This week from November 6 to November 10, FireCompass research identified a huge number of CVEs that are high in severity and ransomware, botnets, and threat actors creating havoc. Some of the CVEs identified are of popular commercial products used by variants of industries and some new & well known malwares targeting industries for this week. In this, we will list important CVEs discovered this week as well as list of malware, threat actors and botnets which were most active this week along with the CVEs that they were using in their campaigns.
The Key Vulnerabilities that FireCompass has Focused on are:
- ManageEngine Desktop Central Vulnerabilities
- Microsoft Exchange Zero Days
- CVE-2023-42659 – WS_FTP unrestricted File Upload
- CVE-2023-22518 – Atlassian Confluence Data Center improper authorization
- CVE-2023-47246 – SysAid unknown path traversal to RCE
The Key Malwares and Threat Actors that FireCompass has Focused on are:
- CVE-2023-22518- Atlassian – Confluence Data Center and Server
- CVE-2023-46604 – Apache ActiveMQ
- CVE-2019-0708 – Microsoft Remote Desktop Services
- CVE-2023-47246 – SysAid unknown path traversal to RCE
-> Hackers Won't Wait For Your Next Pen Test: Know Automated Continuous Pen Test
Know The Vulnerabilities Impacting Key Industries and Companies:
ManageEngine Desktop Central Vulnerabilities
ManageEngine Desktop Central lets users automate regular endpoint management. This week it released three vulnerabilities affecting version 9.1.0. Here are the three vulnerabilities.
- CVE-2023-4767 – This vulnerability could allow a remote attacker to inject arbitrary HTTP headers and perform HTTP response splitting attack.
- CVE-2023-4768 – This vulnerability could allow a remote attacker to inject arbitrary HTTP headers and perform HTTP response splitting attack.
- CVE-2023-4769 – This vulnerability could allow an authenticated attacker to launch targeted attacks, such as a cross-port attack, service enumeration and other attacks via HTTP requests.
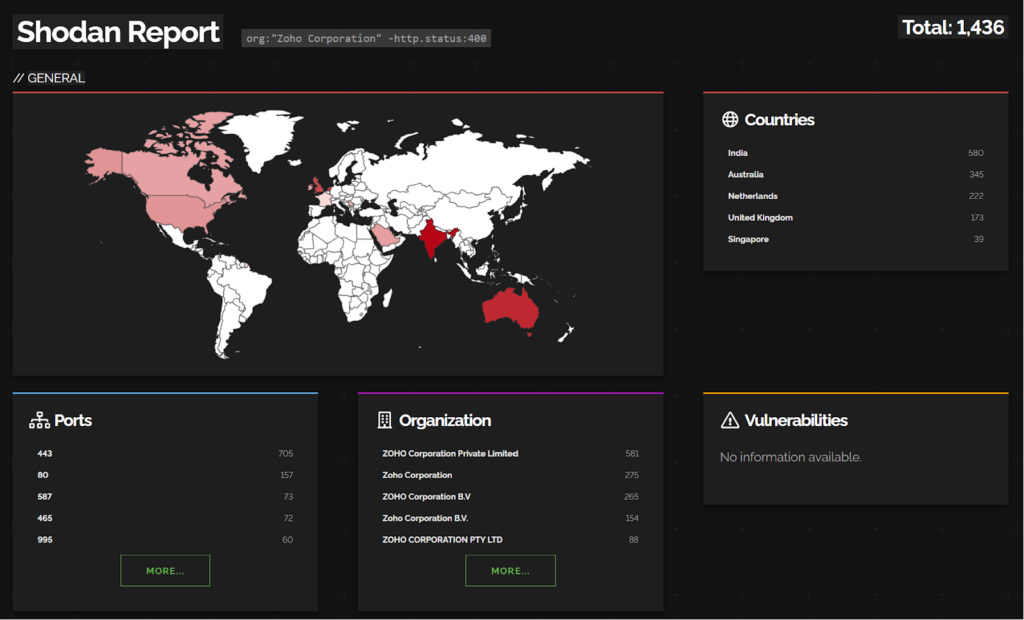

Microsoft Exchange Zero Days
The Zero Day Initiative released four 0days for Microsoft Exchange, the CVEs are not officially released yet but here are the ZDIs for the vulnerabilities.
- ZDI-23-1581 – Microsoft Exchange Create Attachment From Uri Server-Side Request Forgery Information Disclosure Vulnerability.
- ZDI-23-1580 – Microsoft Exchange Download Data From Office Market Place Server-Side Request Forgery Information Disclosure Vulnerability.
- ZDI-23-1579 – Microsoft Exchange Download Data From Uri Server-Side Request Forgery Information Disclosure Vulnerability.
- ZDI-23-1578 – Microsoft Exchange Chained Serialization Binder Deserialization of Untrusted Data Remote Code Execution Vulnerability.

>> Find Critical Risks in 72 Hours & Continuous Risk Hunting (Request Demo)
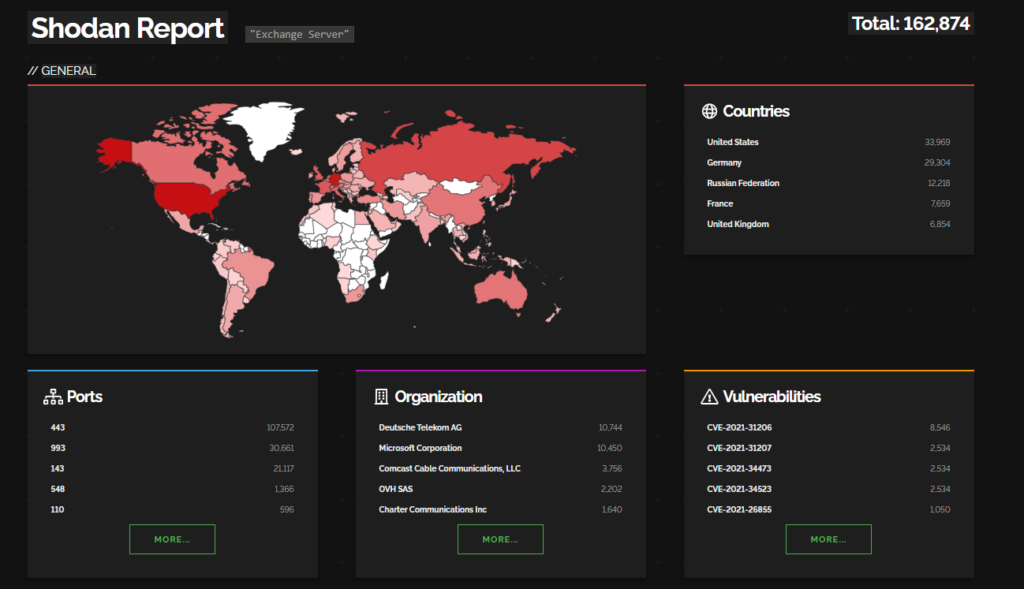
CVE-2023-42659 – WS_FTP Unrestricted File Upload
Progress product WS_FTP has been exploited by ransomware and malwares in 2023, this week it released a CVE where WS_FTP version prior to 8.7.6 and 8.6.4 which is vulnerable to an unrestricted file upload An authenticated Ad Hoc Transfer user has the ability to craft an API call which allows them to upload a file to a specified location on the underlying operating system hosting the WS_FTP Server application.
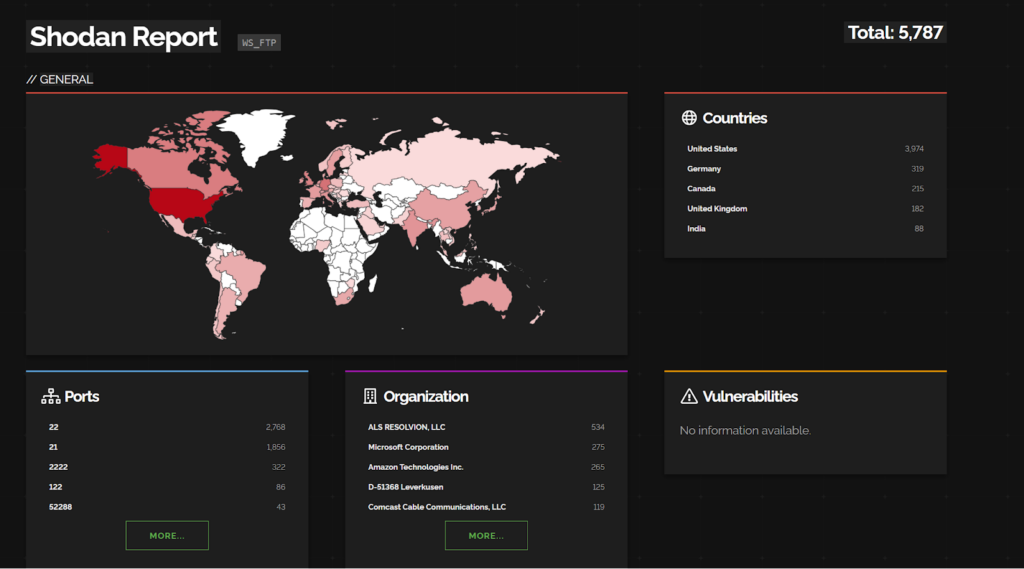

CVE-2023-22518 – Atlassian Confluence Data Center Improper Authorization
Atlassian Confluence Data Center and Server has improper authorization which allows an unauthenticated attacker to reset Confluence and create a Confluence instance administrator account. Using this account, an attacker can then perform all administrative actions that are available to Confluence instance administrators leading to – but not limited to – full loss of confidentiality, integrity and availability.
This CVE has been listed in CISA exploited in the wild list for this week.

>> [Request RECON Demo] - Reconnaissance Techniques As Threat Actors
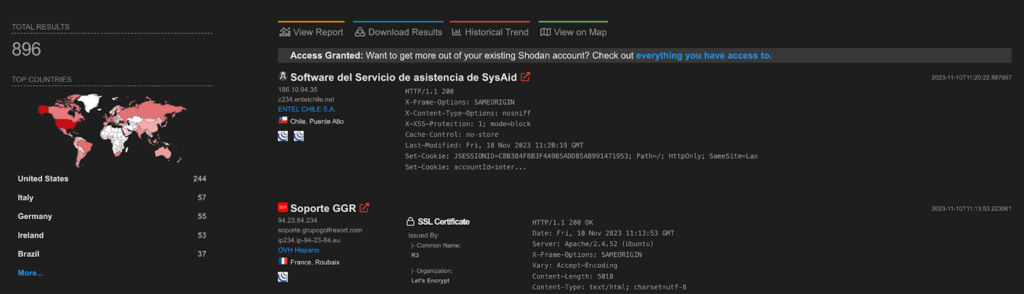
CVE-2023-47246 – SysAid unknown path traversal to RCE
CVE-2023-47246 is a critical vulnerability in SysAid On-Premise before 23.3.36. It is a path traversal vulnerability that allows an attacker to upload and access WAR file webshells and other payloads in the webroot of the SysAid Apache Tomcat web server. This could allow the attacker to execute arbitrary code on the server.
The vulnerability exists in the way that SysAid handles file uploads. An attacker can exploit the vulnerability by crafting a malicious file upload request that includes a specially crafted path. If the request is successful, the attacker will be able to upload a file to the webroot of the SysAid web server.
The POC of the above vulnerability can be found here: https://www.huntress.com/blog/critical-vulnerability-sysaid-cve-2023-47246
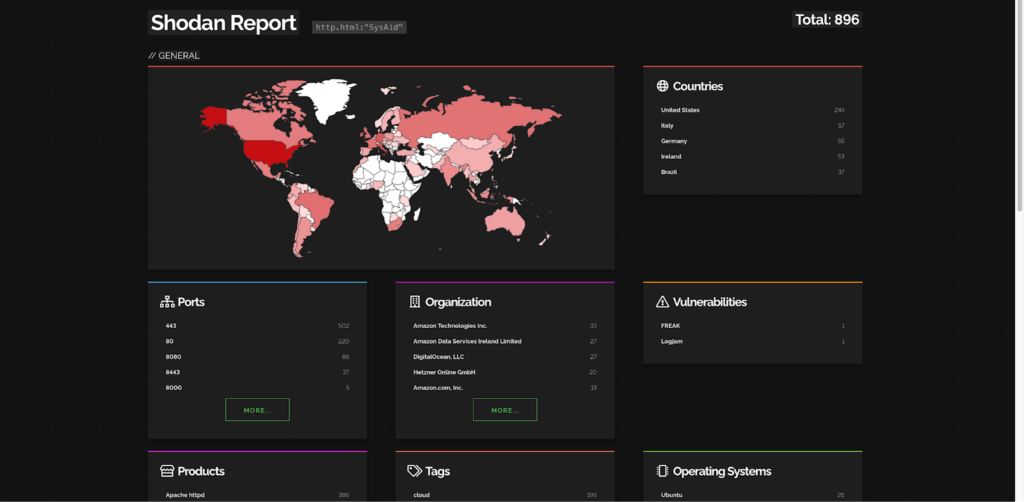

-> [Request Demo] - Get the Hacker’s View Of Your Attack Surface
Know The Threat Actors Impacting Key Industries and Companies:
CVE-2023-22518- Cerber ransomware
Confluence Data Center and Server are affected by an Improper Authorization bypass unexploited vulnerability. There is no impact to confidentiality as an attacker cannot exfiltrate any instance data. Atlassian Cloud sites are not affected by this vulnerability. This vulnerability was found to be exploited by Cerber ransomware in order to encrypt files in the victim machine.
The POC of the above vulnerability can be found here: https://github.com/RootUp/PersonalStuff/blob/master/check_cve_2023_22518.py
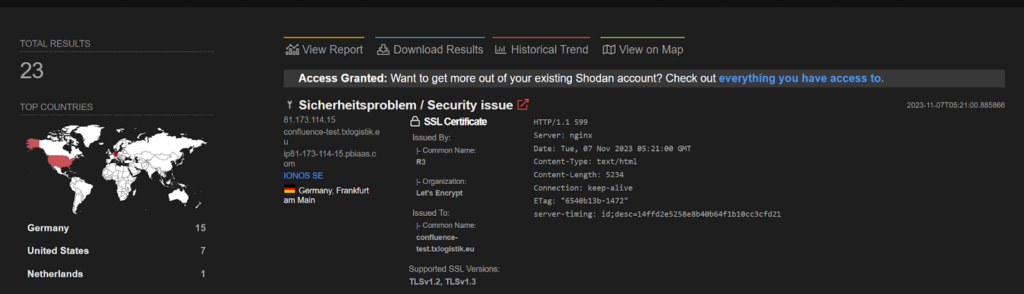

CVE-2023-46604 – TellYouThePass ransomware
Apache ActiveMQ is vulnerable to Remote Code Execution. The vulnerability may allow a remote attacker with network access to a broker to run arbitrary shell commands by manipulating serialized class types in the OpenWire protocol to cause the broker to instantiate any class on the classpath. This vulnerability was found to be exploited by a ransomware group named, TellYouThePass ransomware.
The POC of the above vulnerability can be found here: https://github.com/SaumyajeetDas/CVE-2023-46604-RCE-Reverse-Shell-Apache-ActiveMQ
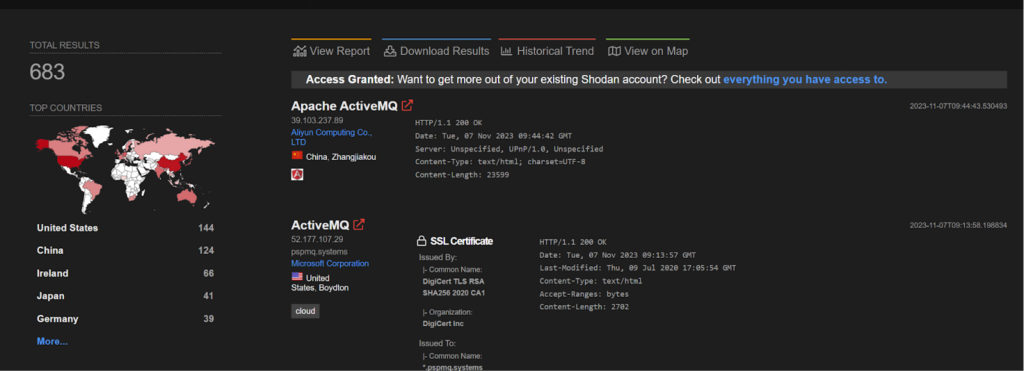

>> (Learn More) "Automated Pen Testing Significantly Improved The Depth & Breadth Of Testing" - Ed Adams, Security Innovation
CVE-2019-0708 – Kimsuky
A remote code execution vulnerability exists in Remote Desktop Services formerly known as Terminal Services when an unauthenticated attacker connects to the target system using RDP and sends specially crafted requests, aka ‘Remote Desktop Services Remote Code Execution Vulnerability’. This vulnerability was found to be exploited by a North Korean state backed hacker group named, Kimsuky.
The POC of the above vulnerability can be found here: https://packetstormsecurity.com/files/162960/Microsoft-RDP-Remote-Code-Execution.html
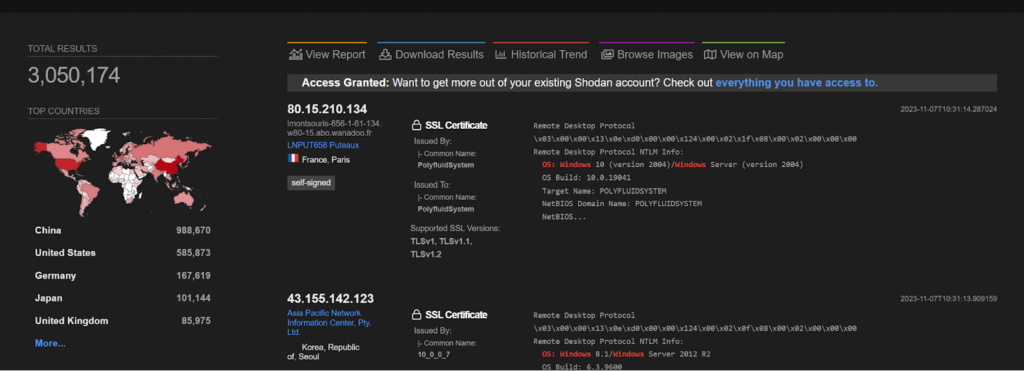

CVE-2023-47246 – DEV-0950 (Lace Tempest)
DEV-0950 (Lace Tempest) is actively exploiting CVE-2023-47246, a path traversal vulnerability in SysAid On-Premise before 23.3.36. This vulnerability allows an attacker to upload and access WAR file webshells and other payloads in the webroot of the SysAid Apache Tomcat web server. This could allow the attacker to execute arbitrary code on the server.
Lace Tempest is a known ransomware group, so it is likely that they are exploiting CVE-2023-47246 to deploy ransomware on affected systems.
The POC of the above vulnerability can be found here: https://www.huntress.com/blog/critical-vulnerability-sysaid-cve-2023-47246

-> (Request Demo) 10 X Pen Testing Frequency & 100% Asset Coverage
By: Firecompass Research Team – Debdipta Halder, Soumyanil Biswas, Faran Siddiqui, Anirban Bain
About FireCompass:
FireCompass is a SaaS platform for Continuous Automated Pen Testing, Red Teaming and External Attack Surface Management (EASM). FireCompass continuously indexes and monitors the deep, dark and surface webs using nation-state grade reconnaissance techniques. The platform automatically discovers an organization’s digital attack surface and launches multi-stage safe attacks, mimicking a real attacker, to help identify breach and attack paths that are otherwise missed out by conventional tools.
Feel free to get in touch with us to get a better view of your attack surface.


