Critical CVEs And Active Threats: Apache Kafka-Ui, Ivanti Multiple Product, J-Web of Juniper Networks Junos OS and More
This week from January 29th to February 02nd, FireCompass research team identified a huge number of CVEs that are high in severity and ransomware, botnets, and threat actors creating havoc. Some of the CVEs identified are popular commercial products used by various industries and some new & well-known malware targeting industries for this week. In this, we will list important CVEs discovered as well as list of malware, threat actors and botnets which were most active along with the CVEs that they were using in their campaigns.
List of Critical Vulnerabilities That Were Exploited – FireCompass Research :
- CVE-2023-52251 – Apache Kafka-Ui
- CVE-2024-21620 – J-Web of Juniper Networks Junos OS
- CVE-2024-21893 – Ivanti Multiple Product
-> Hackers Won't Wait For Your Next Pen Test: Know Automated Continuous Pen Test
Detailed Analysis: Vulnerabilities
CVE-2023-52251 – Apache Kafka-Ui
CVE-2023-52251 is a critical vulnerability in versions 0.4.0 through 0.7.1 of the Apache Kafka user interface “kafka-ui” that allows remote attackers to take complete control of affected systems. This is possible because attackers can manipulate a specific parameter within the software’s code, enabling them to execute any malicious code they desire. As of now, there is no patch available, but the vendor has been notified. If you are using a vulnerable version of kafka-ui, it is crucial to take immediate steps to mitigate the risk, such as restricting access to the web interface and implementing additional security measures.
POC – https://github.com/BobTheShoplifter/CVE-2023-52251-POC
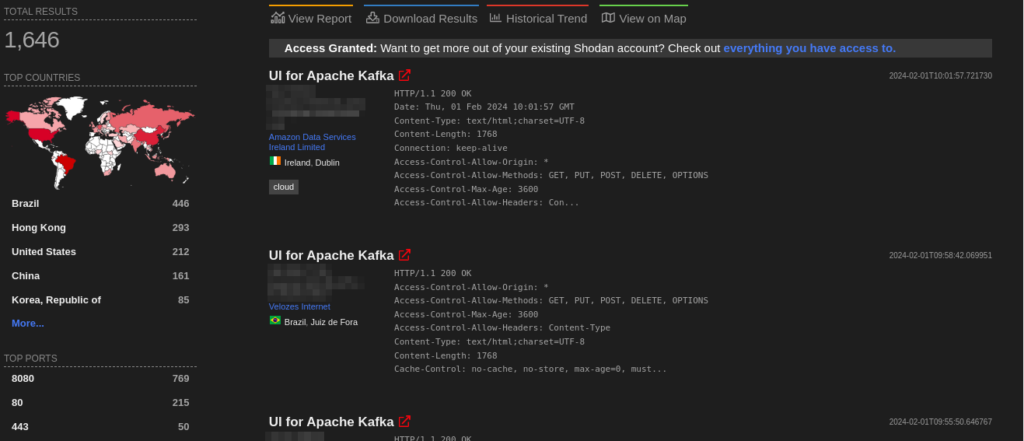
A total of more than 1500 endpoints of Apache Kafka-Ui are exposed on the Shodan.
CVE-2024-21620 – J-Web of Juniper Networks Junos OS
J-Web, a component of Juniper Networks Junos OS on SRX and EX Series devices, contains a critical security flaw (CVE-2024-21620) that allows attackers to craft malicious URLs. Clicking such a link grants them full control over the victim’s device, including administrator privileges, by exploiting a weakness in how J-Web handles user input. This vulnerability affects all Junos OS versions before 20.4R3-S10, 21.2R3-S8, 21.4R3-S6, 22.1R3-S5, 22.2R3-S3, 22.3R3-S2, 22.4R3-S1, 23.2R2, and 23.4R2. Upgrading to these patched versions immediately is essential to safeguard your devices.
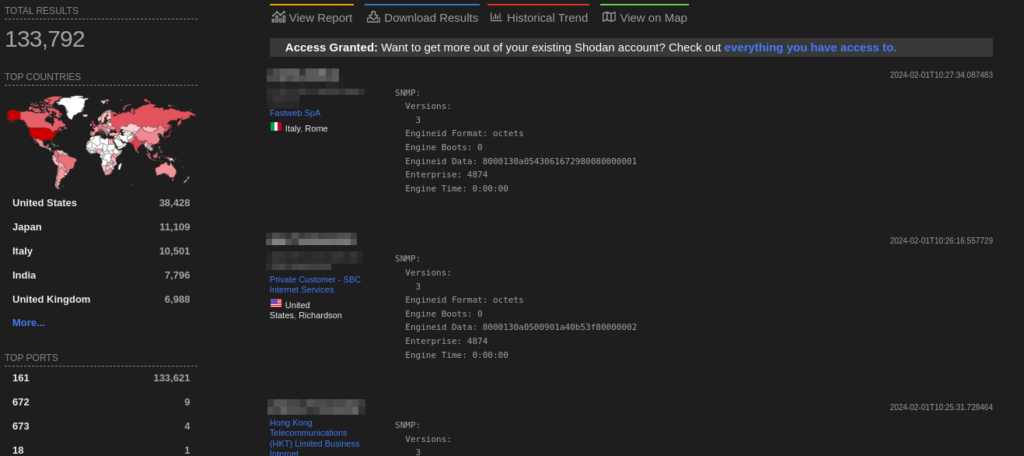
A total of more than 133k endpoints of Juniper Networks are exposed on the Shodan.
>> Find Critical Risks in 72 Hours & Continuous Risk Hunting (Request Demo)
CVE-2024-21893 – Ivanti Multiple Product
An unpatched vulnerability (CVE-2024-21893) exists in Ivanti Connect Secure, Policy Secure, and Neurons for ZTA versions 9.x and 22.x. This vulnerability allows attackers to bypass authentication and access restricted resources within the system. The vulnerability resides in the SAML component and is classified as a server-side request forgery, meaning attackers can potentially trick the server into performing unauthorized actions. It’s crucial to update affected systems immediately to mitigate the risk of unauthorized access and potential compromise.
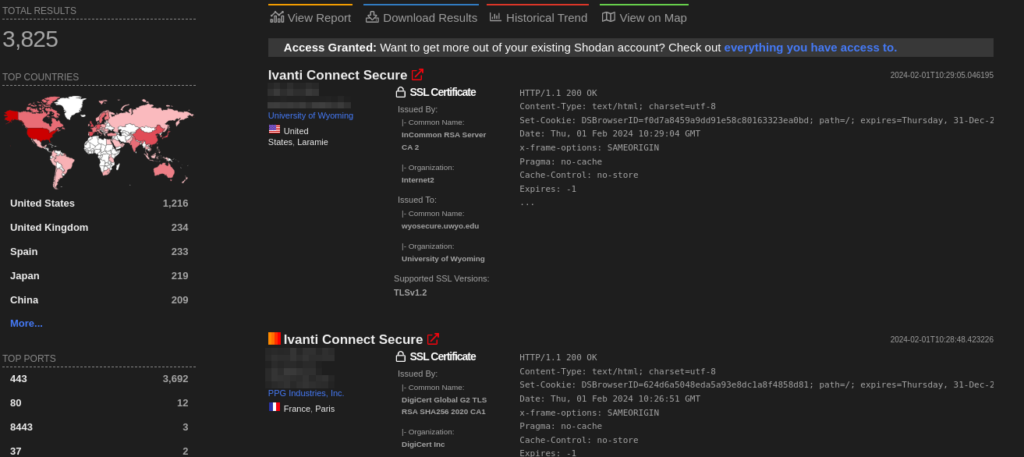
A total of more than 3.5k endpoints of Ivanti are exposed on the Shodan.
Author: Debdipta Halder
Assisted By: Soumyanil Biswas, Faran Siddiqui, Anirban Bain
About FireCompass:
FireCompass is a SaaS platform for Continuous Automated Pen Testing, Red Teaming and External Attack Surface Management (EASM). FireCompass continuously indexes and monitors the deep, dark and surface webs using nation-state grade reconnaissance techniques. The platform automatically discovers an organization’s digital attack surface and launches multi-stage safe attacks, mimicking a real attacker, to help identify breach and attack paths that are otherwise missed out by conventional tools.
Feel free to get in touch with us to get a better view of your attack surface.




