In November 2023, FireCompass research identified a huge number of CVEs that are high in severity and ransomware, botnets, and threat actors creating havoc. Some of the CVEs identified are of popular commercial products used by variants of industries and some new & well known malwares targeting industries for this Month. In this blog, we will list important CVEs discovered as well as list of malware, threat actors and botnets which were most active along with the CVEs that they were using in their campaigns.
Sample List of Critical Vulnerabilities That Were Exploited In November – FireCompass Research
- CVE-2023-46604 – Apache ActiveMQ
- CVE-2023-22518 – Atlassian Confluence Data Center improper authorization
- CVE-2023-48029 – CoreBos CSV Injection
- CVE-2023-26205 – FortiADC Automation Privilege Escalation
- CVE-2023-34991 – Fortinet FortiWLM SQL Command Injection
- Microsoft Exchange Vulnerabilities
- Adobe Coldfusion Vulnerabilities
Top Malwares And Threat Actors of November
- CVE-2023-46604 – TellYouThePass ransomware
- CVE-2019-0708 – Kimsuky
- CVE-2023-4966 – LockBit Ransomware Gang
- CVE-2023-40044 and CVE-2023-42657 – Dark Pink APT
Weekly Digest : Critical CVEs Published In November Month
Week 1: Critical CVEs and Active Threat Actors
Week 2: Critical CVEs and Active Threat Actors
Week 3: Critical CVEs and Active Threat Actors
Week 4: Critical CVEs and Active Threat Actors
Detailed Analysis :
Top Vulnerabilities Being Exploited in November
CVE-2023-46604 – Apache ActiveMQ
Apache ActiveMQ is vulnerable to Remote Code Execution.The vulnerability may allow a remote attacker with network access to a broker to run arbitrary shell commands by manipulating serialized class types in the OpenWire protocol to cause the broker to instantiate any class on the classpath. Users are recommended to upgrade to version 5.15.16, 5.16.7, 5.17.6, or 5.18.3, which fixes this issue.
Here are the industries and companies that are affected by this CVE.
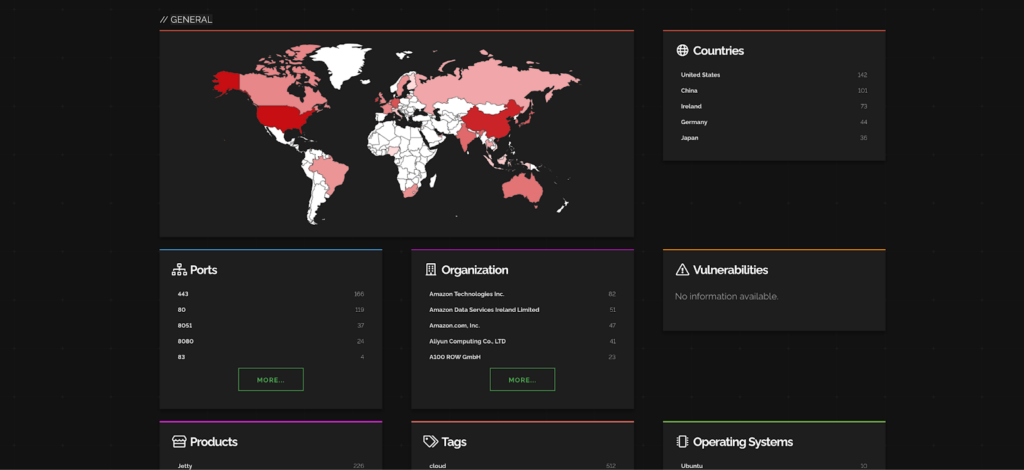

Ref: Shodan
Most impacted countries are USA and China while Amazon Services are getting affected the most.
CVE-2023-22518 – Atlassian Confluence Data Center Improper Authorization
Atlassian Confluence Data Center and Server has improper authorization which allows an unauthenticated attacker to reset Confluence and create a Confluence instance administrator account. Using this account, an attacker can then perform all administrative actions that are available to Confluence instance administrators leading to – but not limited to – full loss of confidentiality, integrity and availability.
This CVE has been listed in CISA exploited in the wild list for this week.

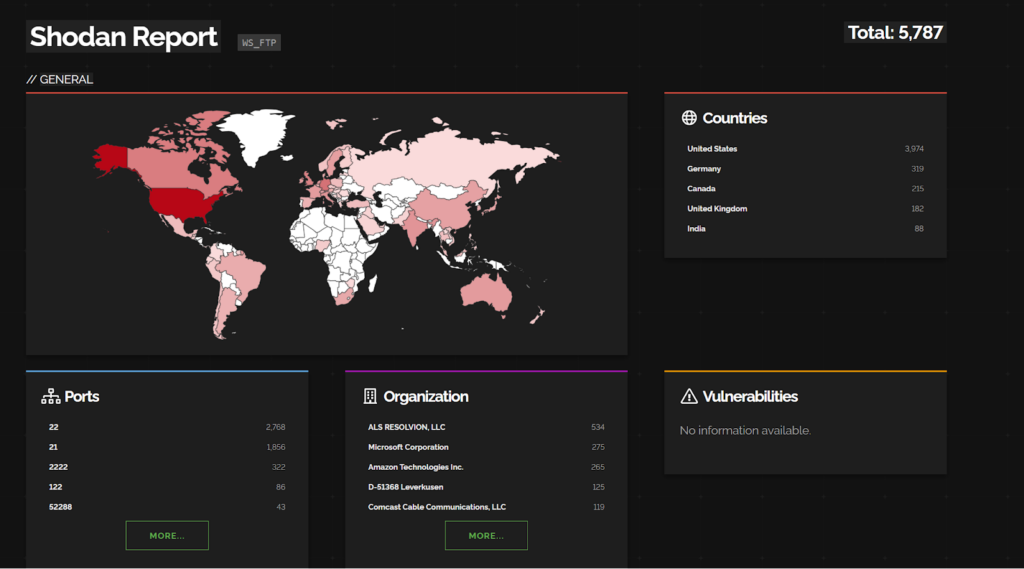
CVE-2023-48029 – CoreBos CSV Injection
CoreBos is an open-source and free business application framework that helps small and medium businesses to handle all the day to day tasks. Corebos 8.0 and below is vulnerable to CSV Injection. An attacker with low privileges can inject a malicious command into a table. This vulnerability is exploited when an administrator visits the user management section, exports the data to a CSV file, and then opens it, leading to the execution of the malicious payload on the administrator’s computer.
POC Link – https://nitipoom-jar.github.io/CVE-2023-48029/
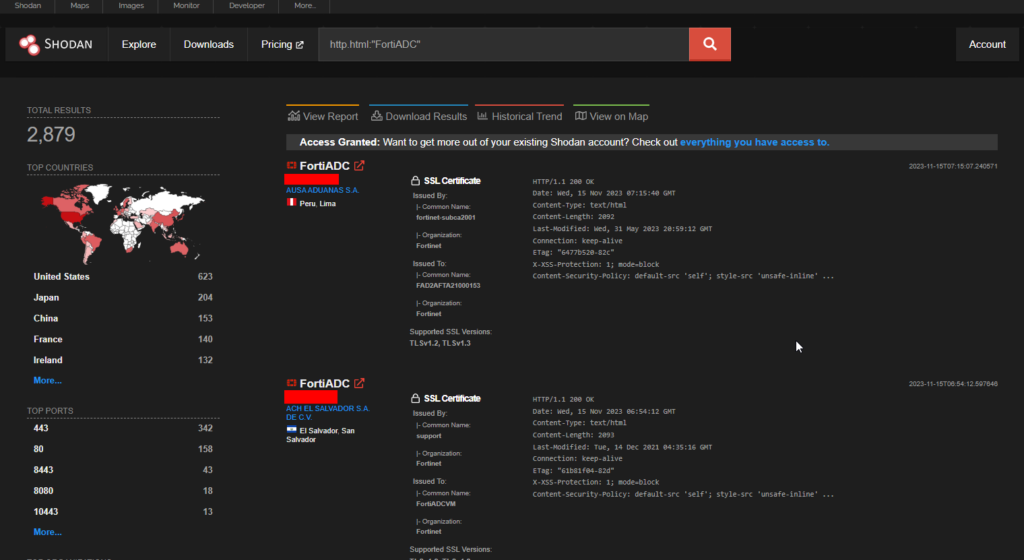

Shodan shows 2879 endpoints and the USA has the most number of them.
-> Hackers Won't Wait For Your Next Pen Test: Know Automated Continuous Pen Test
CVE-2023-26205 – FortiADC Automation Privilege Escalation
FortiADC Automation version 7.1.0 through 7.1.2, 7.0 all versions, 6.2 all versions, 6.1 all versions may allow an authenticated low-privileged attacker to escalate their privileges to super_admin via a specific crafted configuration of fabric automation CLI script.


Shodan shows 2879 endpoints and the USA has the most number of them.
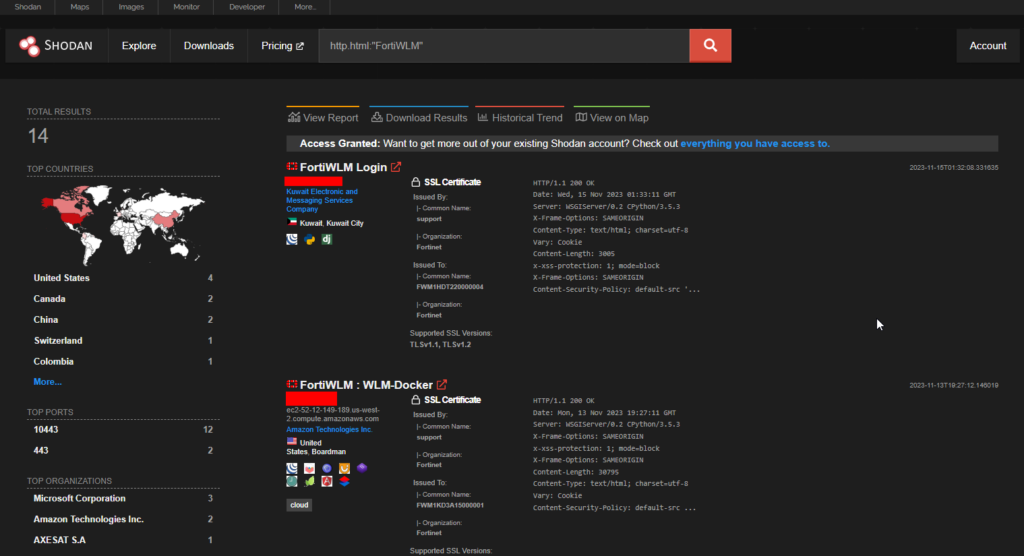
CVE-2023-34991 – Fortinet FortiWLM SQL Command Injection
A improper neutralization of special elements used in an sql command (‘sql injection’) in Fortinet FortiWLM version 8.6.0 through 8.6.5 and 8.5.0 through 8.5.4 and 8.4.0 through 8.4.2 and 8.3.0 through 8.3.2 and 8.2.2 allows attacker to execute unauthorized code or commands via a crafted http request.

>> Find Critical Risks in 72 Hours & Continuous Risk Hunting (Request Demo)
Microsoft Exchange Server Vulnerabilities
This on 14th November, 2023 – Tuesday was the Microsoft Patch Tuesday where they disclosed several numbers of vulnerabilities. One of them being the popular Microsoft Exchange Server which is a prime target for threat actors. Four vulnerabilities were released, here is the list.
- CVE-2023-36035 – Microsoft Exchange Server Spoofing Vulnerability
- CVE-2023-36039 – Microsoft Exchange Server Spoofing Vulnerability
- CVE-2023-36050 – Microsoft Exchange Server Spoofing Vulnerability
- CVE-2023-36439 – Microsoft Exchange Server Remote Code Execution

>> [Request RECON Demo] - Reconnaissance Techniques As Threat Actors
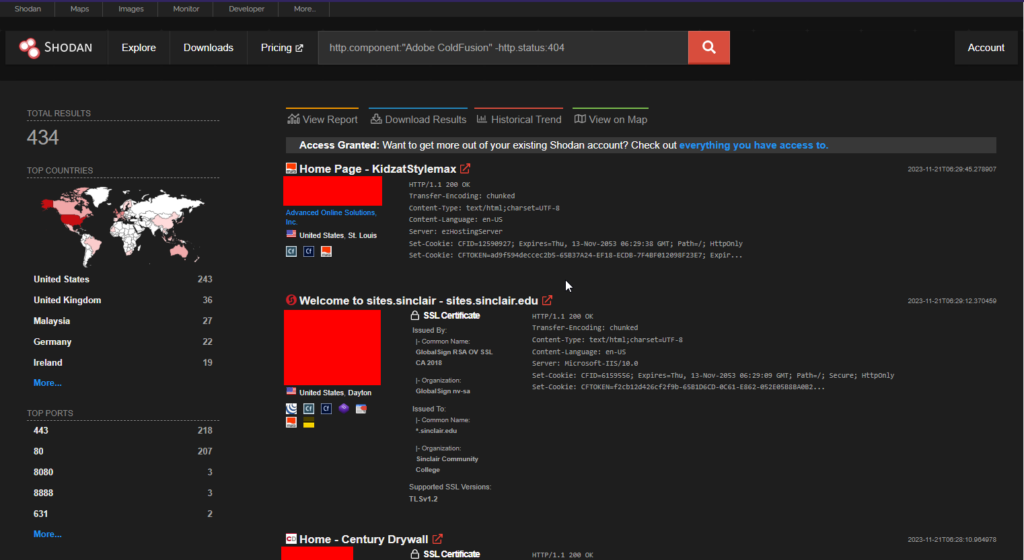
Adobe Coldfusion Vulnerabilities
Adobe Coldfusion is a popular web application development tool which had a fair share of vulnerabilities this year along with various threat actors abusing it. This week it released five CVEs in version 2023.5
- CVE-2023-26347 – Improper Access Control vulnerability
- CVE-2023-44350 – Deserialization to RCE
- CVE-2023-44351 – Deserialization to RCE
- CVE-2023-44352 – Reflected Cross-Site Scripting (XSS)
- CVE-2023-44353 – Deserialization to RCE

-> [Request Demo] - Get the Hacker’s View Of Your Attack Surface
Detailed Analysis: Top Malwares And Threat Actors Of November
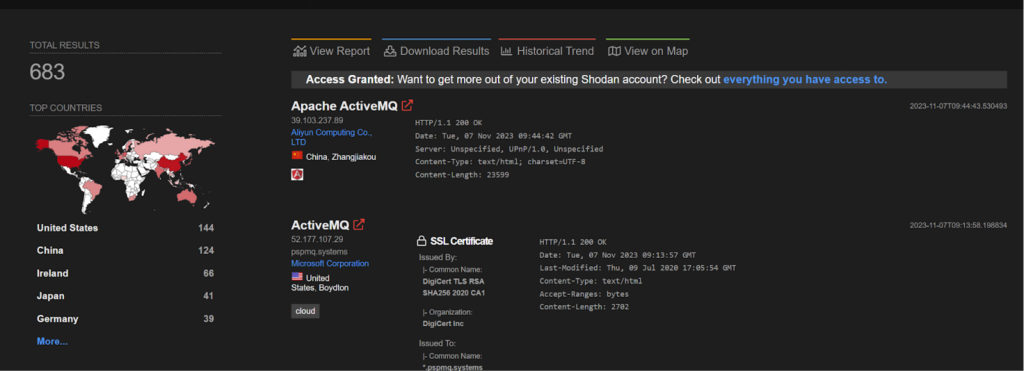
CVE-2023-46604 – TellYouThePass ransomware
Apache ActiveMQ is vulnerable to Remote Code Execution. The vulnerability may allow a remote attacker with network access to a broker to run arbitrary shell commands by manipulating serialized class types in the OpenWire protocol to cause the broker to instantiate any class on the classpath. This vulnerability was found to be exploited by a ransomware group named, TellYouThePass ransomware.
The POC of the above vulnerability can be found here: https://github.com/SaumyajeetDas/CVE-2023-46604-RCE-Reverse-Shell-Apache-ActiveMQ

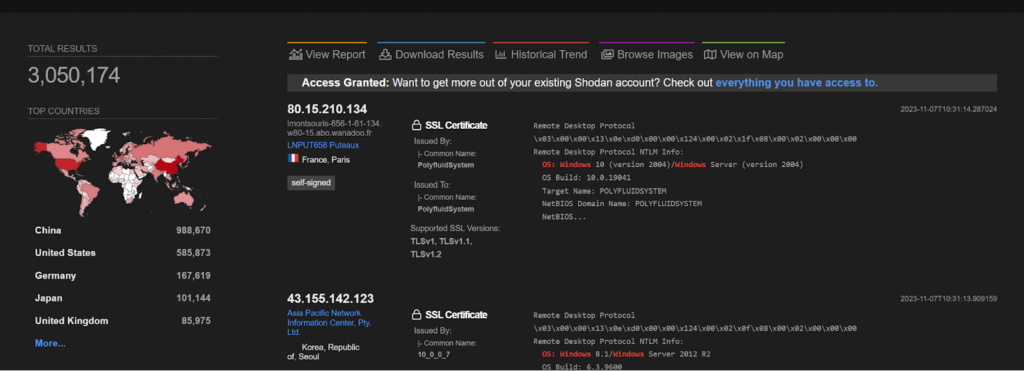
CVE-2019-0708 – Kimsuky
A remote code execution vulnerability exists in Remote Desktop Services formerly known as Terminal Services when an unauthenticated attacker connects to the target system using RDP and sends specially crafted requests, aka ‘Remote Desktop Services Remote Code Execution Vulnerability’. This vulnerability was found to be exploited by a North Korean state backed hacker group named, Kimsuky.
The POC of the above vulnerability can be found here: https://packetstormsecurity.com/files/162960/Microsoft-RDP-Remote-Code-Execution.html

>> (Learn More) "Automated Pen Testing Significantly Improved The Depth & Breadth Of Testing" - Ed Adams, Security Innovation
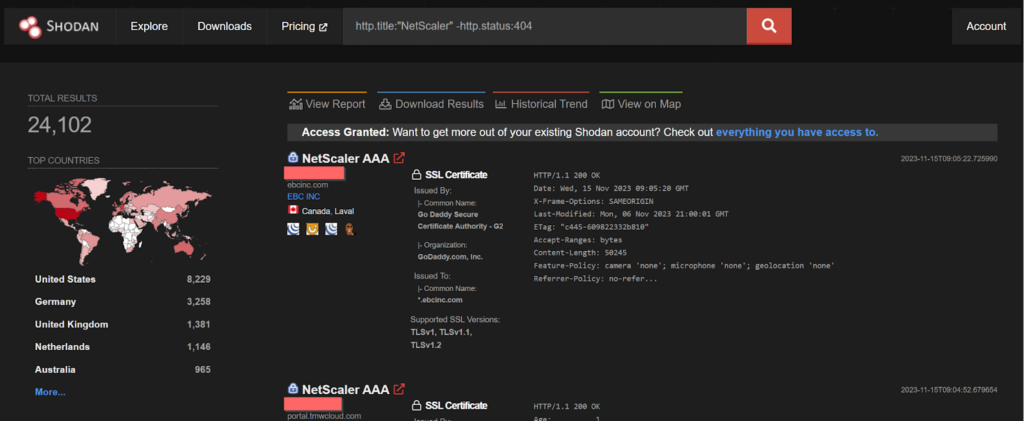
CVE-2023-4966 – LockBit Ransomware Gang
Sensitive Information Disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA virtual server. This vulnerability is found to be exploited by the LockBit ransomware gang.
POC of the above vulnerabilty:
https://github.com/mlynchcogent/CVE-2023-4966-POC

CVE-2023-40044 and CVE-2023-42657 – Dark Pink APT
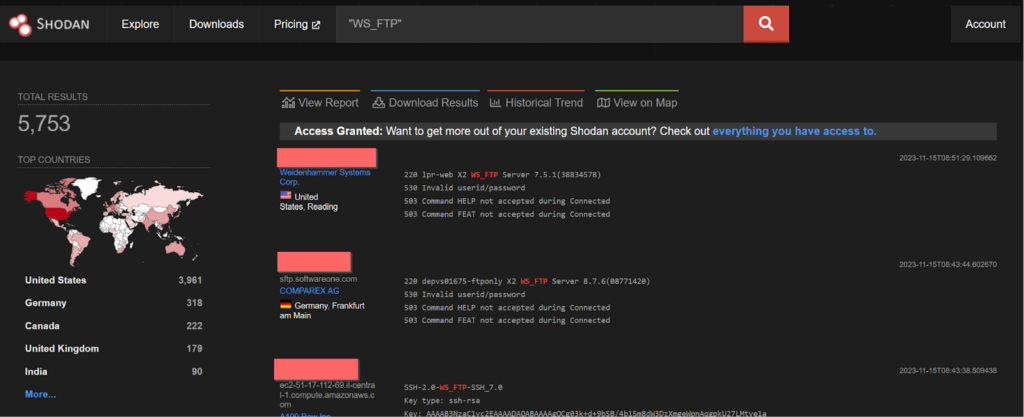
In WS_FTP Server versions prior to 8.7.4 and 8.8.2, a pre-authenticated attacker could leverage a .NET deserialization vulnerability in the Ad Hoc Transfer module to execute remote commands on the underlying WS_FTP Server operating system and
a directory traversal vulnerability was discovered. An attacker could leverage this vulnerability to perform file operations on files and folders outside of their authorized WS_FTP folder path. Attackers could also escape the context of the WS_FTP Server file structure and perform the same level of operations (delete, rename, rmdir, mkdir) on file and folder locations on the underlying operating system. These vulnerabilities are found to be exploited by Dark Pink APT group.
PoC for CVE-2023-40044:
http://packetstormsecurity.com/files/174917/Progress-Software-WS_FTP-Unauthenticated-Remote-Code-Execution.html

-> (Request Demo) 10 X Pen Testing Frequency & 100% Asset Coverage
By: Firecompass Research Team – Debdipta Halder, Soumyanil Biswas, Faran Siddiqui, Anirban Bain
FireCompass Day 1 CVE Playbook: Find Critical Risks in 24 Hrs:
FireCompass “Day 1 CVE Asset Exposure” Playbook can discover CVEs with Critical and High severity within 24 hours to 72 hours of them becoming public. This helps our customers to find and fix critical issues before exploits become available.
FireCompass is a SaaS platform for Continuous Automated Pen Testing, Red Teaming and External Attack Surface Management (EASM). FireCompass continuously indexes and monitors the deep, dark and surface webs using nation-state grade reconnaissance techniques. The platform automatically discovers an organization’s digital attack surface and launches multi-stage safe attacks, mimicking a real attacker, to help identify breach and attack paths that are otherwise missed out by conventional tools.
Feel free to get in touch with us to get a better view of your attack surface.


