamers to identify potential targets and understand the network’s structure.
- Responder Tool:
Responder, a powerful tool in the Red Teamer’s arsenal, exploits LLMNR by answering these multicast queries and capturing Net-NTLMv2 hashes. Installation involves:
git clone https://github.com/SpiderLabs/Responder.git
cd Responder
Execution is initiated with:
python Responder.py -I <interface> -w -r -f
-I: Specifies the network interface.
-w: Enables WPAD poisoning (Web Proxy Auto-Discovery)
-r: Activates SMB and HTTP rogue authentication.
-f: Forces NTLMv2 authentication.
- Capturing Hashes:
As Windows devices attempt to resolve names through LLMNR, Responder captures Net-NTLMv2 hashes. These hashed credentials can subsequently be cracked offline or employed in Pass-the-Hash attacks for unauthorized access. - Pass-the-Hash (PtH) Attack:
With obtained hashes, Red Teamers can execute lateral movement within the network. Utilizing tools like psexec, they pass the hash for authentication:
psexec \target -s -c <malicious_payload.exe>
This command executes the payload on the target machine using the captured hash, demonstrating the real-world impact of LLMNR exploitation.
Mitigating LLMNR Exploitation
- Group Policy:
Organizations can proactively mitigate LLMNR exploitation by disabling it through Group Policy. The policy to “Turn off Multicast Name Resolution” can be configured under:
Computer Configuration -> Administrative Templates -> Network -> DNS Client
Setting this policy to “Enabled” prevents Windows devices from using LLMNR.
- Network Segmentation:
Network segmentation plays a crucial role in minimizing the impact of successful LLMNR exploitation. Restricting unnecessary communication between subnets limits the attacker’s ability to move laterally.
- Intrusion Detection Systems (IDS):
Implementing IDS rules to detect abnormal LLMNR traffic patterns is essential. Anomalies, such as unusual spikes in LLMNR queries, can serve as early indicators of potential malicious activity. - Continuous Pentesting, How FireCompass can help?
Engaging in Continuous Pentesting, plays a crucial role in identifying and mitigating LLMNR vulnerabilities. By regularly simulating real-world attacks, the Red Teamer assesses network weaknesses, analyzes traffic for anomalies, and tests the effectiveness of security controls. This proactive approach allows for ongoing adjustments to configurations, patch management, and access controls, ultimately strengthening the organization’s resilience against potential LLMNR-related exploits and making the Continuous Pentesting process Automated, leaves us no room for overlooking even the slightest vulnerability.
-> Hackers Won't Wait For Your Next Pen Test: Know Automated Continuous Pen Test
Conclusion
In conclusion, LLMNR, though designed for convenience, can inadvertently expose organizations to significant security risks. This deep dive into LLMNR exploitation provides a roadmap for understanding the protocol’s nuances and outlines effective mitigation strategies. By adopting a proactive approach to secure network protocols, organizations can fortify their defenses against potential threats, ensuring a robust Cyber Security posture in the face of evolving challenges.
By: FireCompass Delivery Team – K Surya Sai Harsha, Arnab Chattopadhayay, Joy Sen
About FireCompass:
FireCompass is a SaaS platform for Continuous Automated Pen Testing, Red Teaming and External Attack Surface Management (EASM). FireCompass continuously indexes and monitors the deep, dark and surface webs using nation-state grade reconnaissance techniques. The platform automatically discovers an organization’s digital attack surface and launches multi-stage safe attacks, mimicking a real attacker, to help identify breach and attack paths that are otherwise missed out by conventional tools.
Feel free to get in touch with us to get a better view of your attack surface.










