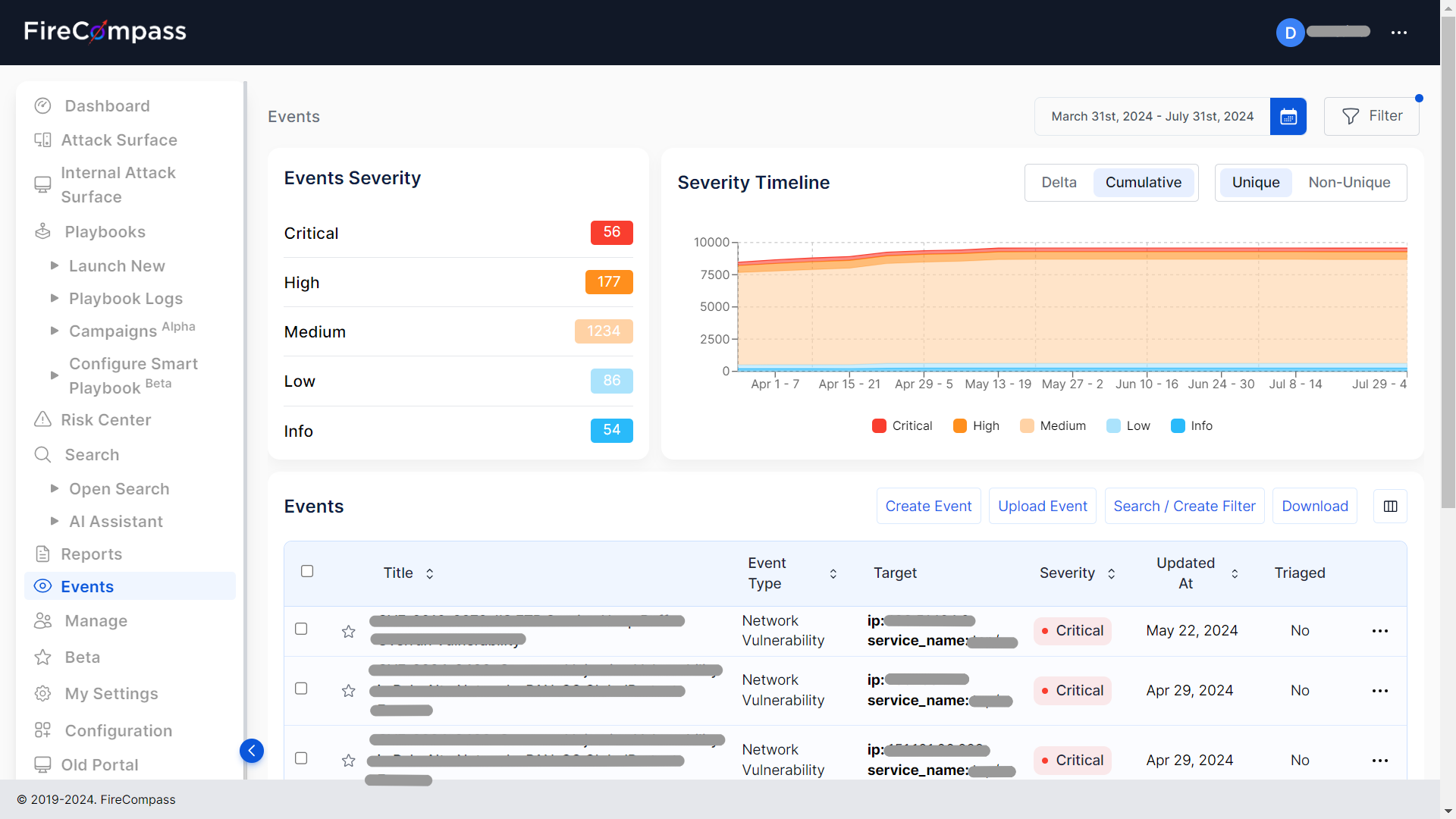
• Vulnerability Scanning: Using automated tools to identify and report on potential security weaknesses in your network and systems.
• Social Engineering: Manipulating people into giving up confidential information or performing unauthorized actions.
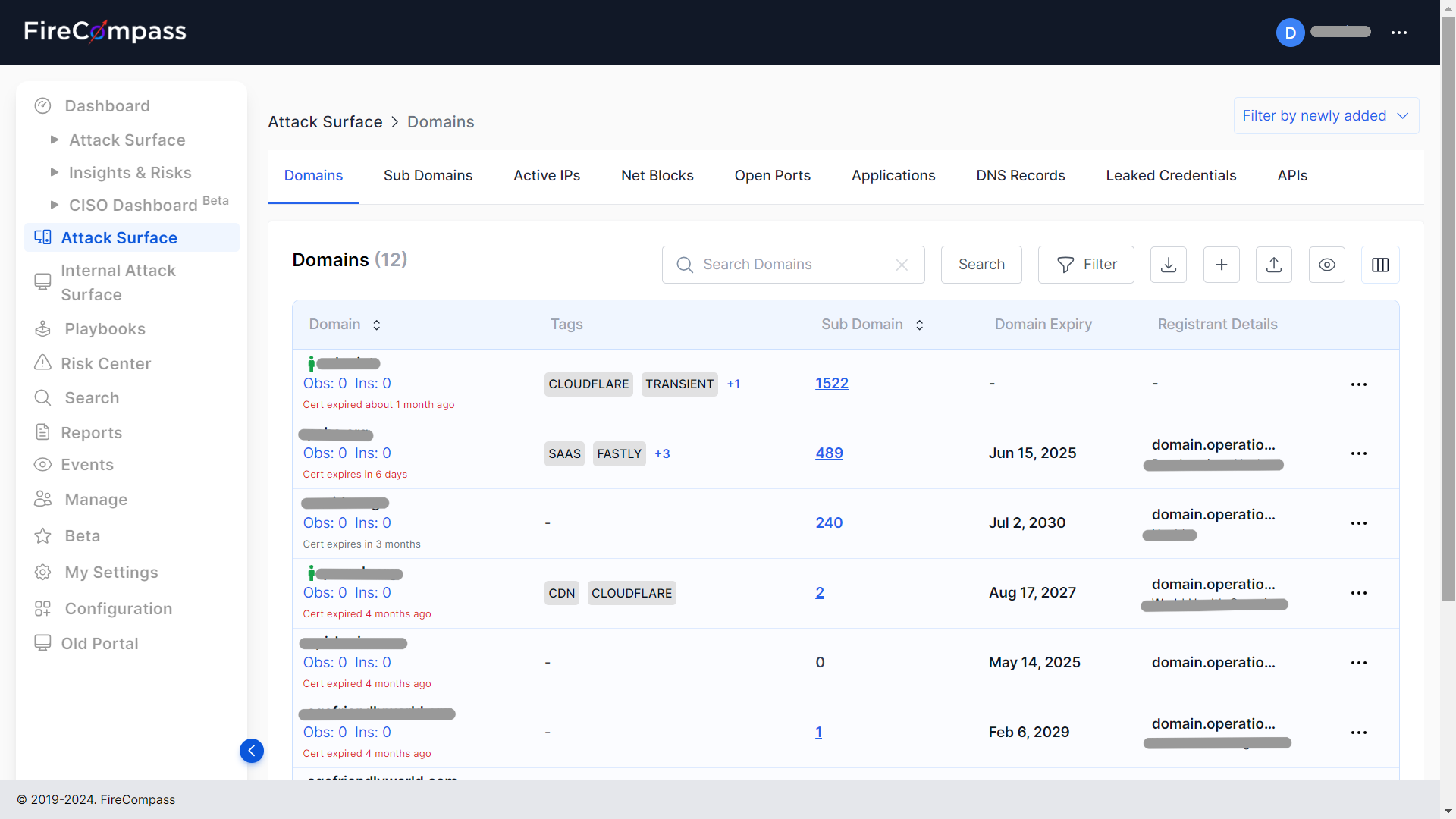
• Network Mapping: Utilizing tools to map out a network’s topology and identify potential entry points.
• Penetration Testing: Using automated tools and manual methods to identify and exploit weaknesses in your networks and systems.
• Physical Security Testing: Utilizing physical reconnaissance and covert methods to assess the physical security of your organization.
• Malware Analysis: Examining malicious code to better understand the nature and purpose of the attack.
• Database Enumeration: Utilizing tools to identify and retrieve information from databases.
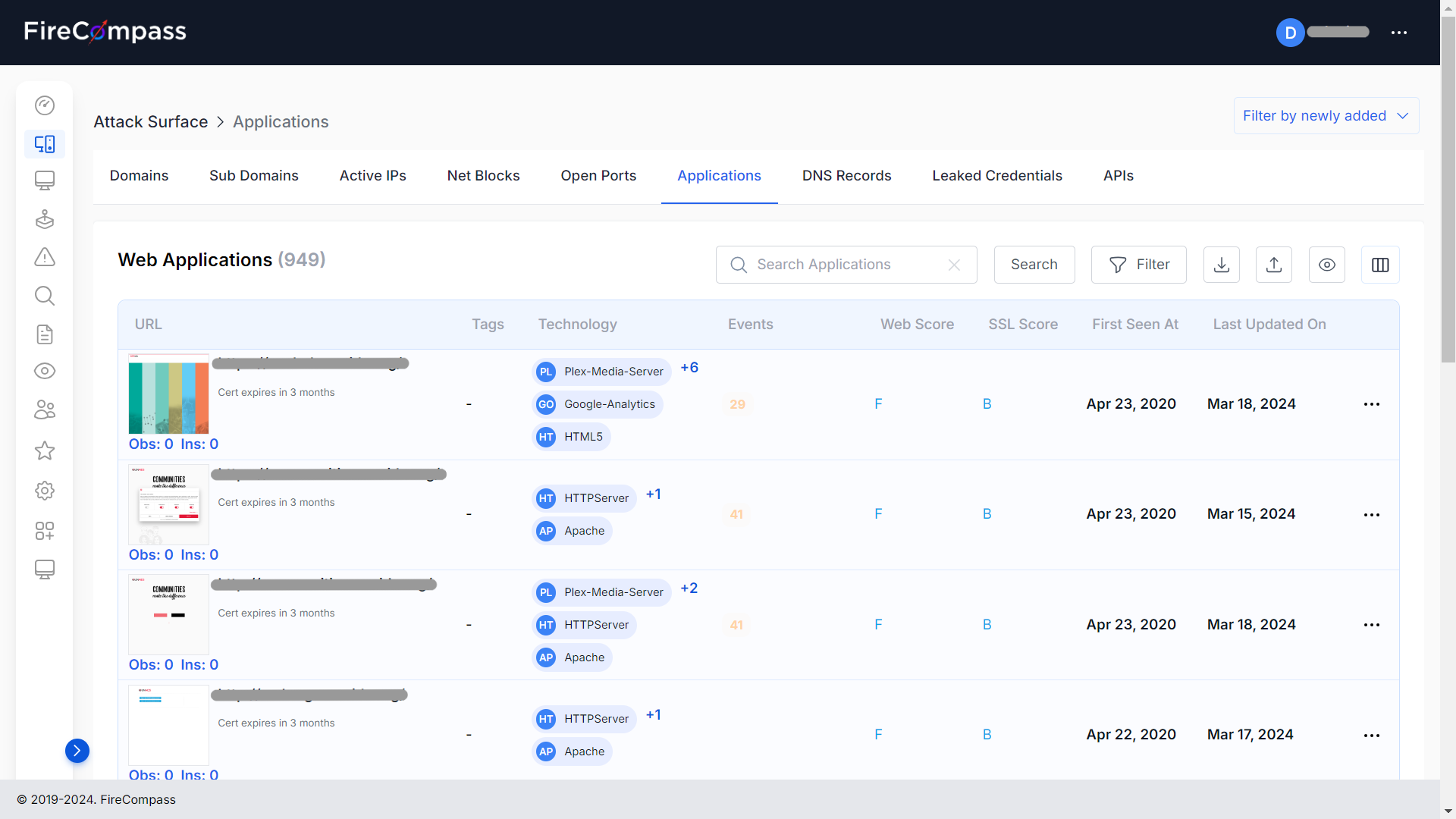
• Application Security Testing: Utilizing tools to evaluate the security of web and mobile applications.
• Wireless Network Testing: Utilizing tools to assess the security of wireless networks.
• Phishing Campaigns: Utilize emails to employees or partners to gain initial access or information about systems including credentials.