Ransomware Attacks are increasing globally. The attacks are more targeted and hackers are using modern and sophisticated techniques to achieve their goals. Organizations must have a clear view to their attack surface and an in-depth understanding of adversary behaviour, regularly validate susceptibility of organisations systems against attacks, while testing efficacy of the defensive controls. One must remember that Ransomware attacks mostly use well known attack channels like Phishing and RDP ports to exploit.
The FBI has been warning organizations that hackers are increasingly abusing Remote desktop protocol (RDP) connections. This is still a widely used application and RDP does not use strong authentication schemes. With the majority of organizations moving to work from home, the number of exposed RDP ports suddenly increased in Shodan. Though RDP can be exploited in different ways, attackers tend to rely onRDPs that are already exposed. As per Cyware, RDP is the most common intrusion method used by threat actors for most ransomware attacks in 2020 to gain access to windows computers and install malware.
"RDP is the most common intrusion method used by threat actors – for most ransomware attacks in 2020"
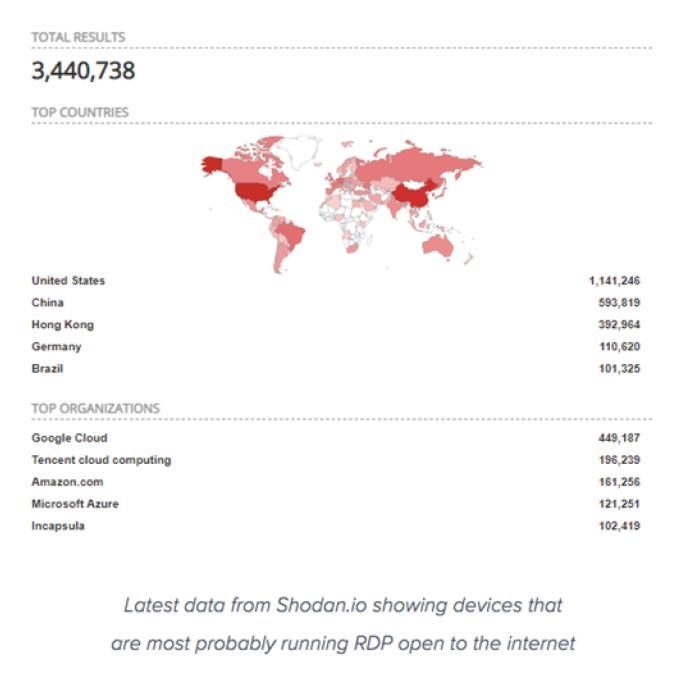
As per Avast, the most notorious failures, however, occur when the RDP access is opened to the whole internet (specifically, port 3389). If the security settings at either endpoints are misconfigured, it leaves a doorway for interceptors to find and hack into the targeted machine.
Why RDP Tops the Chart for Ransomware Attacks?
"There are millions of systems with RDP ports exposed online, and this makes RDP a great attack vector for ransomware operators"
Ransomware Attacks Through Exposed RDP Ports
Ransomware can enter your network through a variety of ways, however, utilizing exposed RDP is one of the favorites for a hacker for launching ransomware attacks. The steps below explains the anatomy of a Ransomware Attack using exposed RDP ports.
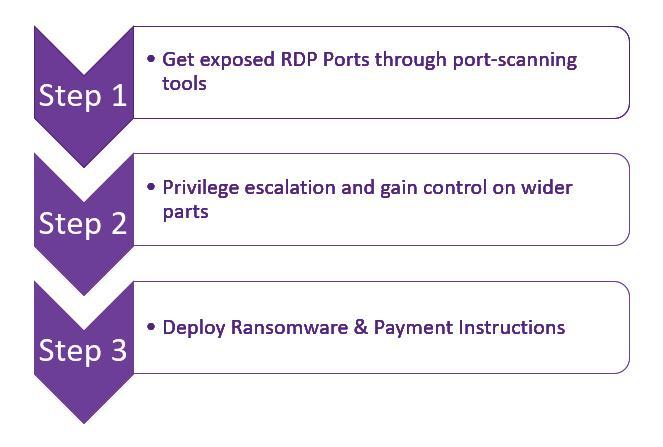
Step 1 (Get exposed RDP Ports through port-scanning tools):
They use open source port-scanning tools to scan & gather exposed RDP ports online and then try to gain access to a system using social engineering or brute-force tools or through stolen credentials from the dark web.
Step 2 (Privilege escalation and gain control on wider parts):
Once the attackers gain access to one system of the target, they make the network vulnerable by disabling antivirus software or changing configuration settings etc.
Step 3 (Deploy Ransomware & Payment Instructions):
After disabling the security systems attackers deliver malware payloads by installing ransomware, using infected machines to distribute spam, deploying keyloggers, or installing backdoors to be used for future attacks.
Recommendations to avoid attacks
- Reconnaissance: Implement tools that will conduct reconnaissance on a continuous basis like ransomware actors to discover your exposed services like RDP, FTP servers and other ports which are commonly exploited
- Test your Security Defenses: Test the current state of security preparedness and effectiveness from the perspective of your security defense tools. Tools like FireCompass will help in continuous testing with advanced simulation of hacking attempts on your digital attack surface
- Continuous Attack Surface Monitoring: Implement tools that will continuously monitor the digital attack surface.



