
In the ever-evolving landscape of digital connectivity and technology, organizations face an incessant challenge to fortify their cyber defenses against an ever-expanding array of threats. The rapid advancement of information technology has brought about unparalleled convenience and efficiency, but it has also ushered in an era where the vulnerability of digital ecosystems is a constant concern. Recent times have witnessed the emergence of critical vulnerabilities that have the potential to compromise the security and integrity of systems on a global scale.
This is a case study of CVEs that were trending from November to December 2023 which are critical in nature, been exploited by attackers and affected the organization’s overall. This list consists of popular products with critical and high CVSS score CVES.
This case study aims to shed light on the intricacies surrounding a series of recent critical vulnerabilities that have sent shockwaves through the cybersecurity community. As we delve into the depths of these vulnerabilities, we will unravel the technical nuances, assess the potential impact on affected systems, and explore the subsequent response mechanisms employed by organizations and security experts.
SysAid Remote Code Execution Vulnerabilities – CVE-2023-47246
SysAid is a cloud-based IT service management (ITSM) platform that helps organizations streamline their IT operations and deliver a better service experience to their employees. It offers a wide range of features, including:
- Help desk: A ticketing system for managing incident reports, service requests, and other customer interactions.
- Asset management: Track and manage IT assets, such as computers, servers, and network devices.
- Change management: Manage changes to the IT environment in a controlled and coordinated manner.
CVE-2023-47246 is regarding a critical zero-day vulnerability on their SysAid On-Premise software. This is a path traversal vulnerability that allows threat actors to gain unauthorized access to affected systems and execute arbitrary code.
The complete file path was “C:\Program Files\SysAidServer\tomcat\webapps\usersfiles“. The unauthorized access and control over the system were facilitated by a WebShell. Following this, the attacker employed a PowerShell script, delivered via the WebShell, to run a malware loader called “user.exe” on the compromised system. This loader was utilized to inject the GraceWire trojan into one of the specified processes: spoolsv.exe, msiexec.exe, or svchost.exe.

A sequence of actions illustrating how threat actors exploit the CVE-2023-47246 vulnerability to gain unauthorized access to the SysAid system.
We can find the attack surface on shodan by [http.html:”SysAid”] query.
OwnCloud Sensitive Data Exposure – CVE-2023-49103
OwnCloud is a widely used open-source file synchronization and sharing solution. It is convenient to store files in the cloud, so they are available on any device and can be shared with a few clicks.
On November 21, 2023. The software developers of OwnCloud published an advisory for the vulnerability disclosed as CVE-2023-49103 which is an unauthenticated information disclosure, which lets an attacker access sensitive information for version 0.2.x before 0.2.1 and 0.3.x before 0.3.1.
On November 25, 2023. Mass exploitation of this vulnerability in the wild by unknown threat actors led to CISA listing this CVE on November 30, 2023.
This vulnerability allows an unauthenticated attacker to leak sensitive information via the output of the file “PHPINFO()“ when targeting the URI “/apps/graphapi/vendor/microsoft/microsoft-graph/tests/GetPhpInfo.php“
This leads to exposing environment variables which contain usernames and passwords for ownCloud systems.
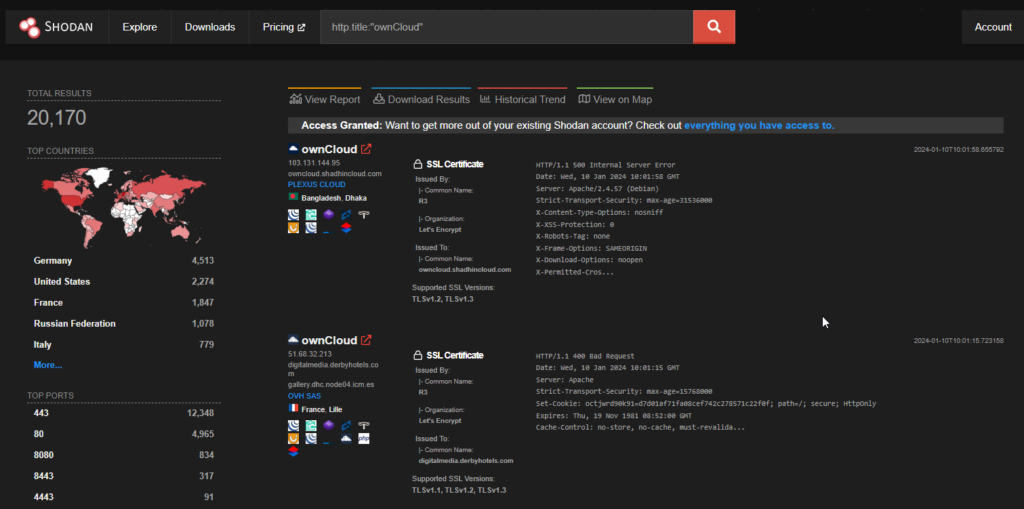
Shodan shows approximately 20k endpoints exposed.
Here a python script for exploitation
https://github.com/creacitysec/CVE-2023-49103
Where a list of URL needs to be supplies in which this script check and verify the presence of vulnerable URI
The recommended fix is to delete the ‘owncloud/apps/graphapi/vendor/microsoft/microsoft-graph/tests/GetPhpInfo.php’ file, disable the ‘phpinfo’ function.
Netgate PFSense and PFSense Plus – CVE-2023-48123
pfSense is an open-source firewall and router software distribution based on FreeBSD that is designed to provide advanced network security, routing, and other features. It originated as a fork of the m0n0wall project and has evolved into a powerful and flexible platform used by individuals, small businesses, and enterprises.
pfSense Plus is an enhanced, commercially supported version of pfSense offered by Netgate. While the core pfSense software is open-source and freely available, pfSense Plus includes additional features, improvements, and official support services provided by Netgate. It’s designed for users who require additional support, advanced features, and a commercially backed solution for their network security needs.
From November and December 2023, Netgate PFSense and PFSense Plus released 1 High level vulnerability known as CVE-2023-48123 which was exploited in the wild.
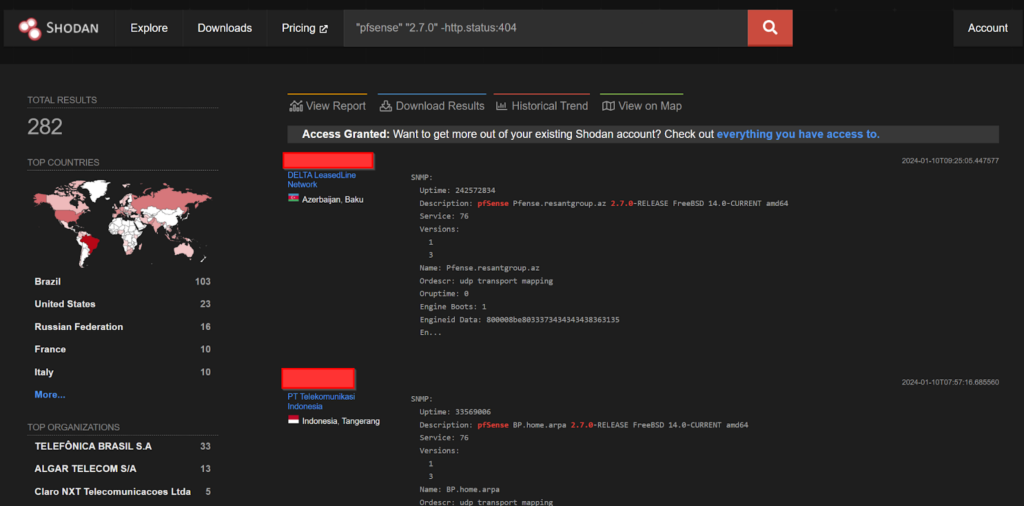
Shodan shows over 200 endpoints being exposed to the public.
The basic premise of this vulnerability is that pfsense fails to control the data sent by the user in the file packet_capture.php, allowing an authenticated remote attacker to execute arbitrary code by sending specifically forged requests.
Sophos Firewall Code Injection Vulnerability – CVE-2022-3236
Sophos Firewall offers the enterprise-grade protection, performance, visibility, and SD-WAN features that you need for today’s most demanding networks. From November and December 2023, Sophos Firewall released 1 High level vulnerability known as CVE-2022-3236 which was exploited in the wild.
The flaw is in the User Portal and Webadmin of Sophos Firewall which lets the attacker execute remote code.
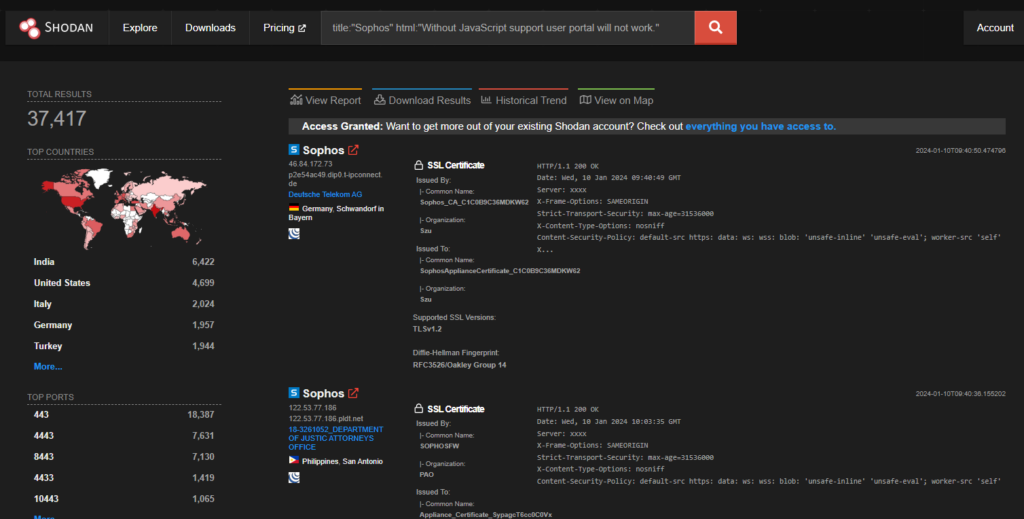
As per shodan, there are approximately 37k endpoints exposed on the internet that are vulnerable to this attack.
The presence of “_discriminator“ field and “/log/validationError.log“ is a sufficient indication for exploitation attempts.
It is advised users to update to the latest version of Sophos Firewall.
Author: Debdipta Halder
Assisted By: Soumyanil Biswas, Faran Siddiqui, Anirban Bain
About FireCompass:
FireCompass is a SaaS platform for Continuous Automated Pen Testing, Red Teaming and External Attack Surface Management (EASM). FireCompass continuously indexes and monitors the deep, dark and surface webs using nation-state grade reconnaissance techniques. The platform automatically discovers an organization’s digital attack surface and launches multi-stage safe attacks, mimicking a real attacker, to help identify breach and attack paths that are otherwise missed out by conventional tools.
Feel free to get in touch with us to get a better view of your attack surface.





